Takeaways
- Validin is introducing JA4+ capabilities, starting with JA4X available to Community and Enterprise users
- JA4X enables detection of structural anomalies in X.509 certificates
- JA4X can be used to uncover and track malicious C2 infrastructure
A New Way to Search Certificates Within Validin
Validin is excited to announce support for JA4X fingerprints, effective immediately. JA4X is a fingerprinting technique that enables users to better identify anomalies in web certificates. Validin processes around 400 million certificates a day, both from our own active crawling and by monitoring the Certificate Transparency stream. In this blog, we’ll quickly cover what the JA4X fingerprint represents and useful pivots for this data within Validin.
What is JA4+?
JA4+ is a suite of fingerprinting techniques developed by John Althouse (the creator of JARM) and the team at FoxIO to fingerprint different types of internet infrastructure. Validin is working to integrate this capability in the platform quickly, and the JA4X fingerprint is immediately available as the first of the JA4+ suite coming to Validin.
What is a JA4X Fingerprint?
A JA4X fingerprint mathematically represents three separate hashes concatenated to uniquely identify three aspects of a certificate: the issuer RDN, the subject RDN and the extensions. The goal of the JA4X fingerprint is not to identify the content of the certificate, but to fingerprint how the certificates were generated. Each component is derived from the first 12 characters of a SHA-256 hash of the ordered keys for the issuer RDN, subject RDN, and certificate extensions.
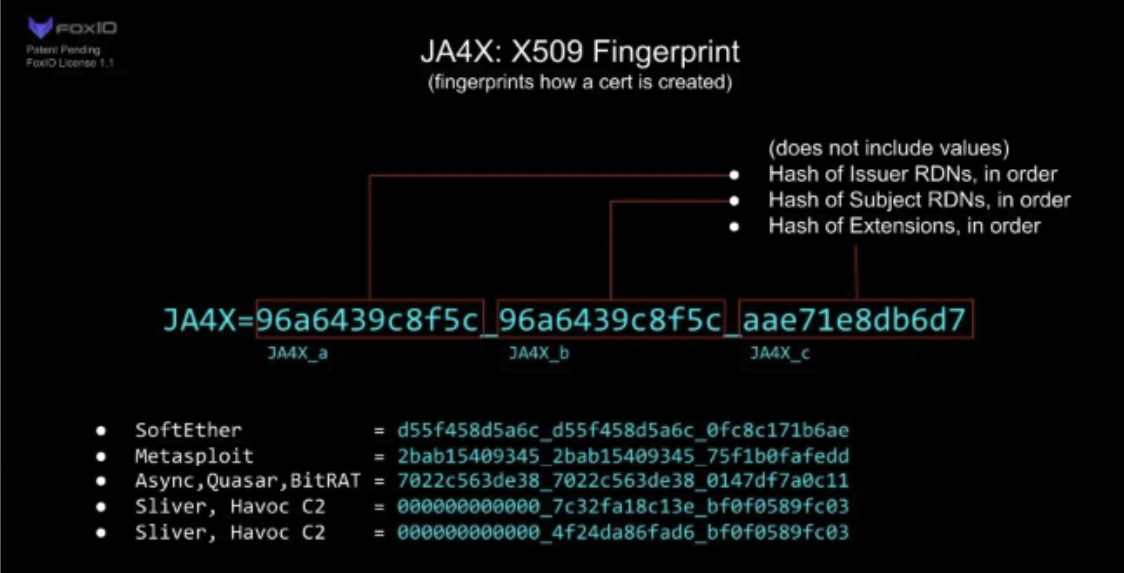
Find more information about JA4X and JA4+, read the write-up from FoxIO here
Where is JA4X in Validin?
Starting with host responses collected after January 13th, you can find a collected certificate’s JA4X fingerprint in two places:
1. The slideout of the entries within the “Host Responses" tab
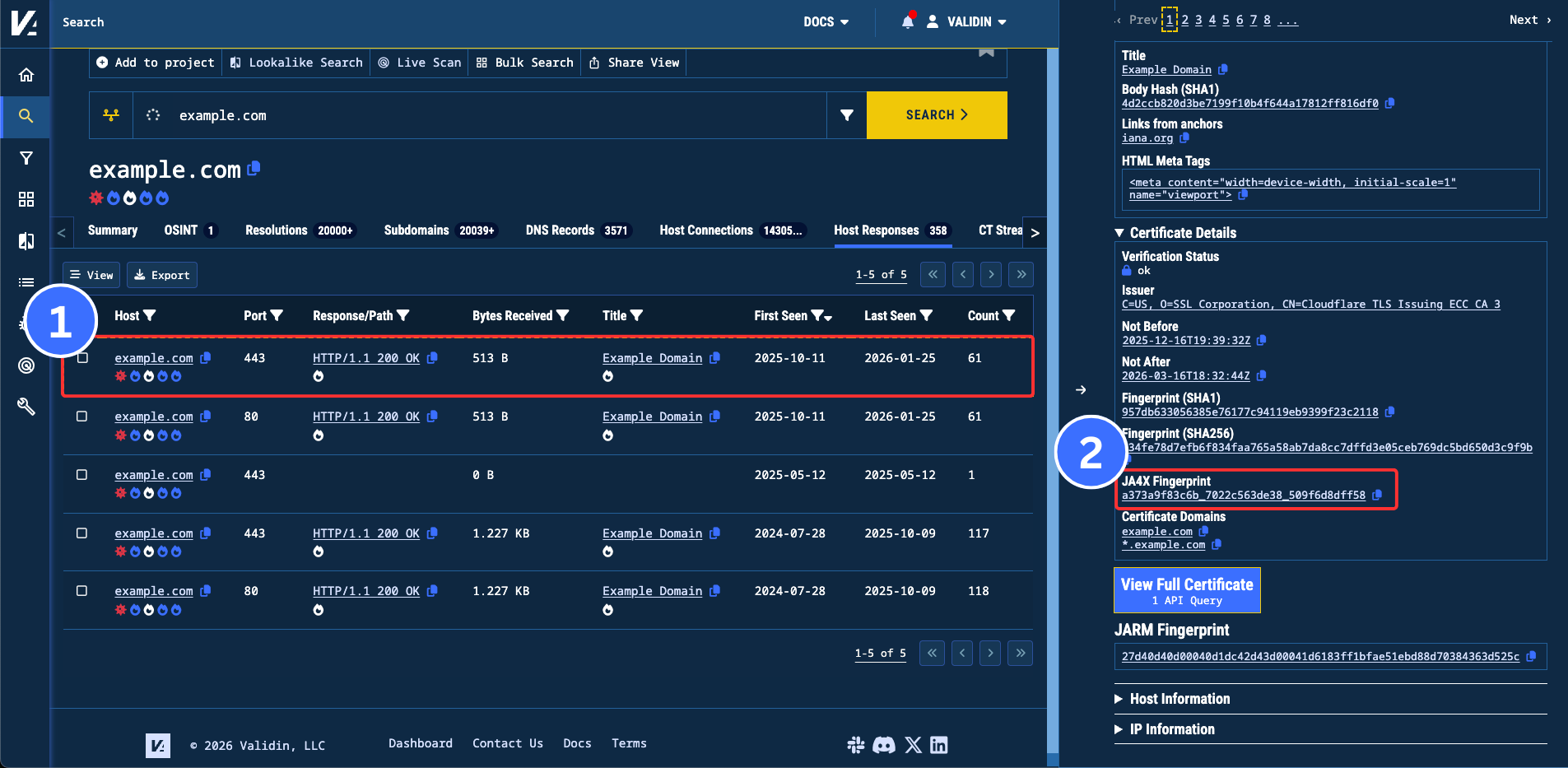
The calculated JA4X for the certificate we received when we crawled this host
2. The “Host Connections” tab
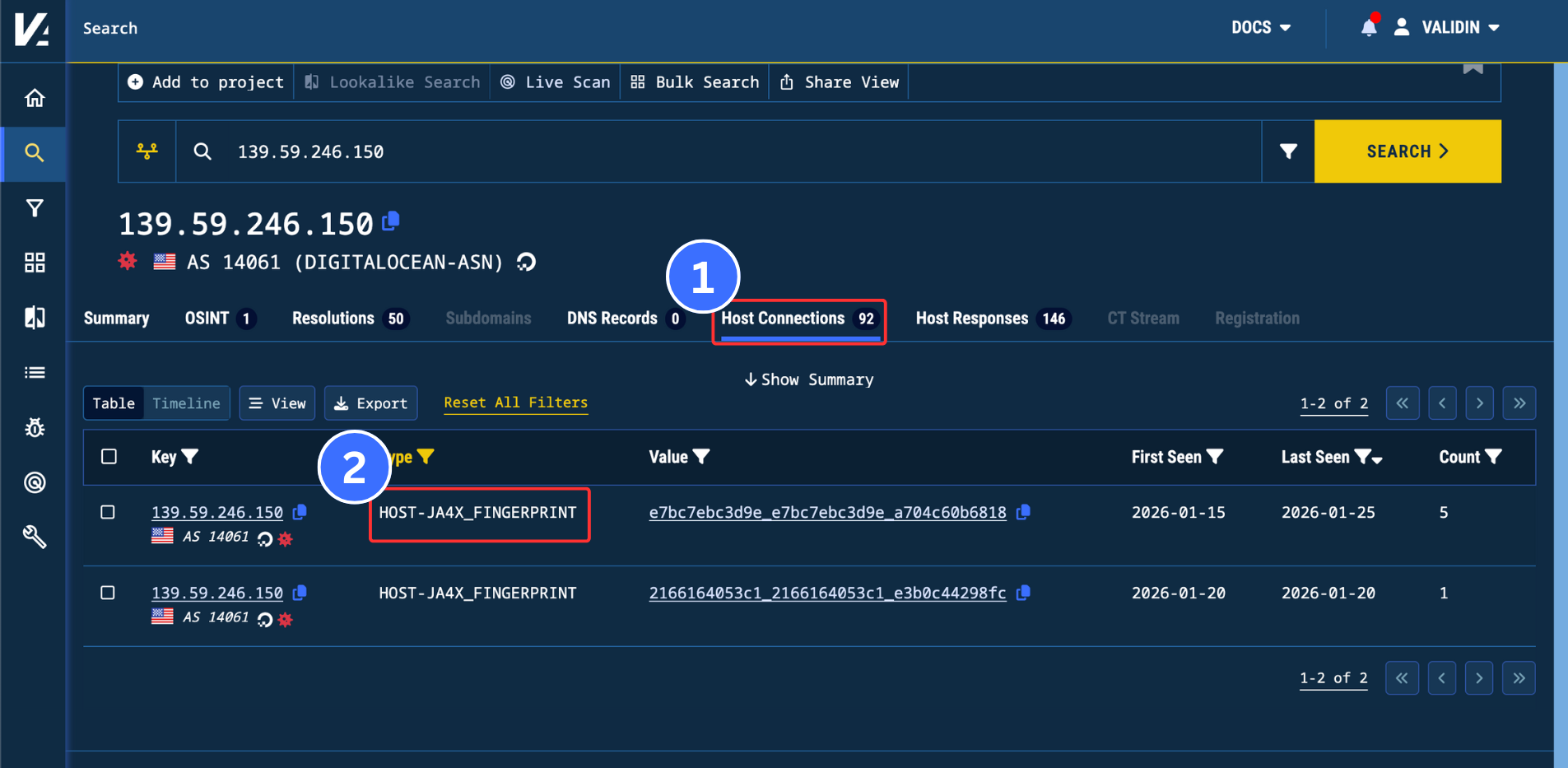
The calculated JA4X pulled out from all host responses allowing for quick search and pivoting
There are two places where JA4X fingerprints can be used for searches: core search and advanced search. JA4X can be particularly useful for finding C2 infrastructure as that infrastructure can share custom implementations for certificate generation.
Example: Use a JA4X Fingerprint in Validin to Discover Malware IoCs
An interesting example of a fingerprint that we found was the indicator e7bc7ebc3d9e_e7bc7ebc3d9e_a704c60b6818, which, when searched via our core search, yields six high confidence indicators for BianLian Malware.
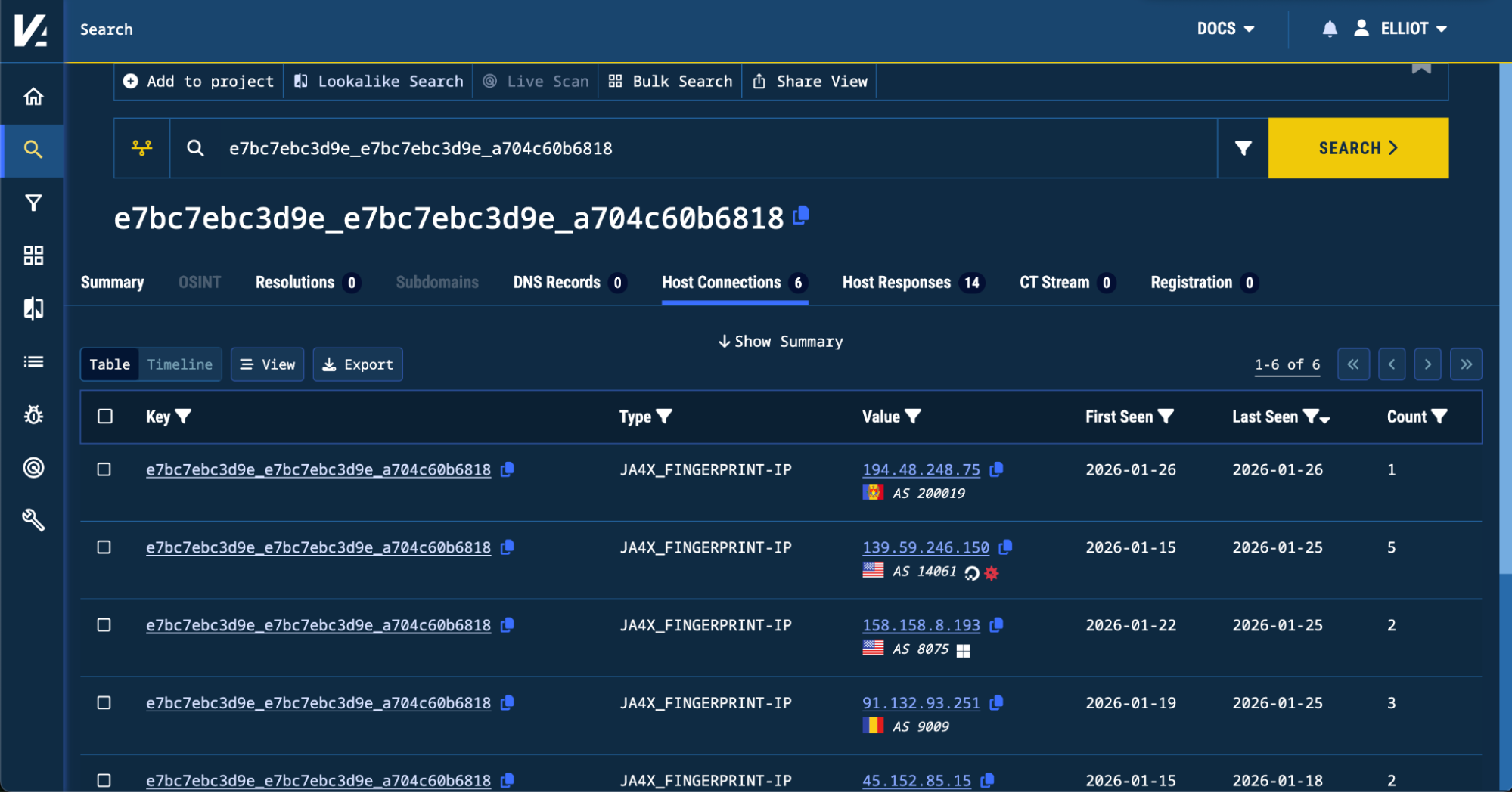
Searching for a JA4X associated with Bianlian malware
JA4X can also be used within our advanced search, accessible via the field cert.fingerprint_ja4x.
Example: Uncover QuasarRAT C2 servers with JA4X Fingerprint in Validin
For example, a great query to uncover QuasarRAT C2 servers is through combining the known JA4X fingerprint of these C2 servers: 7022c563de38_7022c563de38_0147df7a0c11. Starting from here in Validin’s core search yields 1125 IP addresses with a matching JA4X response.
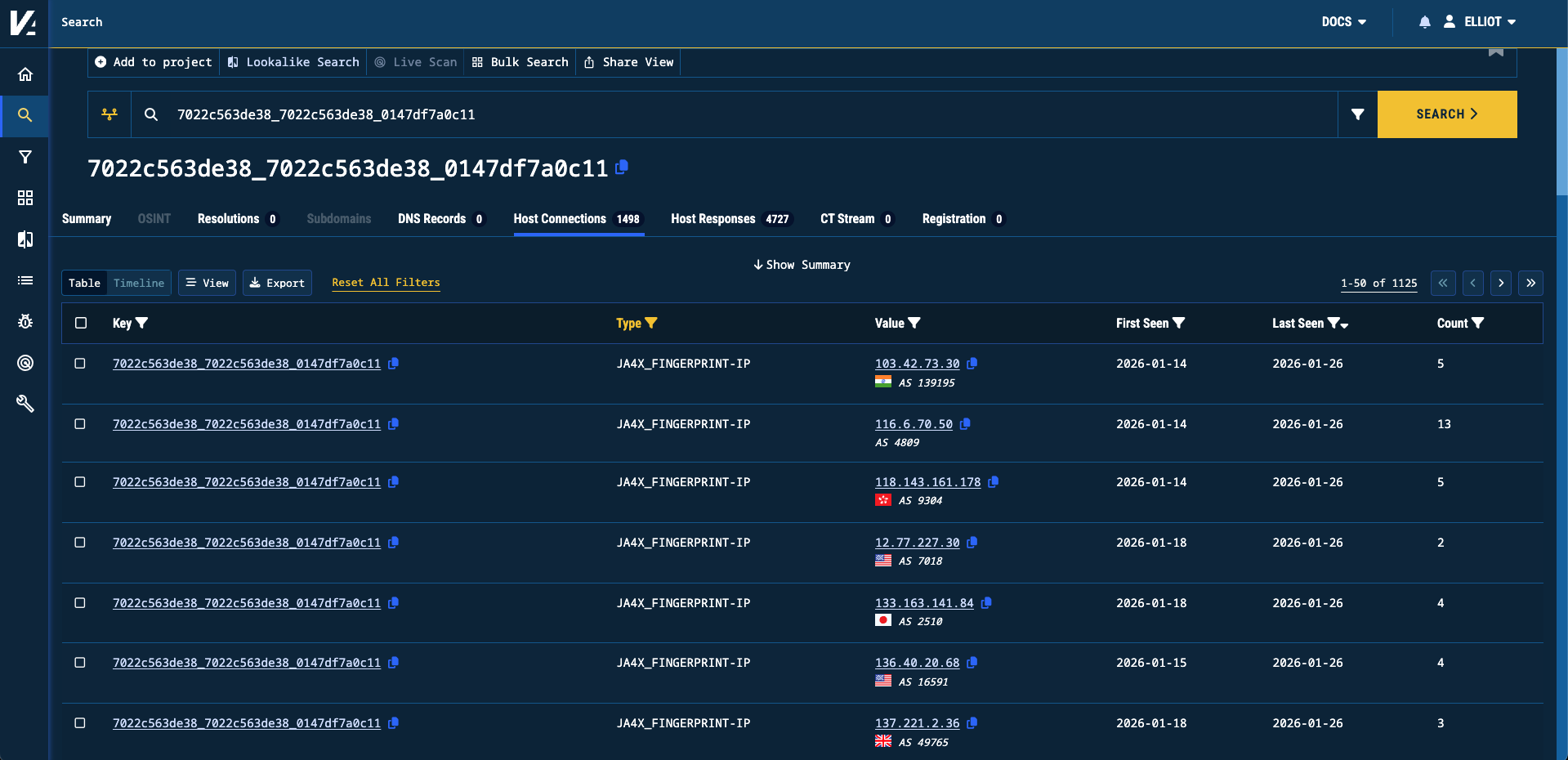
Matching IP Addresses for QuasarRat-associated JA4X
A spot check of the IPs and domains hints that this search is too generic. To narrow things down we can find another aspect of these certificates to filter. We can filter for IPs that have already been publicly flagged as malware. Observing the certificates for these IPs shows that all 6 IPs that have already been publicly tagged as malware have a ‘Not After’ value of 9999-12-31T23:59:59Z , the maximum value allowed in the field.
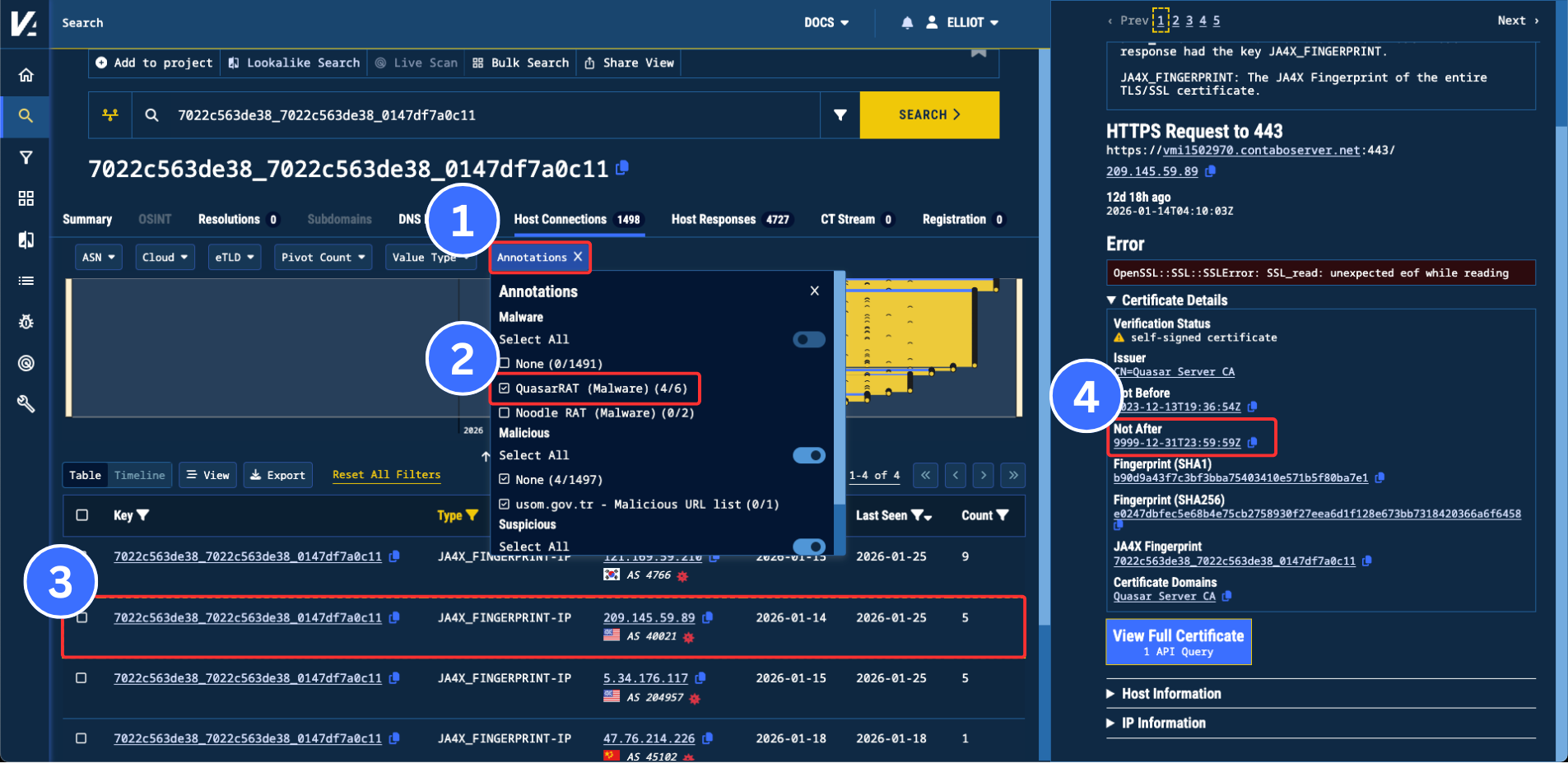
Unusual expiration date observed in the certficates
We are unable to use the Not After pivot individually, because over 20,000 responses have this Not After date in their certificate. However, we can construct an advanced search query that combines both the JA4X fingerprint and the certificate Not After date.
cert.not_after="9999-12-31T23:59:59Z" AND cert.fingerprint_ja4x="7022c563de38_7022c563de38_0147df7a0c11"
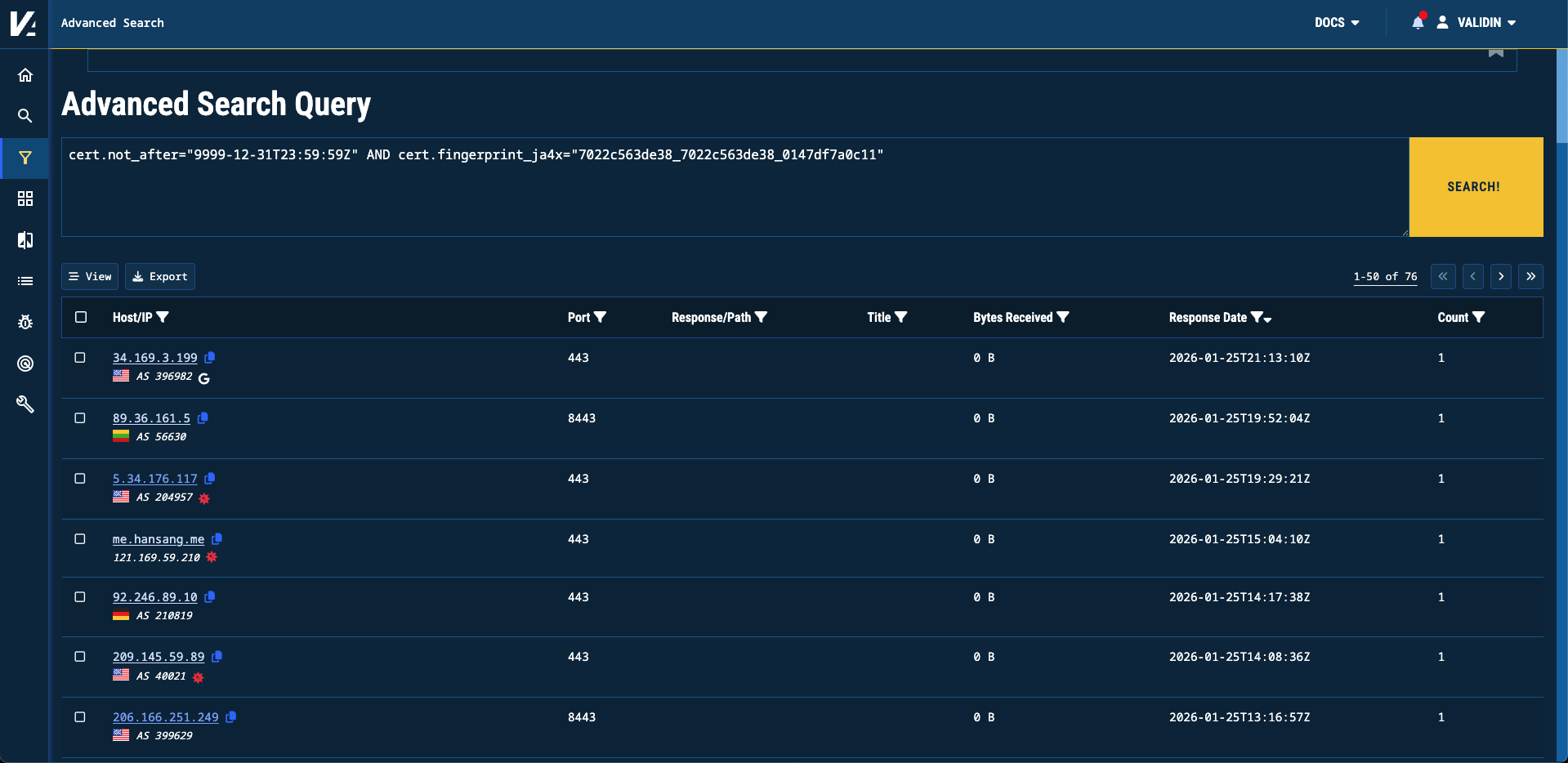
Advanced search using JA4X that finds QuasarRAT C2 Servers
While each of these IPs and domains still need additional verification, we now have a much smaller and higher confidence subset of results that we can feasibly individually verify. The full suspected indicator list is included below.
Conclusion
Validin is committed to providing the best tooling to Cyber Threat Intelligence (CTI) analysts for discovering and monitoring threats on the open internet. Providing JA4X support immediately opens up new ways for users to hunt in the Validin platform. We plan to continue adding support for additional fingerprints in the JA4+ suite. If you have any preferences on which we should prioritize first, please reach out to support@validin.com.
Indicators
194.48.248.75
139.59.246.150
158.158.8.193
91.132.93.251
45.152.85.15
130.94.29.233
34.169.3.199
89.36.161.5
5.34.176.117
121.169.59.210
92.246.89.10
209.145.59.89
206.166.251.249
27.124.2.46
35.226.108.177
27.124.2.52
94.156.189.117
185.82.218.221
5.34.176.160
51.77.231.232
98.142.254.207
47.77.204.50
1.54.115.86
118.68.121.207
47.76.214.226
58.187.16.102
27.124.2.48
42.115.10.126
52.184.27.75
