Validin YARA detection now runs across live host responses
Takeaways
- Validin YARA detection now runs across live host data
- Rule versioning and Projects enable fast, collaborative threat hunting
- ClickFix case study - live detection of HTML and JavaScript-based threats
Summary and Outcomes
Earlier this year, we introduced YARA rule hunting across Validin’s virtual host response data that allows analysts to scan historical host responses using their own detection logic.
We’re excited to announce that Validin’s YARA engine now runs continuously on live data, as it arrives.
With continuous execution, rule versioning, and contextual visibility, YARA in Validin now operates as a live detection layer across our vast virtual host response dataset.
The updates enable security teams to track infrastructure in near-realtime as adversaries adjust their attack vectors to avoid detection, keep in step with changes in attacker TTPs, and bridge the gap between receiving raw intelligence and detecting threats specific to their area of operation.
Key outcomes:
- Enhanced triage - detect new or recycled infrastructure in hours, not days
- Improved efficiency - refine detection logic whilst retaining historical context
- Minimize risk - contain threats before they propagate across hosting clusters
- Execute trend analysis, once a threat has been identified and contained
How We Do It: Native YARA-X Integration
Behind the scenes, Validin processes over 5TB and 850 million (100 million unique) host responses every day.
That’s a LOT of data to make sense of… for us and our users.
To make this possible, we developed a custom integration with YARA-X - the next-generation version of YARA created by VirusTotal.
YARA’s first incarnation was focused on file-based malware detection. YARA-X modernizes the engine in a way that facilitates internet-scale CTI data processing, giving Validin the ability to operationalize YARA detection logic for our users in a fast and reliable way.
On top of that, we’ve built our integration to be immediately conversant with the unique way Validin collects and stores data, enabling scale and efficiency for widescale adoption by our customer base, while maintaining deep context on each and every matching indicator.
From Retrospective to Continuous Detection
Our YARA functionality already enables large-scale retroactive searches. With this update, those same rules now operate as live monitors that alert the moment new matches appear.
Each rule execution is timestamped, showing exactly when Validin captured the response that triggered the match.
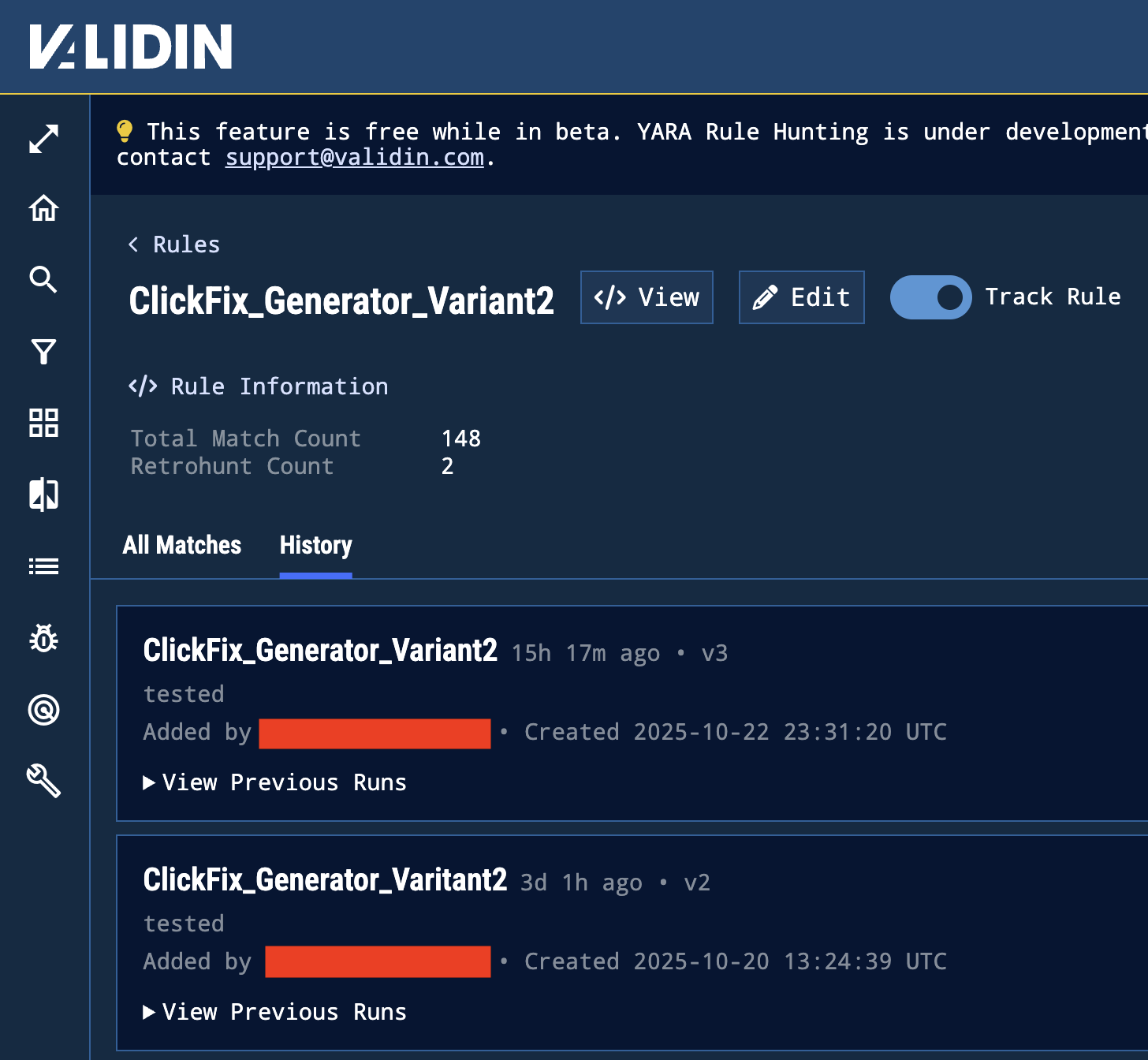
Figure 1. Different versions of the same YARA rule
The Retrohunt Count shows how many times a rule has been executed across past datasets and gives analysts a clear view of a rule’s reach in a given dataset.
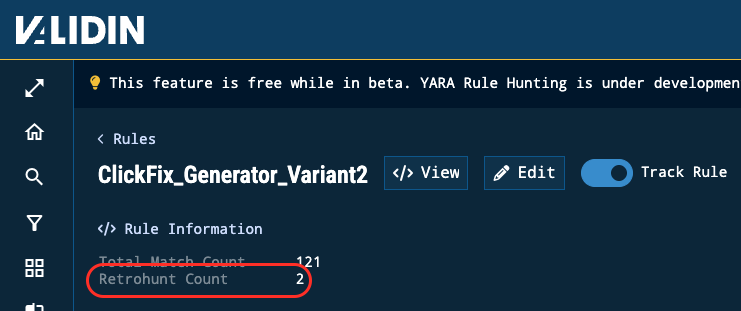
Figure 2. Retrohunt Count
Key advantages of continuous detection:
- Rules execute automatically over live data.
- Matches are timestamped and enriched with context for precise infrastructure tracking.
- Analysts can monitor new matches in real time.
- No need for manual retro hunts or scheduled scans.
Enhanced YARA Rule Editing and Testing
As Validin’s dataset scales beyond 850 million host responses collected daily, precision and manageability are critical.
The new YARA playground lets analysts test their rules, before running on Validin’s dataset. It’s used to create or edit a rule and allows for testing against an arbitrary text document.
This allows analysts to verify, debug, and refine their rules before ever needing to launch a hunt.
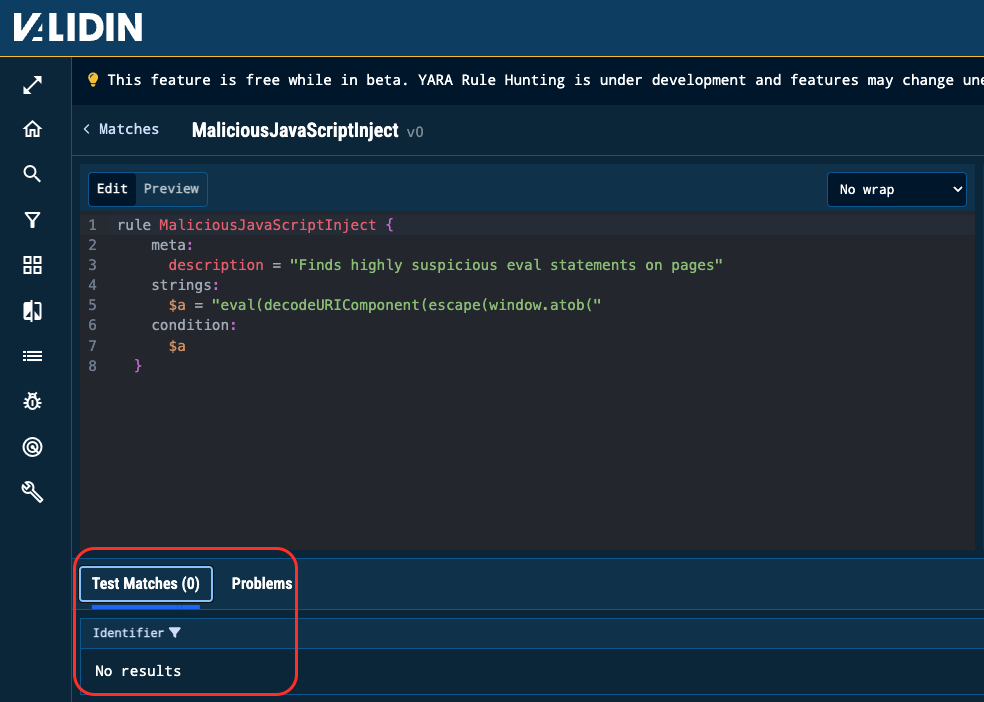
Figure 3. Validin’s YARA editing environment
In conjunction, we’ve introduced a new rule versioning feature that lets analysts maintain multiple syntax variations of the same rule and execute them directly from a drop-down menu.
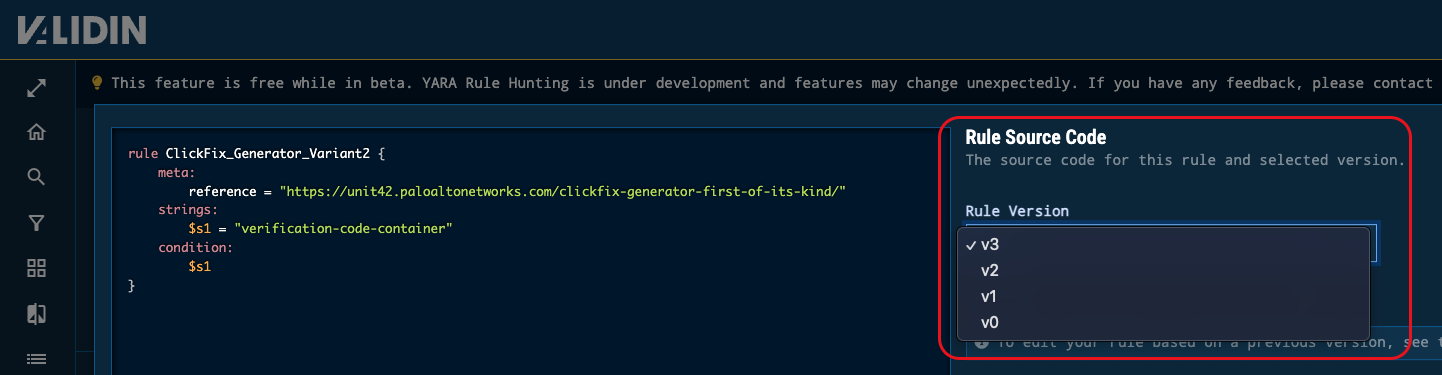
Figure 4. Selecting different versions of the same rule
Each rule version retains its own record, making it easy to test refinements, roll back to earlier logic, or reproduce past detections.
Enhancements in this release:
- A rich YARA playground supporting editing and testing.
- Rule versioning with selectable syntax variants.
- Separate run histories for each version, to support audits.
YARA Searches in Collaborative Workspaces
YARA rules are created and stored within Projects, Validin’s central workspace for collaborative threat investigations.
Projects unite data, alerts, and detection logic in a single view, keeping teams aligned on shared targets and notable infrastructure.
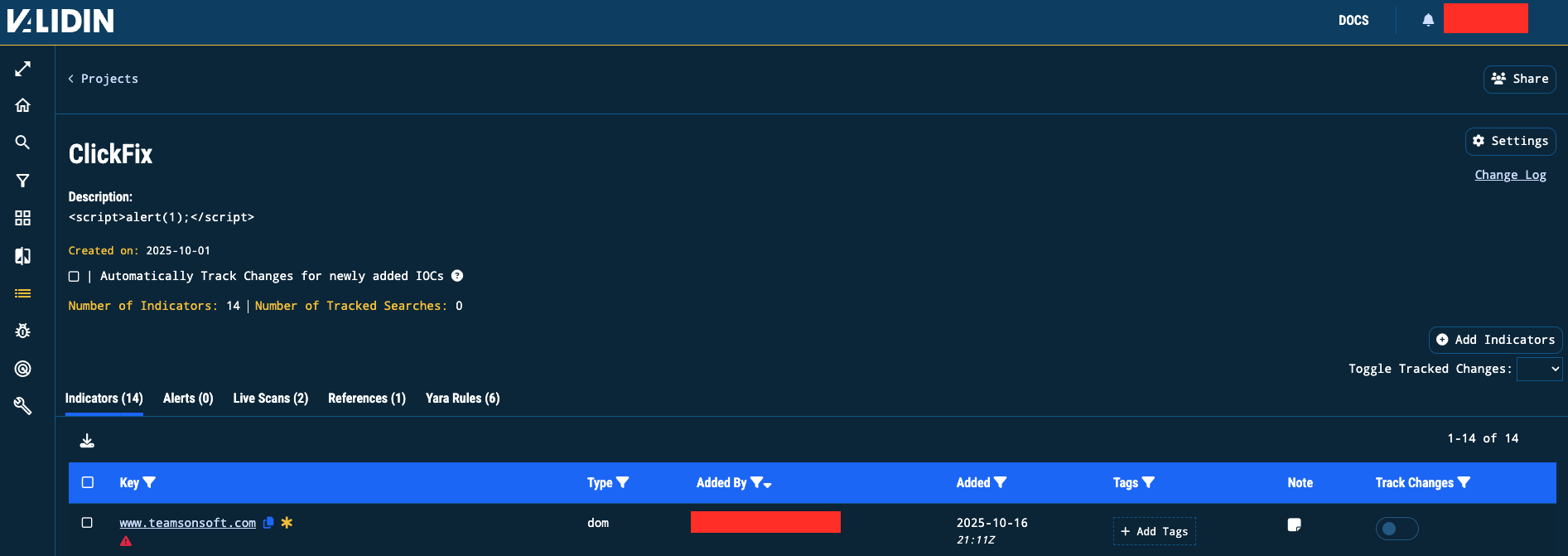
Figure 5. Validin Projects screen
Within each project, analysts can view:
- Indicators - enriched observables in a table view with filters, grouping, and timestamps.
- Alerting - notifications based on rule matches or infrastructure changes.
- Live scans - DNS resolutions, recursive resolutions, host connections, and host responses.
- YARA rules - with version histories and continuous run logs.
This structure keeps scanning, detection, and collaboration in sync. Analysts can easily pivot directly from a YARA match to historic DNS or host responses, allowing teams to focus on threats rather than wrestling with multiple toolsets.
A slide-out menu on returned datasets within a Project also displays virtual host responses for each match, allowing direct inspection of HTML, certificate details, and other key context without leaving the results view.
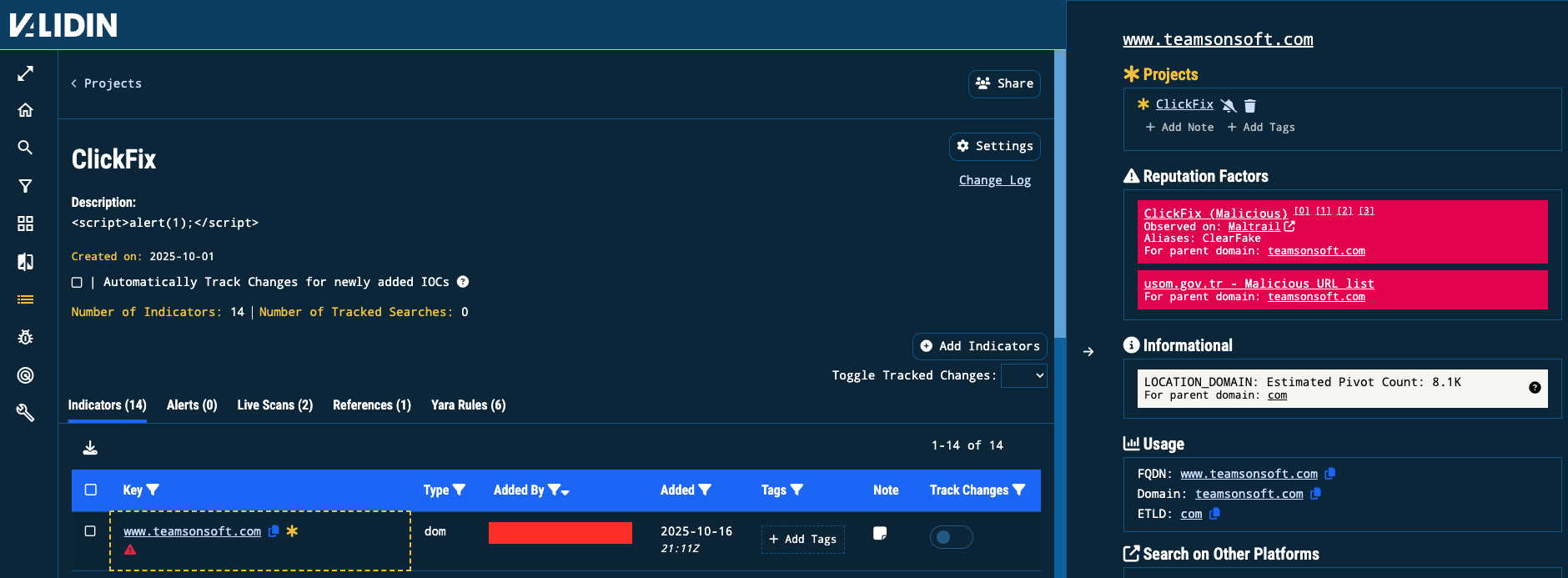
Figure 6. Virtual host details in the Projects space
Case Study: Detecting ClickFix and Malicious Script Injections
To demonstrate the expanded capability, we recreated detections first reported by Palo Alto Networks’ Unit 42, who discovered the ClickFix malware generator dubbed “IUAM” - a campaign that uses HTML templates to inject JavaScript payloads that capture credentials.
The following rule tests detection logic for a ClickFix variant, searching for the CMD+R command that was present in the ClickFix instructions.
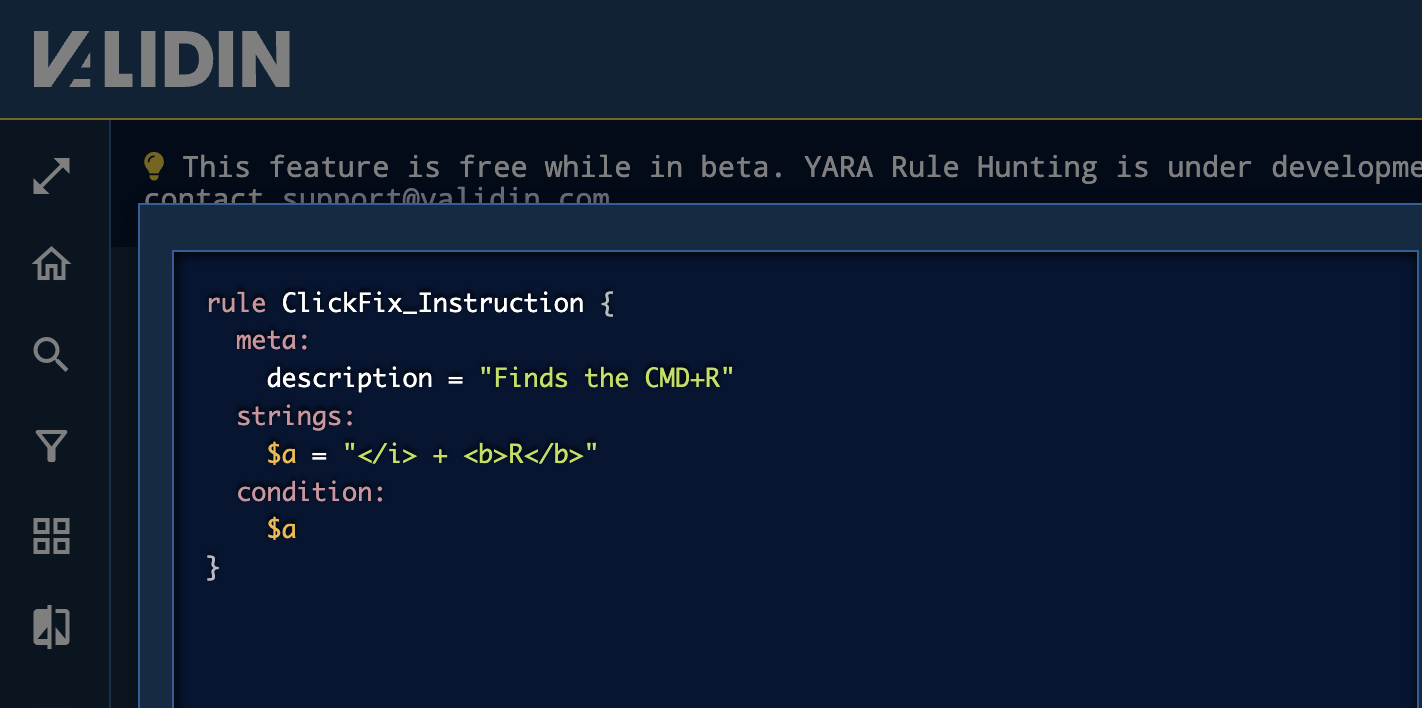
Figure 7. YARA rule targeting ClickFix Instructions
The rule returned 575 matches over 1 day. Most were domains hosting cloned verification or authentication templates and many have already been flagged as ClickFix on the Validin Platform.
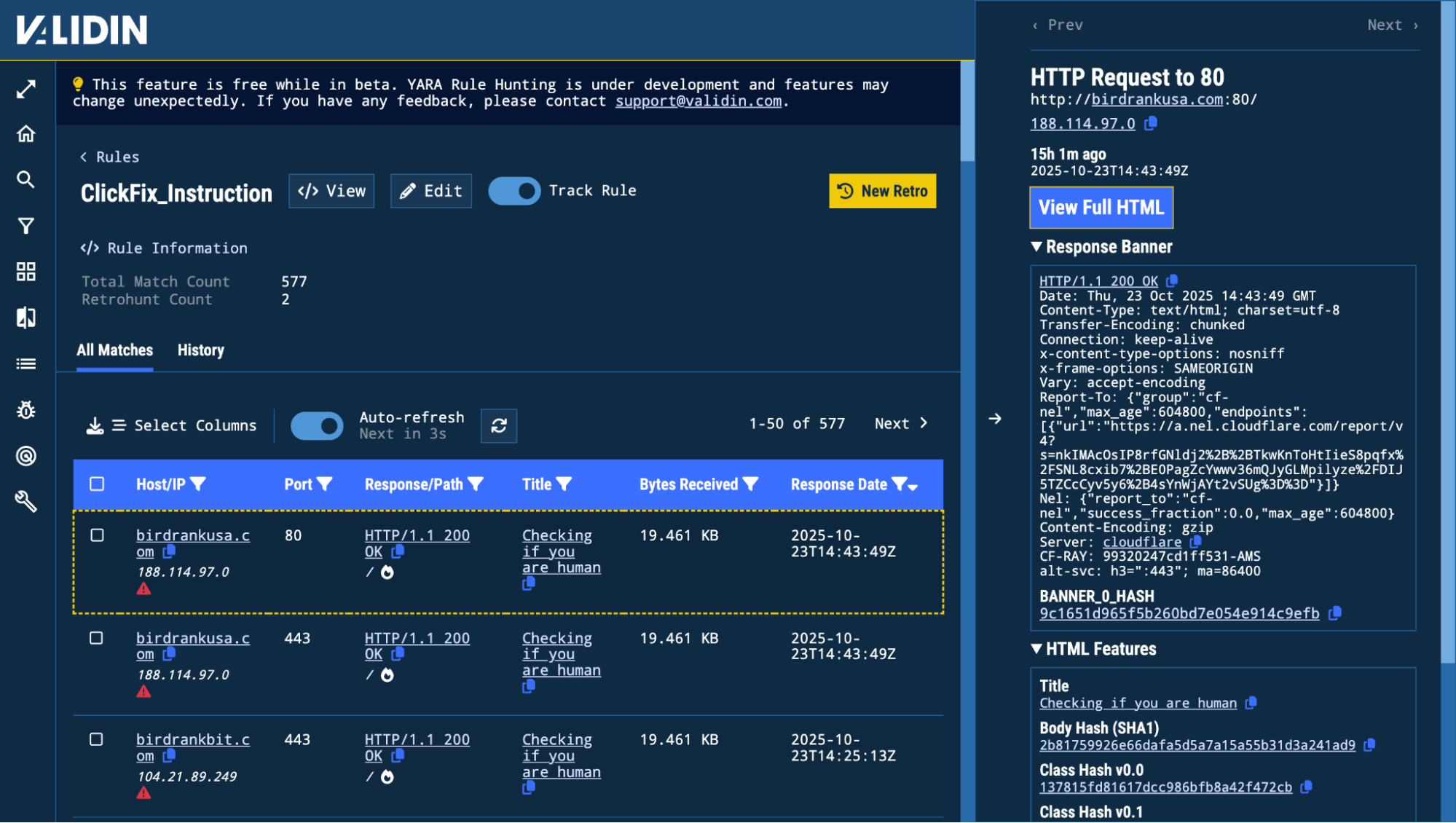
Figure 8. Tabulated matches with slide-out data
Because the rule runs continuously, the platform timestamps each match as new domains appear, showing how the ClickFix infrastructure evolves in near real time.
We then applied a second rule targeting obfuscated JavaScript injections often seen in similar campaigns:
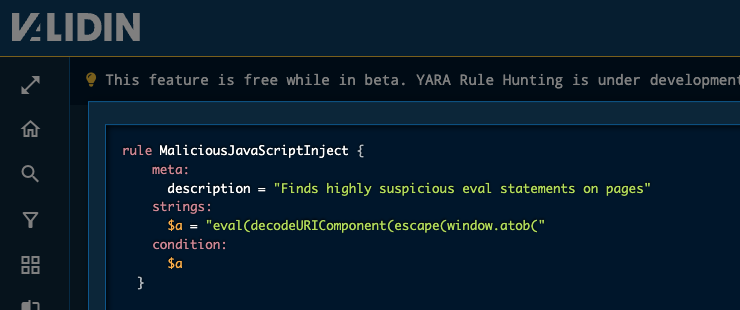
Figure 9. YARA rule targeting ClickFix JavaScript
This rule produced 2,213 indicator matches over 3 days, revealing encoded scripts inside otherwise benign landing pages.
Analysts can review the matching HTML response and response summary directly within a slide-out view.
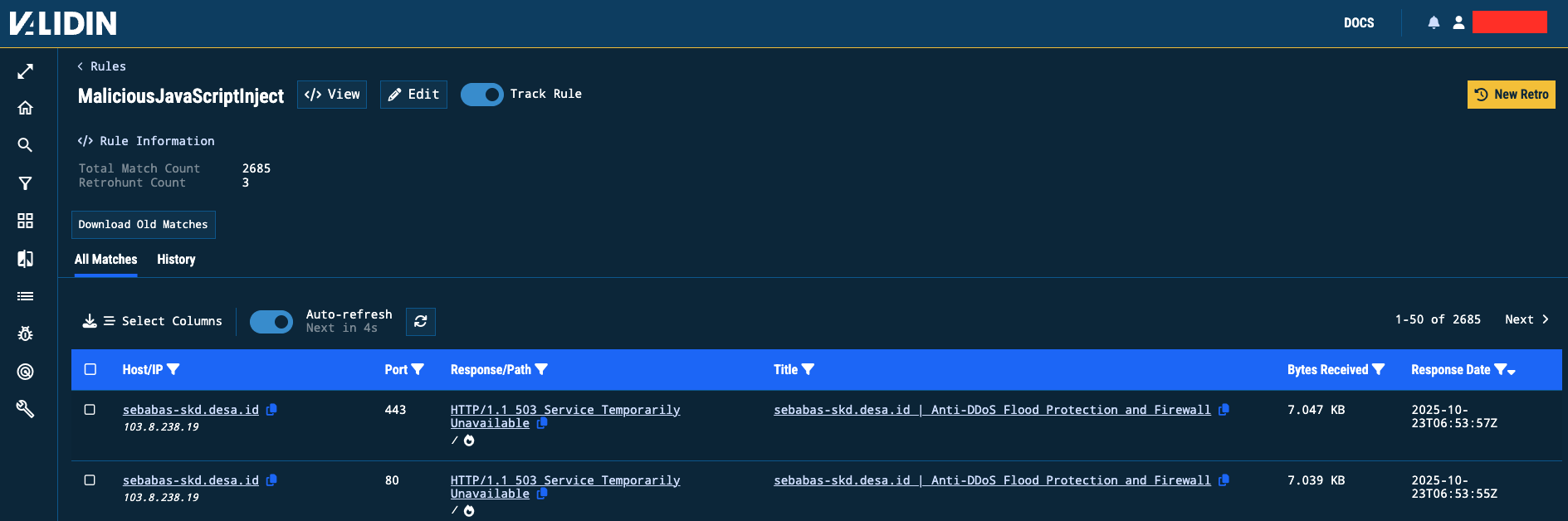
Figure 10. Tabulated matches with the ability to expand details into a slide-out view.
Summary of results:
- ClickFix rule matches based on Unit42 report: 575 verified results over 1 day.
- JavaScript injection rule matches: 2,213 indicators over 3 days.
- Findings verified via host response and full HTML inspection.
Both rules were managed and monitored within a single Validin project, allowing the team to track indicators, alerts, and host responses from one collaborative workspace.
Request A Demo
Validin’s mission is to provide the most complete and actionable view of attacker infrastructure available anywhere in the world.
With continuous YARA detection, collaborative project workflows, and deep response visibility, analysts can begin to move beyond retrospective hunting into real-time threat discovery.
Contact us to learn more about executing YARA searches in Validin Enterprise.