Are pivots from recent blog posts still useful?
In this blog post, we revisit some of our blog posts from the last few months to determine how relevant specific pivots and techniques mentioned in the posts are to current investigations of their respective threats. The purpose is to evaluate whether or not the threat hunting techniques exhibited in the blog post are still viable ways to discover new indicators related to these threat actors.
We approached this scientifically and determined the test methodology before we began. However, we did not thoroughly exhaust the question and pull all possible threads, so this post won’t be an exhaustive list of new indicators. We followed enough of the documented threat hunting workflow to be able to answer the question: are the pivoting and threat hunting techniques in the blogs still viable today?
Selection of blogs:
- The four blog posts were the four most recently-published posts by the Validin team that dove into specific threat hunting techniques
- They’ve all aged between 1 and 4 months
- Each post reported on infrastructure that demonstrated some continued evolution and were not purely retrospective (fresh indicator potential)
Methodology:
- Follow the discovery and pivoting processes defined in the blog posts
- Check if previously-reported connections can still be found
- Evaluate if we are successfully able to identify newer indicators, especially those that are very recent (created since the blog post being evaluated was published and the initial set of indicators was disclosed by Validin)
These are the blogs that meet the selection criteria:
- Hunting Laundry Bear: Infrastructure Analysis Guide and Findings | Validin
- Finding Fake/Phishing Domains with HTML Features in Validin
- Zooming through BlueNoroff Indicators with Validin
- Illuminating Transparent Tribe with Validin
Let’s dive in!
Laundry Bear
In “Hunting Laundry Bear: Infrastructure Analysis Guide and Findings”, we started with two domain names identified by Dutch intelligence and Microsoft Threat Intelligence and used these techniques to identify additional, possibly related infrastructure:
- Regular expression search
- Host response pivots
The Regular Expression Search resulted in 5 additional lookalike domains similar to the “ebsummit” theme, and the host response pivots resulted in 25 domains with host response similarities to the “micsrosoftonline[.]com” lookalike domain.
Replicating the Regex Search
The regex search used was:
/^e[bd]s[uan]?(rn|m)+([li]?t)?s?.eu$/
Replicating this search today, we find one additional domain that matches the regex, but that is the extent of the overlap with the original set that we found. The nameservers, registrar, contact emails, and other key attributes are all different.
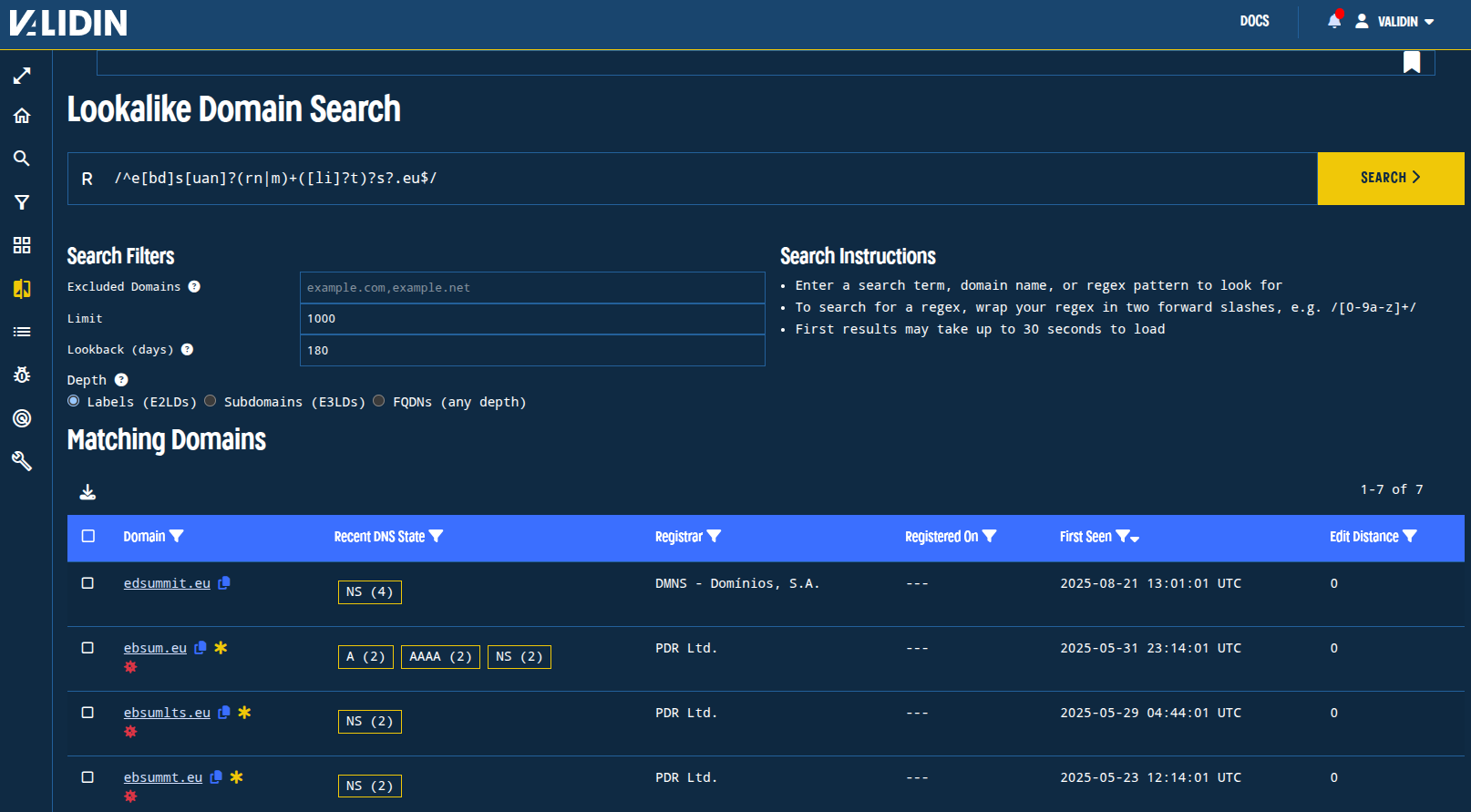
Figure. Lookalike search for domains similar to ‘ebsummit’.
The new match is certainly inconclusive, and most likely not related to the targeted campaign from earlier in the year.
Replicating Host Response Pivots
The original blog post started with the HTML SHA1 hash 38c47d338a9c5ab7ccef7413edb7b2112bdfc56f, returned by the known Laundry Bear domain micsrosoftonline[.]com, then pivoted through unique features in domains connected via that SHA1 to discover additional domains and IPs related by tooling, hosting infrastructure, and content.
Replicating the initial pivot, we find 12 new fully-qualified domains (FQDNs, which include subdomains) on one apex domain: 1drvms[.]co[.]za. In the original post, we pivoted features from the newly-connected domains and explored those connections. Can we do the same with the most recently observed domain 1drvms[.]co[.]za?
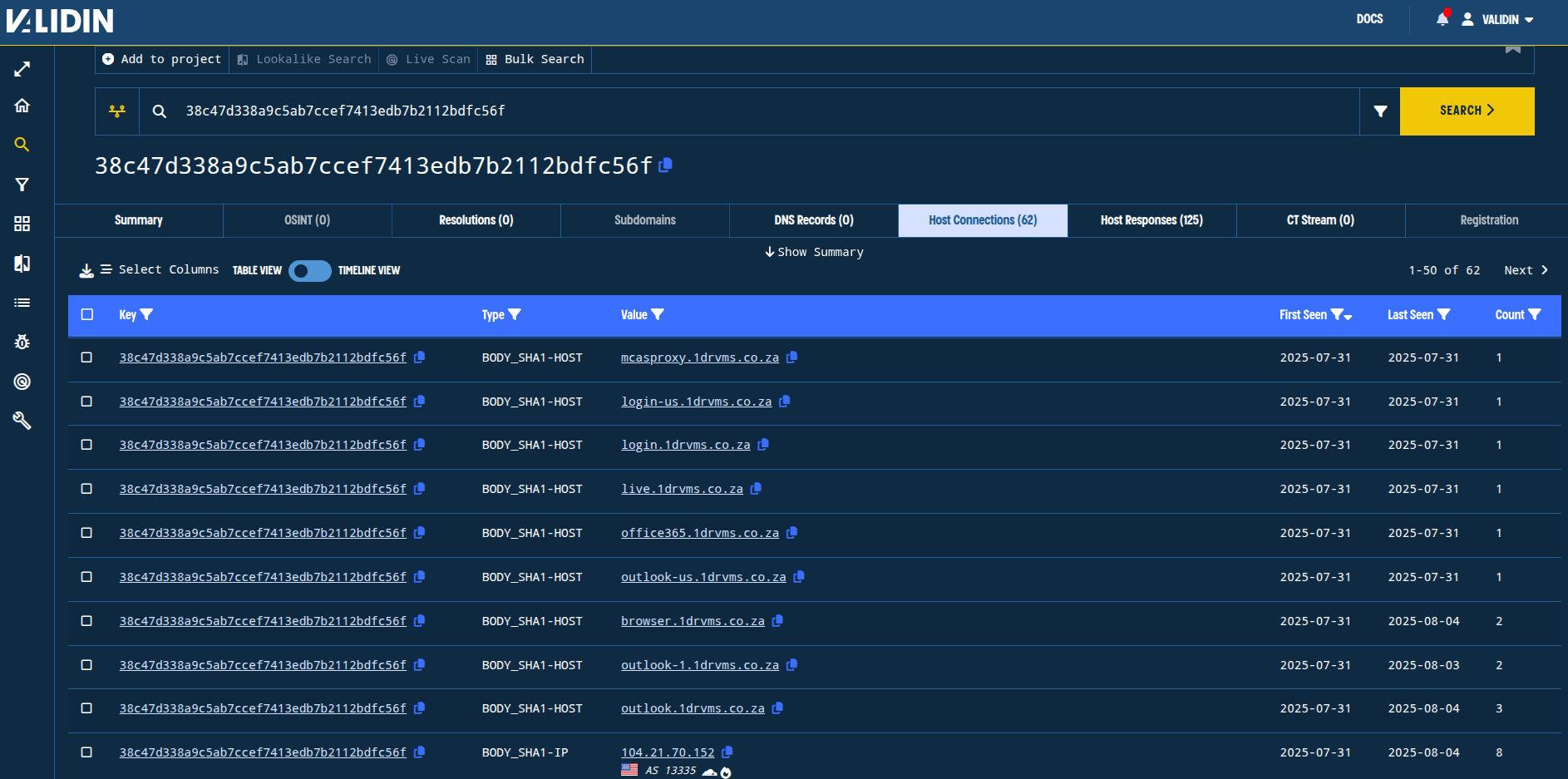
Figure. A dozen domains that went live shortly after Validin’s Laundry Bear blog post in July 2025.
Let’s start by finding the features associated with one of the many subdomains, office365[.]1drvms[.]co[.]za. We’ll open the “Host Connections” tab and filter out any highly-connected features, focusing only on those with less than 20k estimated connections.
![Figure. Host connections for office365[.]1drvms[.]co[.]za, showing extracted, pivotable features. The “pivot count” filter can be used to select the features that have lower cardinality and are most likely to connect to a more uniquely-configured set of domain names and IP addresses. Figure. Host connections for office365[.]1drvms[.]co[.]za, showing extracted, pivotable features. The “pivot count” filter can be used to select the features that have lower cardinality and are most likely to connect to a more uniquely-configured set of domain names and IP addresses.](/images/pivots_revisited_summer_2025/image3.png)
Figure. Host connections for office365[.]1drvms[.]co[.]za, showing extracted, pivotable features. The “pivot count” filter can be used to select the features that have lower cardinality and are most likely to connect to a more uniquely-configured set of domain names and IP addresses.
Pivoting on the first feature, the banner hash a6b3cc14237029c0f1fa9b6de007358a, we observe over 1000 connections across just under 200 unique apex domains (with several subdomains each, on average) with the same banner hash over the last 2 weeks, including portal-microsoftonline[.]com, which is one of the domain names identified in our original blog post.
![Figure. A sample of domain names connected by banner hash to 1drvms[.]co[.]za. Figure. A sample of domain names connected by banner hash to 1drvms[.]co[.]za.](/images/pivots_revisited_summer_2025/image12.png)
Figure. A sample of domain names connected by banner hash to 1drvms[.]co[.]za.
From additional responses observed after our blog post, we find additional banner hash pivots that connect to similarly-configured domain names:
2fb084c9943b733e6b7f65ac1c2f0fc687ca9a795b6e63749632821e1f3d465d
Examples of domain names connected via these banner hashes include:
oauth2-teams[.]com
official365[.]online
docu-delivered[.]com
xn--pmg-6ua[.]com ("ķpmg[.]com")
m36share[.]cloud
miicro-sftoffiic[.]it[.]com
Verdict
Host response pivots continued to yield fresh results six weeks after publication of the original blog, and we were able to continue to find many potentially related domains to the original set via connected host response feature pivots. While we still cannot determine conclusively if these domains are directly associated by the original threat actor due to the lack of specificity in the Dutch and Microsoft reporting about their usage, our ability to find relevant and interesting domains using the same pivoting techniques described in the original blog post does not appear to have diminished.
Finding Fake/Phishing Domains in Validin
In Finding Fake/Phishing Domains with HTML Features in Validin, published on July 10, 2025, we demonstrate how a variety of different HTTP based pivoting techniques can yield undiscovered indicators from publicly reported incidents. While some were unsuccessful, with many of the Validin searches demonstrated in the blog post, we are still able to find novel suspicious domains that came online even within the past 24 hours.
Mac OS Click Fix
Starting with the original MacOS-themed Click-Fix indicator fix-mac-easy[.]com, performing a quick pivot with the favicon hash does not yield new indicators. In fact, the hash was last seen in Validin on July 24th, suggesting that it is no longer a viable pivot to uncover novel infrastructure. Exploring the other discovered indicators in the blog yields few novel or interesting results. Title tags such as “FIX IT ANYWHERE” also do not show any new infrastructure that is seemingly related. We observe from Validin’s timeline view that these title tags were used in a very limited way.
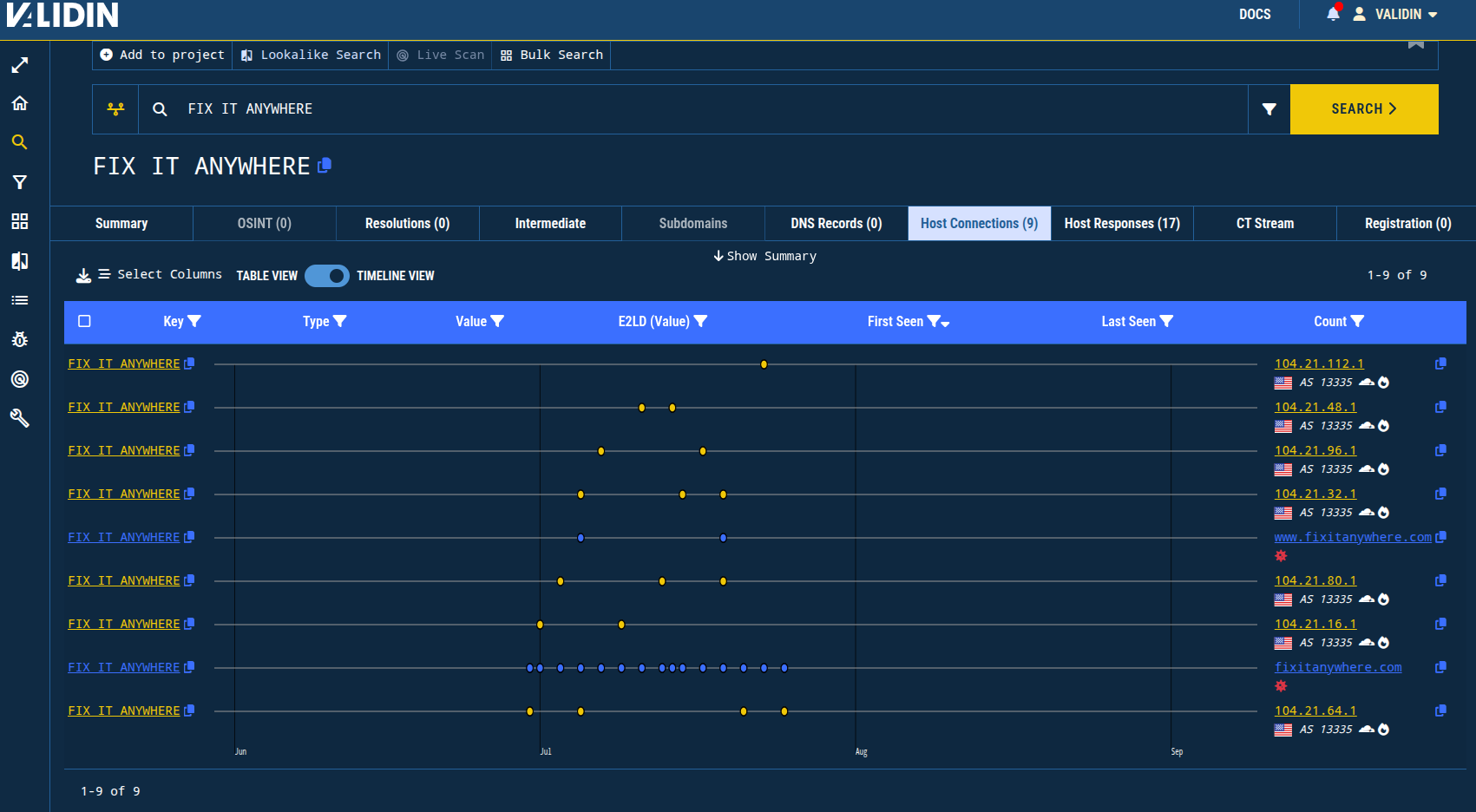
Figure. Timeline view of the “FIX IT ANYWHERE” title tag pivot shows a usage cycle confined to about a month.
Phishing Redirectors
Moving on, we re-test the redirect indicators seen in a reported phishing campaign, starting with the indicator mlpro-trckr[.]com. As a reminder, this domain was the target of several other feeder domain redirects. After searching the indicator again on Validin, filtering by the LOCATION_HOST-DOMAIN type (redirect domain) in the host connections, and sorting by last seen date, we see that domains that are still redirecting to mlpro-trckr[.]com.
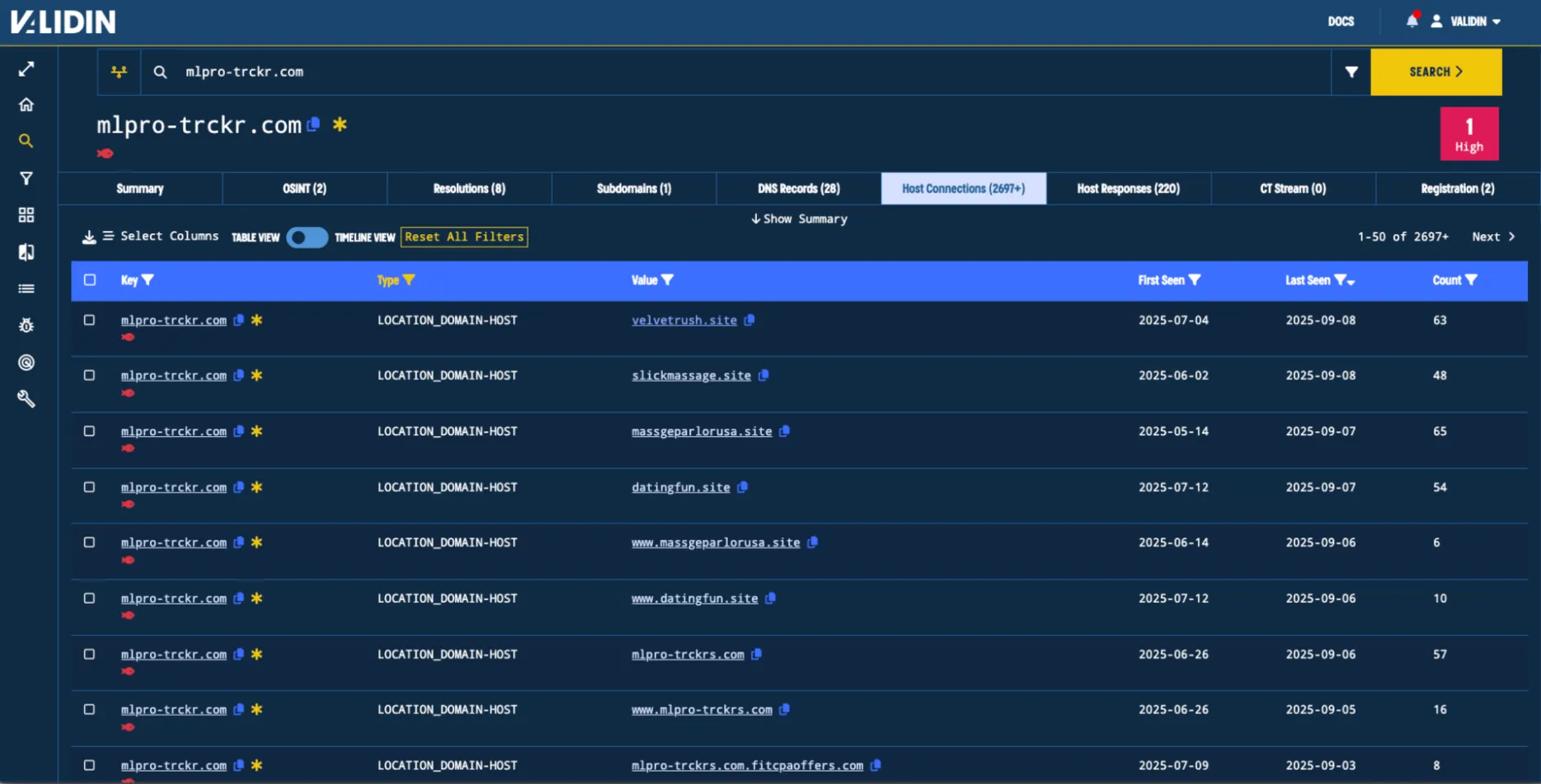
Figure. Location redirects from other domains show ongoing activity from the originally-reported campaign.
From here, our blog post used the most recent header_hash value (dd01ae950b600d5bd3e6) available at the time to find other related infrastructure.
Replicating this, by searching the most recent header_hash value, first seen on September 3rd, 2025 (dd01ae950b6011988c44) and filtering for domains that have not been marked as malicious yet, we find two new domains that were stood up on September 3rd.
smsecuring[.]commailrdx[.]com
Both are lexicographically similar to the domains that we discovered through our original pivoting. For comparison, here is a subset of our originally discovered domains:
eml-pro[.]comml-pro-trckr[.]comsmlinksw[.]liveindsecurewin[.]livesweepsafe[.]live
Notice the shared “sm” prefix, the use of the root of the key word “secure,” and the mail theme. These two new domains have been recently active, which may indicate that this campaign is still active.
Malicious Extension C2
In this section of the blog, we used a body SHA hash to identify suspicious domains used as command and control endpoints. Searching the same value in Validin today (539b0037602495bc1c16c2fb85a32913f14ae12f), reveals more domains that were first seen after our blog’s previous publishing date. The cluster of undiscovered domains returned a response body with this hash for about a week in mid July.
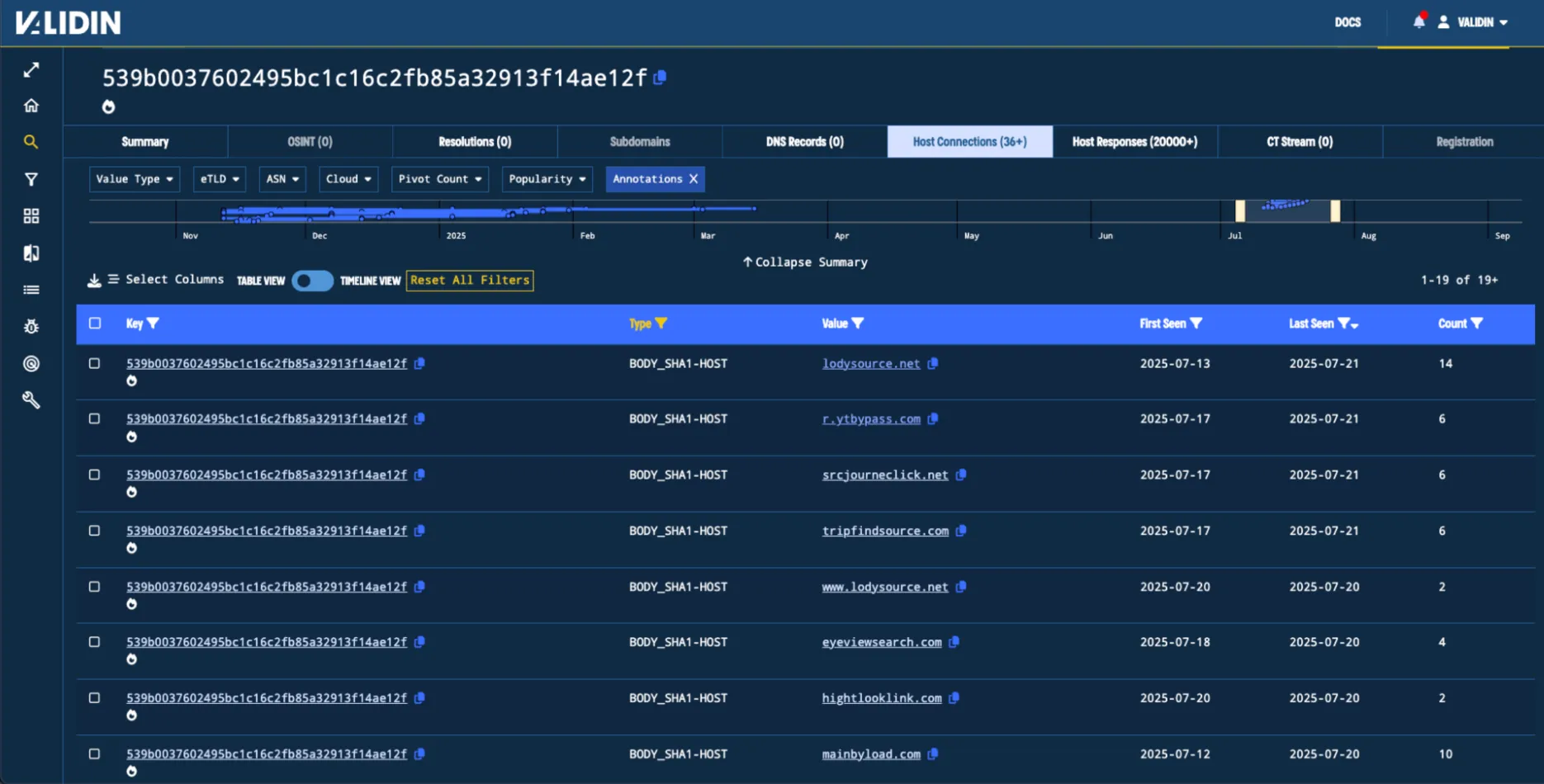
Figure. Body hash pivots.
Looking at the domains lexicographically, indicators like r.ytbypass[.]com are similar to previously reported domains referencing YouTube. However, none seem to be active currently. The full list of new indicators is below.
lodysource[.]net
r.ytbypass[.]com
srcjourneclick[.]net
tripfindsource[.]com
www.lodysource[.]net
eyeviewsearch[.]com
hightlooklink[.]com
mainbyload[.]com
discofind[.]net
www.hightlooklink[.]com
www.srcjourneclick[.]net
www.eyeviewsearch[.]com
cristfind[.]com
sourcefinderpro[.]com
www.arelinksrc[.]com
www.mainbyload[.]com
arelinksrc[.]com
www.discofind[.]net
www.sourcefinderpro[.]com
www.higedown[.]net
higedown[.]net
loadmatchgo[.]com
urldata[.]net
www.easylinkweb[.]net
easylinkweb[.]net
www.urldata[.]net
urgesrclink[.]com
www.loadmatchgo[.]com
www.urgesrclink[.]com
loadsrctool[.]com
www.loadsrctool[.]com
coopertimer[.]com
www.sirtonel[.]com
poloframe[.]com
www.coopertimer[.]com
www.poloframe[.]com
Fake Apps Download
Previously, we uncovered fake Eventbrite infrastructure through HTML title tags marked “Gradient Page.” Using the exact same query in Validin today, filtering for domains that have not been marked as malicious with the same Title Tag value, we find 45 undiscovered domains with a very similar naming convention. By spot checking a few of their homepages, we can see that they contain the same HTML as the original domain. Seven of these domains are still active as of writing this blog.
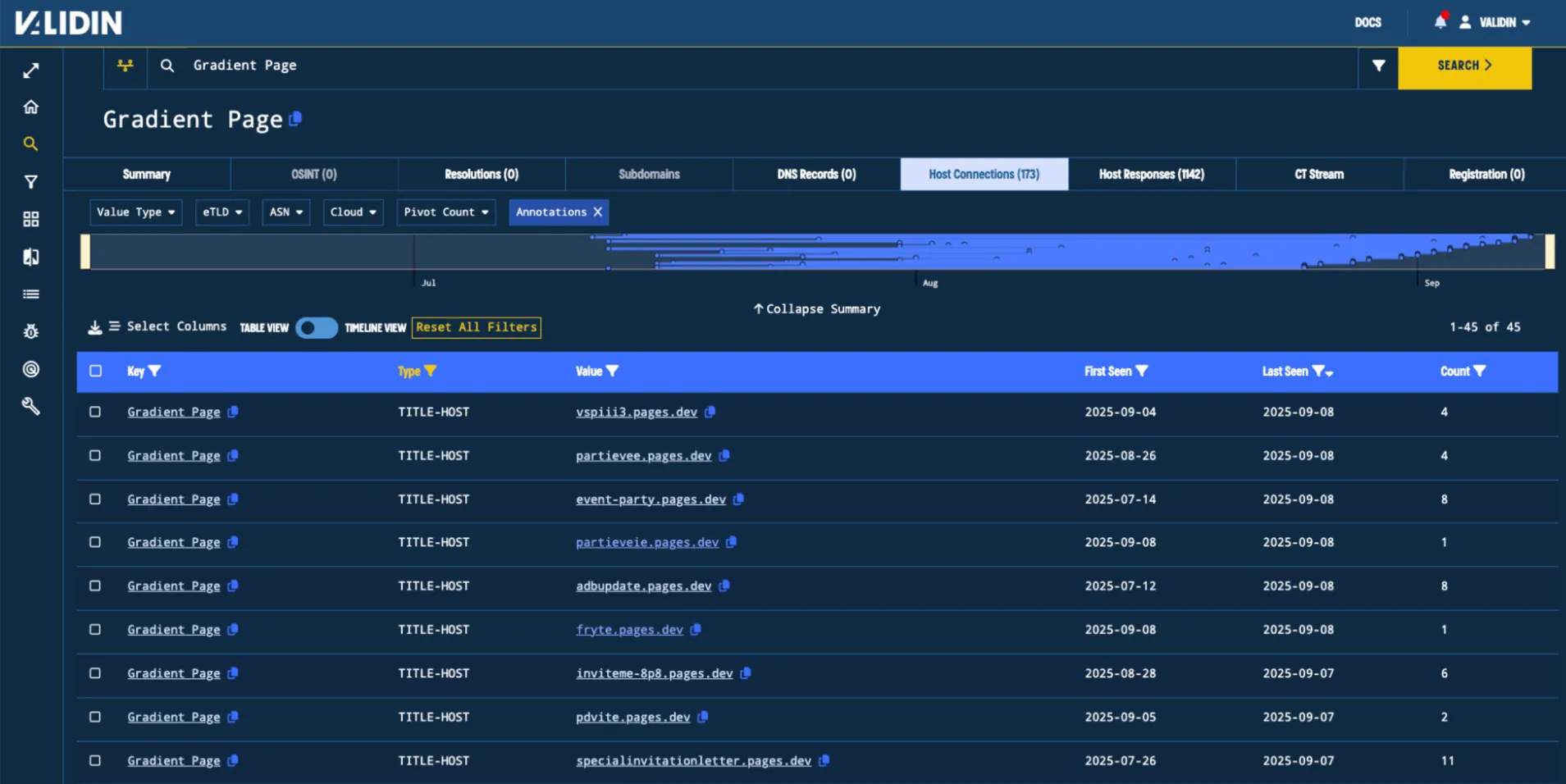
Figure. The timeline view of all host responses seen with title “Gradient Page”
partieveie.pages[.]dev
fryte.pages[.]dev
blorpt.pages[.]dev
pdvite.pages[.]dev
vspiii3.pages[.]dev
partievei.pages[.]dev
inviteme-8p8.pages[.]dev
vipevebite.pages[.]dev
partievee.pages[.]dev
smisl.pages[.]dev
exlusive-invite.pages[.]dev
evitespann.pages[.]dev
partieve.pages[.]dev
simbs.pages[.]dev
vspiii.pages[.]dev
evebrite.pages[.]dev
klick4me.pages[.]dev
special-invitation-cb7.pages[.]dev
rsvpinvite.pages[.]dev
simbaalt.pages[.]dev
ivit.pages[.]dev
altnewprop1.pages[.]dev
newaltpro.pages[.]dev
exclusive-invitation.pages[.]dev
openinvitation-bsd.pages[.]dev
exclusive-invite.pages[.]dev
invitataion-me.pages[.]dev
rsvp-3gb.pages[.]dev
innitive.pages[.]dev
specialinvitationletter.pages[.]dev
allinvite.pages[.]dev
click-me-do3.pages[.]dev
special-invite.pages[.]dev
event-1cz.pages[.]dev
preminv.pages[.]dev
clickme-1uo.pages[.]dev
invitee.pages[.]dev
inviteenow.pages[.]dev
inviteus-c2d.pages[.]dev
nwat.pages[.]dev
event-party.pages[.]dev
inviteus.pages[.]dev
evitenow.pages[.]dev
openinvite.pages[.]dev
adbupdate.pages[.]dev
Verdict
Out of the four HTTP pivoting techniques we reviewed in our blog, three yielded novel indicators yet to be publicly reported, bolstering their viability as threat hunting techniques. In addition, two of these techniques revealed active related and interesting infrastructure that suggests these campaigns are still ongoing.
Transparent Tribe
In “Illuminating Transparent Tribe with Validin” published June 2nd, we found undiscovered infrastructure potentially related to the Transparent Tribe threat actor.
Wildcard Subdomains
Starting from the initial two indicators: kashmirattack[.]exposed and ministryofdefenceindia[.]org. We enumerate their subdomains via a wildcard search in Validin. Unsurprisingly, this search does not uncover any new indicators today.
DNS Resolution History
Moving onto the next set of indicators uncovered by our previous blog:
37.221.64[.]134 - AS 200019 (ALEXHOST, Moldova)45.141.58[.]224 - AS 213373 (IPCONNECT, Seychelles)78.40.143[.]188 - AS 45839 (SHINJIRU-MY-AS-AP Shinjiru Technology Sdn Bhd, Malaysia)78.40.143[.]189 - AS 45839 (SHINJIRU-MY-AS-AP Shinjiru Technology Sdn Bhd, Malaysia)176.65.143[.]215 - AS 44592 (SKYLINK, Netherlands)
We find that very little has changed for each of these IPs since, while 78.40.143[.]188 and 78.40.143[.]189 appear to point to new domains, it is most likely that they use shared hosting, suggesting they have little relevance to this blog.
It should be noted that while this pivoting technique did not yield anything for the original indicator set, using the same set of methods for IPs related to freshly reported Transparent Tribe indicators in the Validin feed yields more interesting results. For example, looking at the recently reported indicator gov[.]in[.]web[.]viewcard[.]in we find that the domain most recently has resolved to the IP 86.107.77[.]54. Viewing the DNS resolution history for this IP, we see several domain names that seem to match the pattern for subdomains used in identifying Transparent Tribe domains.
Additionally, by selecting the “Host Connections” tab and filtering for values that contain “Aadhar”, we find several websites that seem to be posing as printing services for Aadhar cards, the Indian biometric ID.
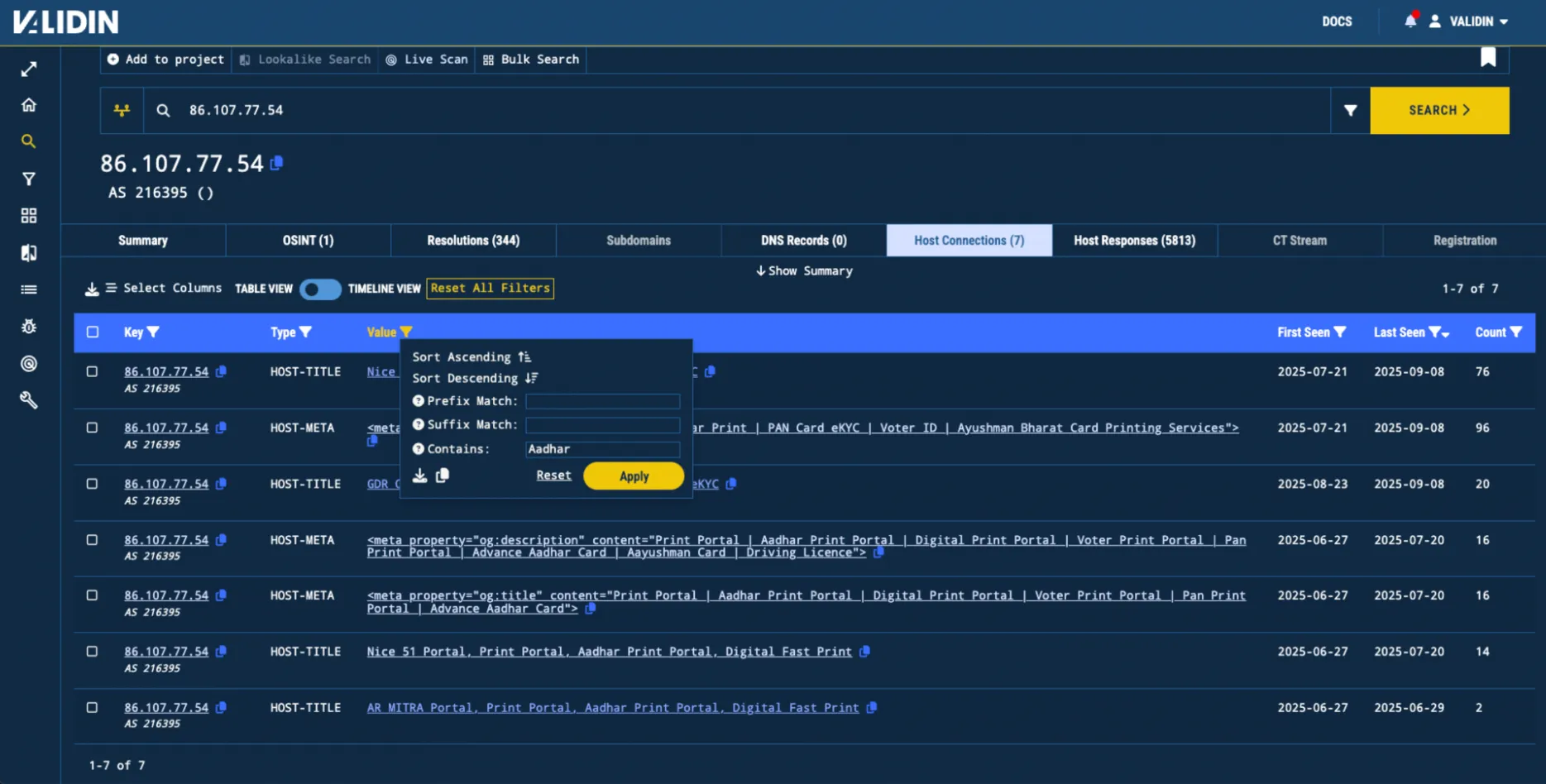
Figure. The Host Connections tab of the suspicious IP filtered by the keyword “Aadhar”
See below a screenshot of viewpage[.]xyz, which is a reported indicator that has a title tag containing the keyword “Aadhar”. It advertises printing services related to Aadhar cards.
![Figure. The homepage of viewpage[.]xyz advertising Aadhar card print services. Figure. The homepage of viewpage[.]xyz advertising Aadhar card print services.](/images/pivots_revisited_summer_2025/image18.webp)
Figure. The homepage of viewpage[.]xyz advertising Aadhar card print services.
This set of indicators shows noteworthy behavior that may be linked to the Transparent Tribe, as they appear to be fake advertisements for government-related services targeting India. For brevity, we leave this as an open thread.
Possible indicators:
viewpage[.]xyzgdronline[.]xyzarmitra[.]inallfast[.]in
E-TAG
We explore the next pivot: the E-TAG. Searching the E-TAG value W/"18-yDYnaqhRYUMt/OyUu05l2wAGXRQ", we see that it was last seen in our data August 11th, 2025. However, for about 6 months starting March 4th, it was an effective means of identifying potential Transparent Tribe infrastructure and notably, it remained so even after we published our blog on June 2nd.
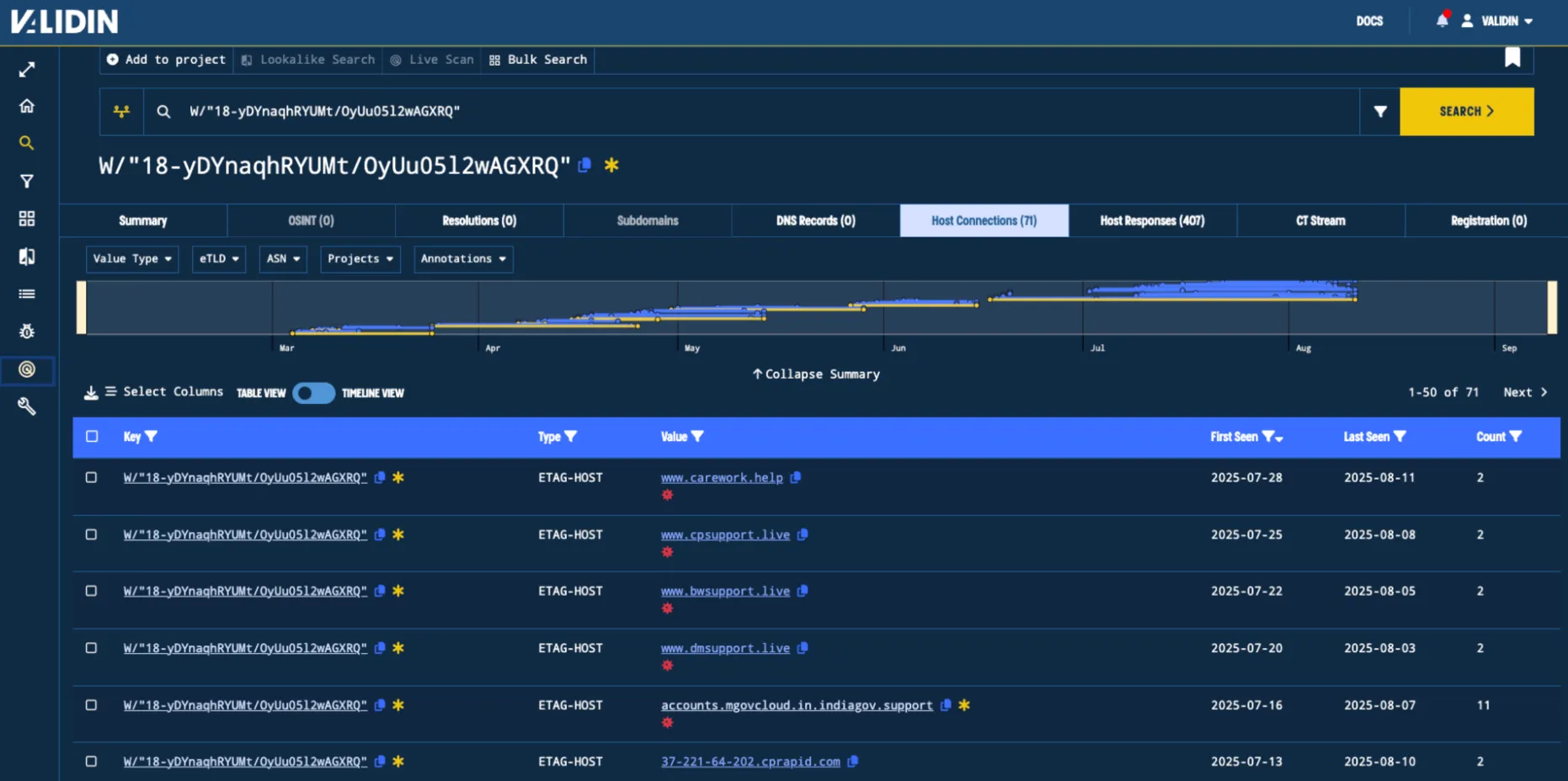
Figure. Timeline view of the domains that had the E-TAG from March to August.
This E-TAG could be used to fine new domains associated with this campaign for an additional two months after the initial blog post.
Title Tag
Finally, we have the title Tag “Pahalgam Terror Attack Updates.pdf”. It does not show any new result past May, suggesting that it is no longer an effective way to identify new infrastructure. This is not entirely unsurprising, as this string is referencing an event, which would no longer be relevant.
Verdict
Applying the same pivoting techniques to fresh indicators in Validin’s Transparent Tribe does reveal interesting threads to pull. While some techniques showcased within the blog continued to work after its publishing, the majority no longer work today.
BlueNoroff
In “Zooming through BlueNoroff Indicators with Validin,” published on June 20, 2025, we started with research published by Huntress into a targeted intrusion into a Web3 organization that was attributed to BlueNoroff (also known as APT38).
We began this post with an observation that the reported domain support[.]us05web-zoom[.]biz resolved to 8.8.8.8 for several weeks. We used Validin’s DNS search features to find other domains with similar resolution patterns, then found host response, DNS, and resolution pivots to identify more domains that are likely associated with similar campaigns by BlueNoroff.
We’ll revisit each of these pivoting strategies to see if we can continue to identify new domains with them.
8.8.8.8
Using the search and filtering techniques described in our blog post, we’ll see if we can find similar domains ending with .biz, .us, .com, and .space. We also filtered for domains containing “zoom”, “meet”, “web”, and “support” in the original blog post, so we’ll do the same here.
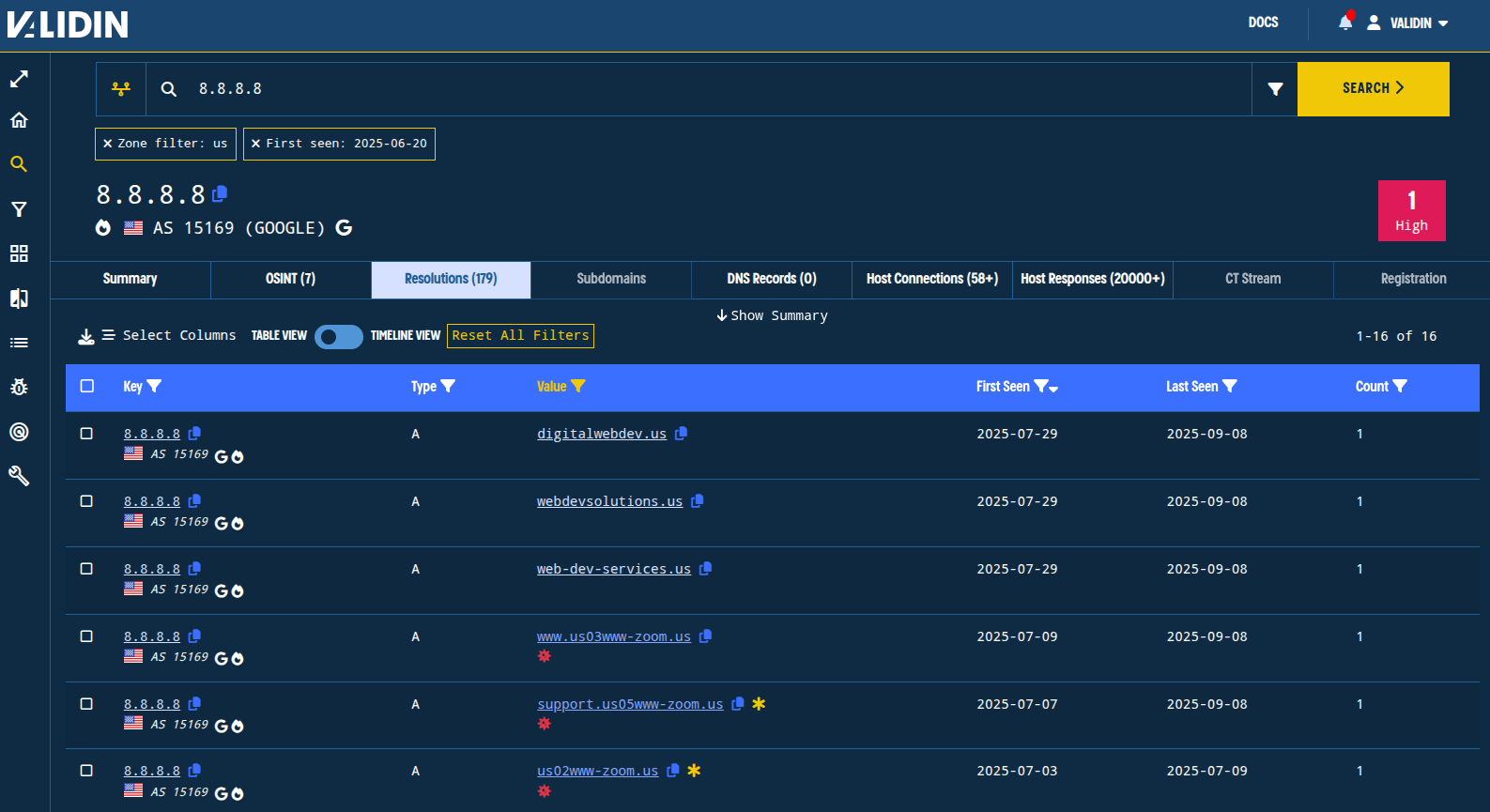
Figure. Recent results for newly .us domains resolving to 8.8.8.8 that have specific keywords in the domain name.
Of the three newly-observed zoom-themed domains, two are net new (though have already been publicly reported due to increased awareness from our original blog post), and one is actually a repeat from the original blog post.
Looking at the DNS timeline for us02www-zoom[.]us in Validin, we find several instances of IP address reuse, and the use of a new IP address starting on August 20, 2025 (23.254.226[.]83). We’ll save the other IP addresses for later because IP pivots were a technique described in the original blog post.
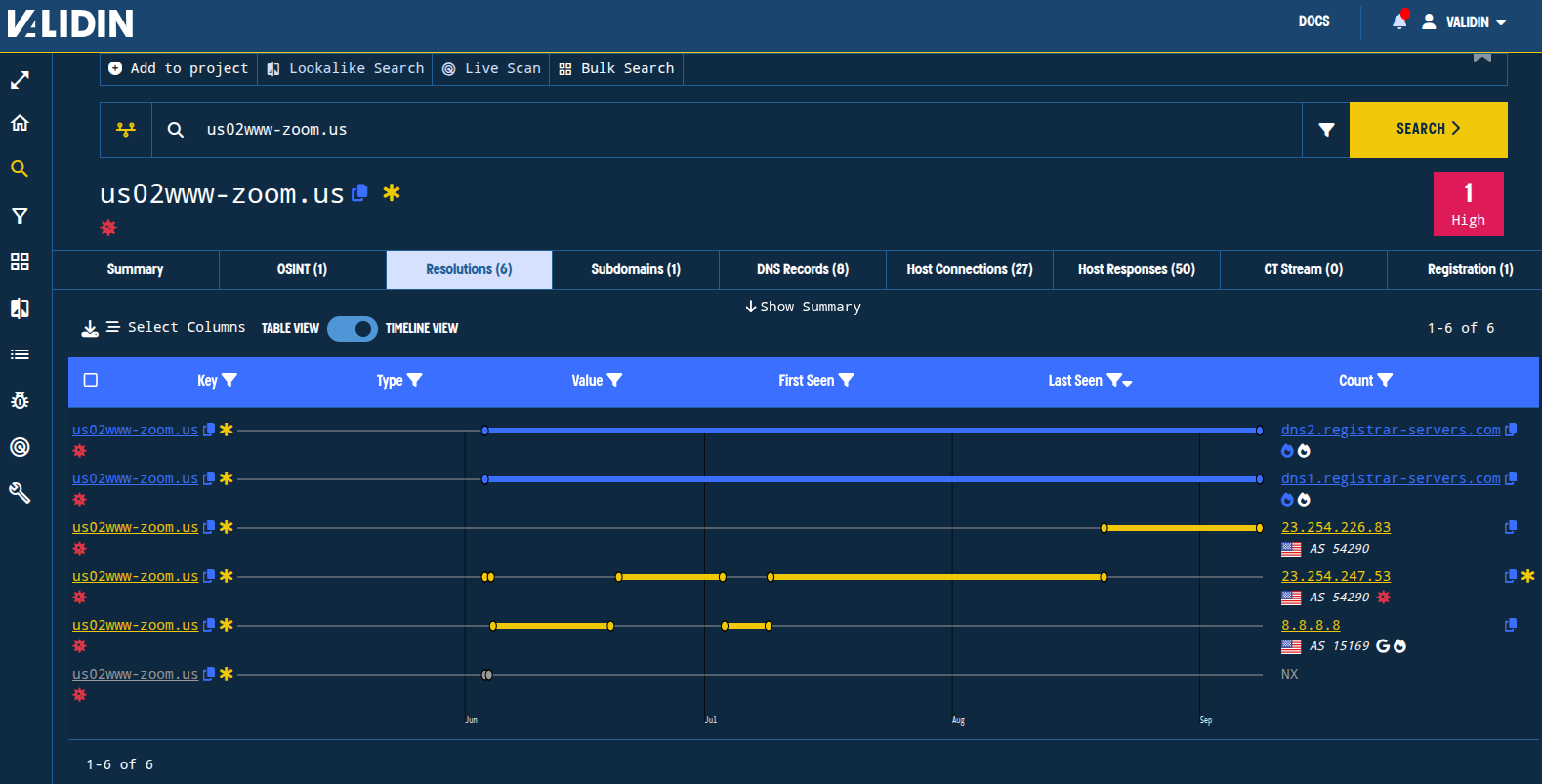
Figure. Validin DNS history timeline view showing rotation and reuse of IP addresses.
In our original blog post, we found 18 domains this way. Today, we still find most of the same indicators, plus these new indicators that have already been publicly attributed to BlueNoroff:
us03web-zoom[.]com
www.us03web-zoom[.]com
www.us03www-zoom[.]us
support.us05www-zoom[.]us
DNS Pivots
We’ll revisit 23.254.247[.]53 from the blog and include 23.254.226[.]83, found above.
We found 11 domains that began resolving to 23.254.247[.]53 after Validin’s blog post on June 20th, 2025. All of those domains are Zoom lookalike domains.
![Figure. Nearly a dozen new BlueNoroff-associated domains began resolving to 23.254.247[.]53 after Validin’s blog post on June 20, 2025. Figure. Nearly a dozen new BlueNoroff-associated domains began resolving to 23.254.247[.]53 after Validin’s blog post on June 20, 2025.](/images/pivots_revisited_summer_2025/image4.png)
Figure. Nearly a dozen new BlueNoroff-associated domains began resolving to 23.254.247[.]53 after Validin’s blog post on June 20, 2025.
The second IP, 23.254.226[.]83, discovered when repeating the filtered pivots from 8.8.8.8 on us02www-zoom[.]us, shows overlap with two additional unreported domains.
![Figure. Domains overlapping with us02www-zoom[.]us using a DNS IP pivot on 23.254.226[.]83 that have not yet been publicly attributed to BlueNoroff. Figure. Domains overlapping with us02www-zoom[.]us using a DNS IP pivot on 23.254.226[.]83 that have not yet been publicly attributed to BlueNoroff.](/images/pivots_revisited_summer_2025/image10.png)
Figure. Domains overlapping with us02www-zoom[.]us using a DNS IP pivot on 23.254.226[.]83 that have not yet been publicly attributed to BlueNoroff.
www[.]teams-meet[.]us
www[.]us004zoom[.]com
us02www-zoom[.]us
www[.]us04web[.]com
ww1[.]us04web[.]com
www[.]us005zoom[.]com
us005zoom[.]com
soporte[.]us05web-zoom[.]forum
www[.]us05zoom[.]com
us05zoom[.]com
www[.]us04www-zoom[.]us
us04www-zoom[.]us
us05zoom[.]us[.]com
Host Connection Pivots
From the original post, we identified several host connection pivots that served useful for discovering new BlueNoroff-associated domains names. We’ll test each of them here for efficacy.
Pivot 1: Domain name in RDP certificate, hwc-hwp-7982830. There were 3 IP addresses that shared this pivot. Looking at Validin’s certificate history, we see that this domain returned the name in the certificate for several weeks, then stopped being a useful pivot. Looking at the host responses for the IPs, it appears that the ports stopped responding to public connection requests around July 4, 2025.
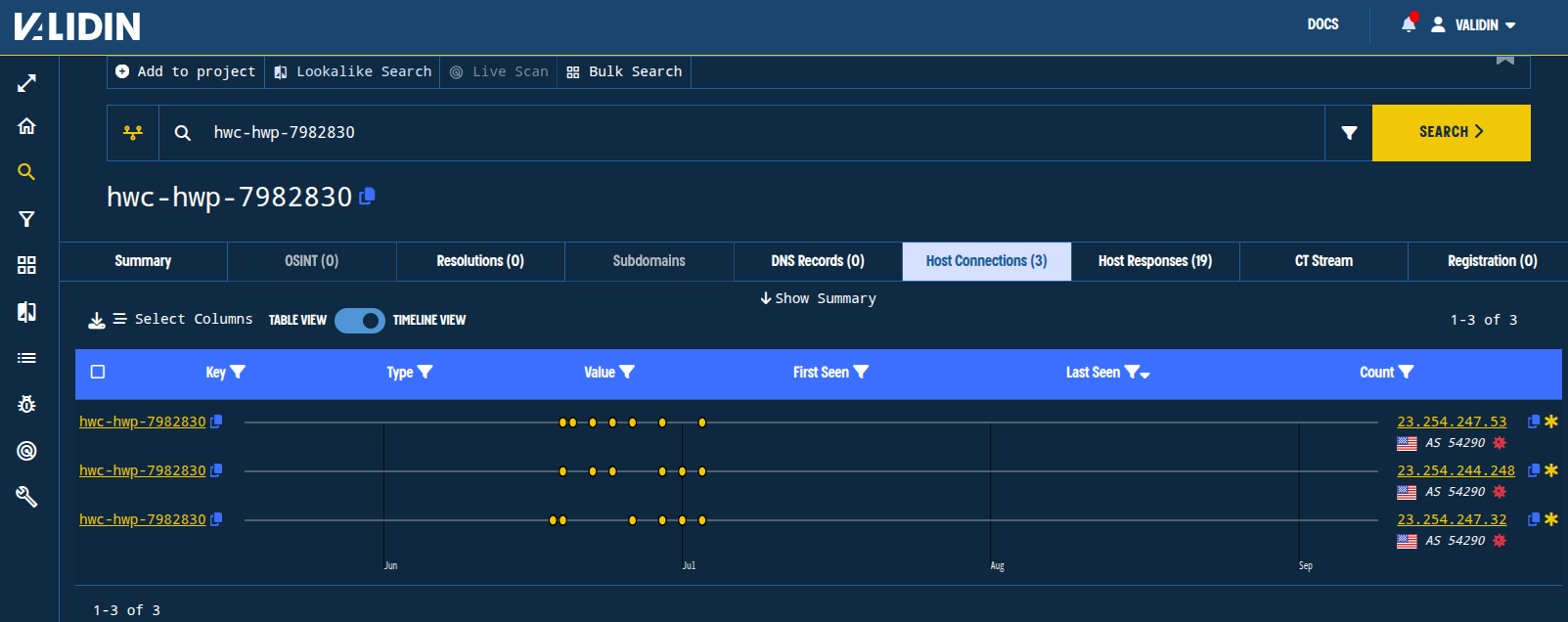
Figure. Validin observed this pivot for several weeks before the port 3389 was no longer publicly accessible on any of the reported IPs.
Pivot 2: HTTP certificate fingerprint 38eaff53184ebca9046c2f10161c664ceb10d0c1. This certificate SHA1 continues to be associated with the 3 IPs flagged in the original blog post as recently as September 5, 2025.
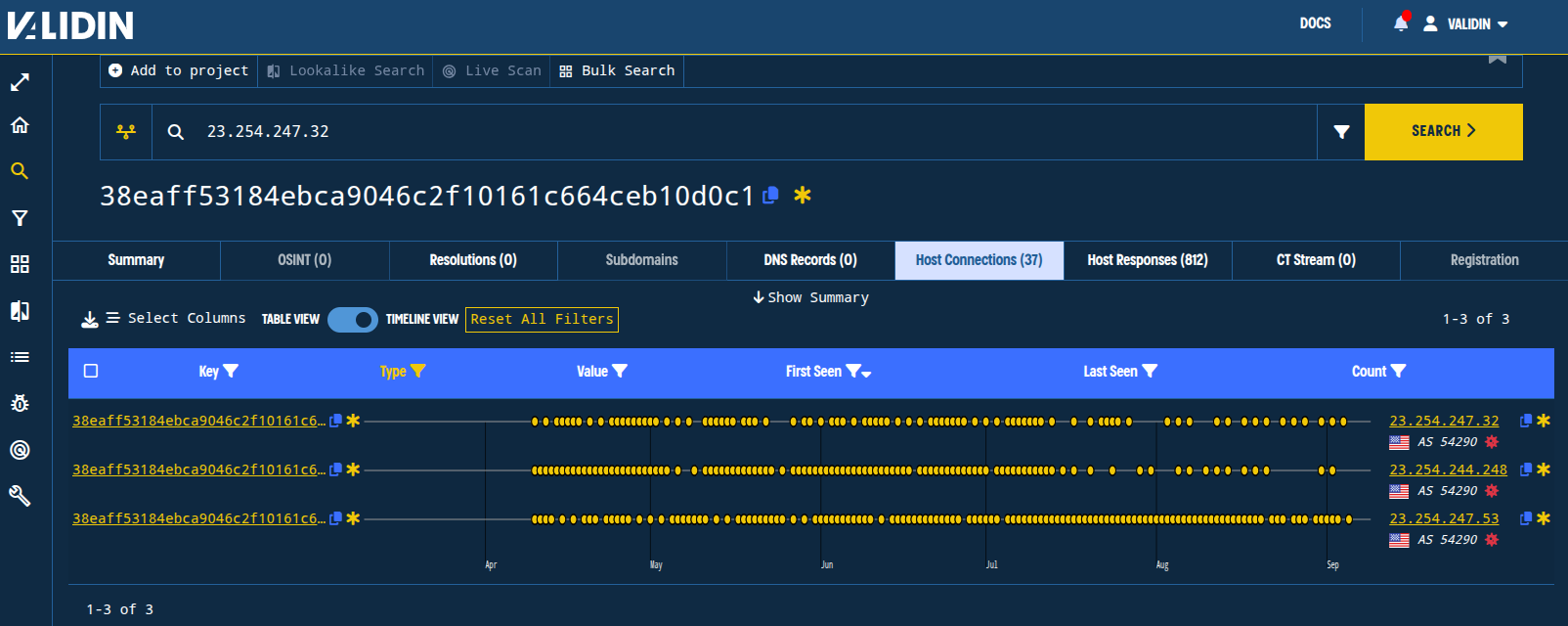
Figure. The HTTP certificate fingerprint results remain unchanged since our blog post on June 20, 2025.
However, the IP address that we discovered earlier, 23.254.226[.]83, started returning an RDP certificate with the domain hwc-hwp-9230840 on August 17, 2025. Pivoting on this IP yields several additional IP addresses that all appear recently active and each may have their own relevant threads to pull.
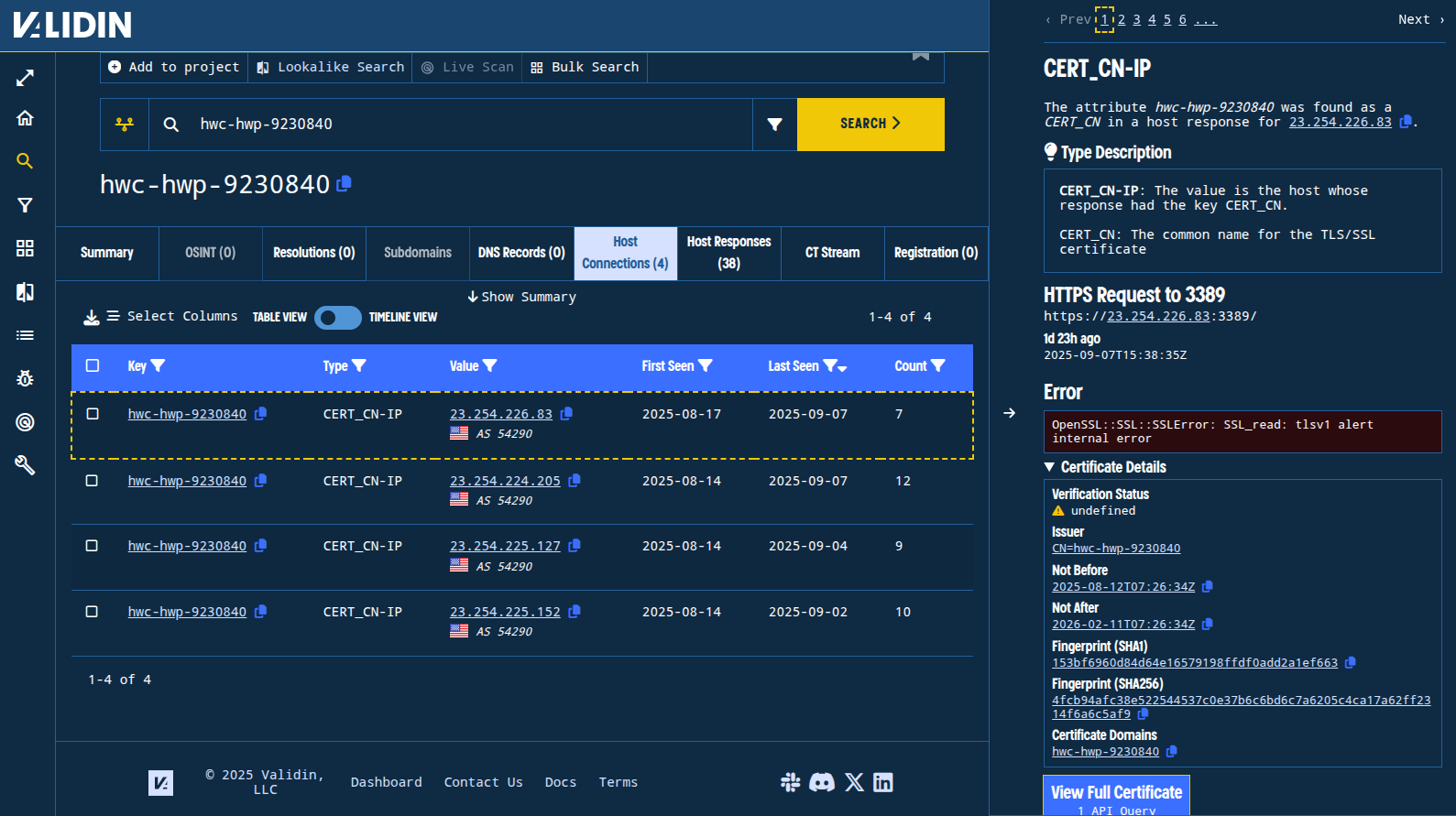
Figure. An RDP certificate pivot associated with one of the newly-associated IP addresses leads to several more potentially interesting IP addresses.
IP addresses:
23.254.224[.]20523.254.225[.]12723.254.225[.]15223.254.226[.]83
More DNS Pivots
In the original blog post, we pivoted from the IP addresses discovered in the other host response and DNS pivots and identified other potentially interesting domain names.
Two of these IP addresses, 23.254.225[.]152 and 23.254.225[.]127, have domains resolving to them with Web3 (cryptocurrency) themes in their names.
![Figure. Passive DNS history shows Web3-themed domains resolving to the IP 23.254.225[.]152 since August 20, 2025. Figure. Passive DNS history shows Web3-themed domains resolving to the IP 23.254.225[.]152 since August 20, 2025.](/images/pivots_revisited_summer_2025/image9.png)
Figure. Passive DNS history shows Web3-themed domains resolving to the IP 23.254.225[.]152 since August 20, 2025.
Web3-themed domains that resolved to 23.254.225[.]152, according to validin’s passive DNS history:
www[.]webthreefinance[.]club
www[.]web3journal[.]io
ww12[.]web3journal[.]io
www[.]web3insider[.]forum
web3journal[.]io
Web3-themed domains that resolved to 23.254.225[.]127, according to Validin’s passive DNS history:
www[.]whisperroom[.]forum
www[.]thorwsap[.]finance
app[.]thorwsap[.]finance
thorwsap[.]finance
Registration Pivots
Pivoting on the registration time from web3journal[.]io, we find two other web3 domains registered on Namecheap at exactly the same time:
web3journal[.]xyz
web3signal[.]xyz
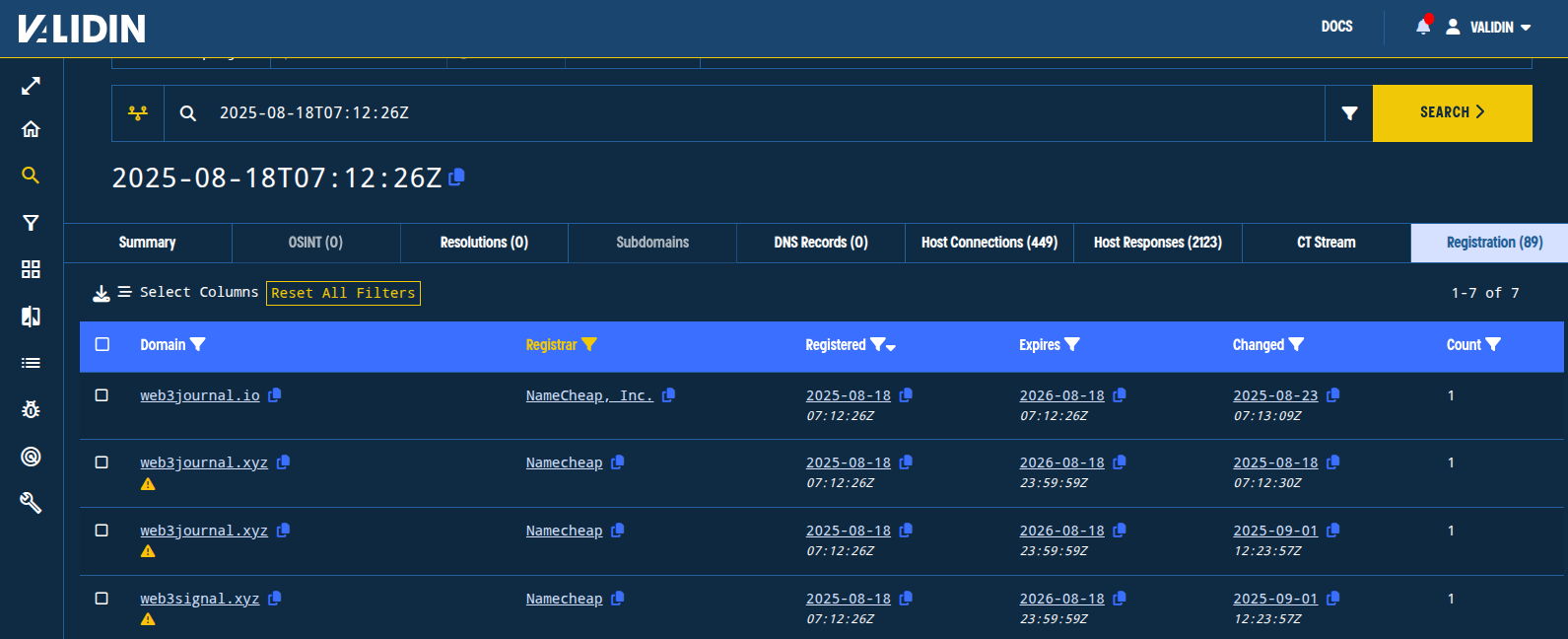
Figure. Web3-themed domains registered as a batch as seen with a registration time pivot in Validin.
Verdict
Most of the pivots or techniques replicated from the original blog post on June 20, 2025 yielded new and interesting pivots, including several domain names that are likely associated with BlueNoroff activities and haven’t been publicly reported. These pivots are still very relevant today.
Conclusion
Following the detailed, step-by-step processes for pivoting found in each of the 4 blogs we analyzed all resulted in connection to new indicators long after the posts were initially published. Many of the feature pivots and searches can still be monitored today to find new connections (monitoring pivots for changes is a feature of our enterprise platform), and all of the techniques discussed in our blog posts enabled reproducible results.
Ready to elevate your threat hunting, threat attribution, and incident response efforts? Whether you’re an individual analyst or part of a larger enterprise team, Validin offers solutions that meet your needs. Individual users can create a free account and self-upgrade to access more advanced features and data.
Part of a team? Contact us today to explore our enterprise options and discover how Validin can power your organizations with powerful tools and unparalleled data. Let Validin help you work smarter, faster, and more effectively in the fight against cyber threats.
