Finding Fake/Phishing Domains with HTTP Features in Validin
On average, every second of every day, Validin completes about 10,000 virtual host and IP host response measurements, enabling exceptionally broad understanding of the way that virtual hosts and IPs respond to HTTP and HTTPS requests. Threat analysts and researchers can leverage Validin’s outstanding coverage of the domain and IP space to amplify findings and quickly expand from known indicators to unknown, unreported, emerging and historic threats. This post highlights a few ways that analysts and researchers can expand knowledge of the threat landscape by amplifying HTTP features captured by Validin with real, recent examples.
MacOS ClickFix - Favicon Pivoting
The starting point for this pivot is this post on X: https://x.com/skocherhan/status/1943223111848964349
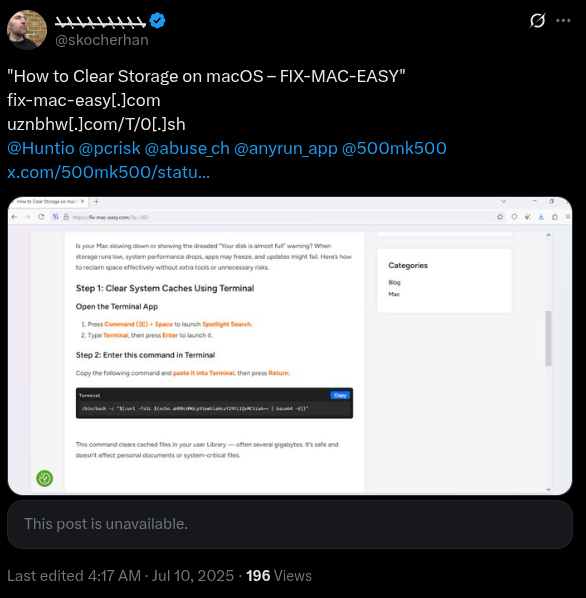
Figure 1. ClickFix campaign reported on X on July 10.
We start by searching for the domain fix-mac-easy[.]com in Validin and visiting the “Host Connections” tab. In this tab, Validin extracts HTTP/S response features from recent responses, including favicon, TLS, HTML, and HTTP banner features and fingerprints, and displays them as pivots. By using the “quick pivot” feature in the slideout, we discover a small number of potentially related domains that share the same favicon hash.
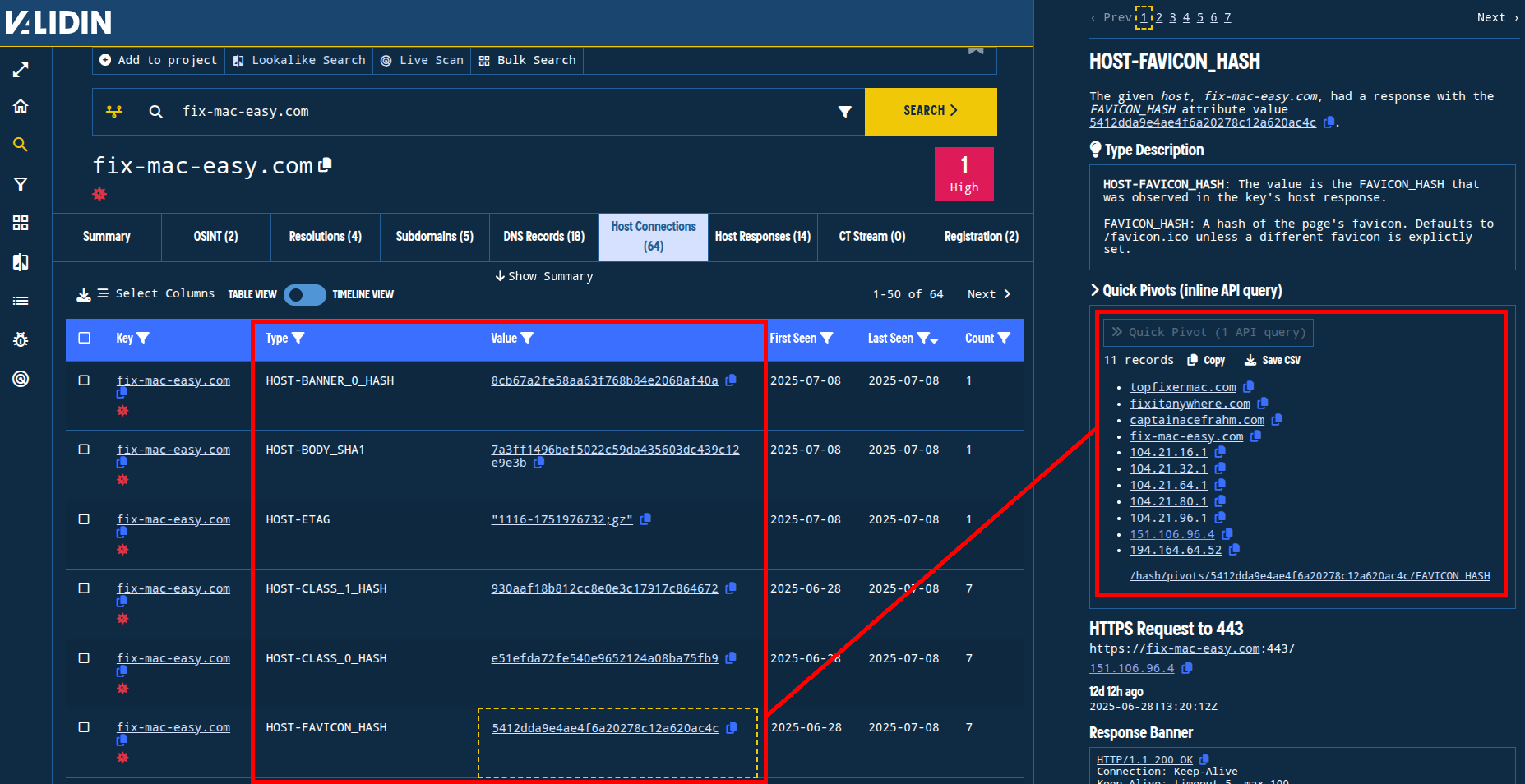
Figure 2. Identifying the favicon hash feature as a potentially good pivot.
Pivoting on the favicon hash 5412dda9e4ae4f6a20278c12a620ac4c, we find two unreported domain names, fixitanywhere[.]com and captainacefrahm[.]com, as well as the IPs 194.164.64[.]52 and 151.106.96[.]4, that have returned identical favicons.
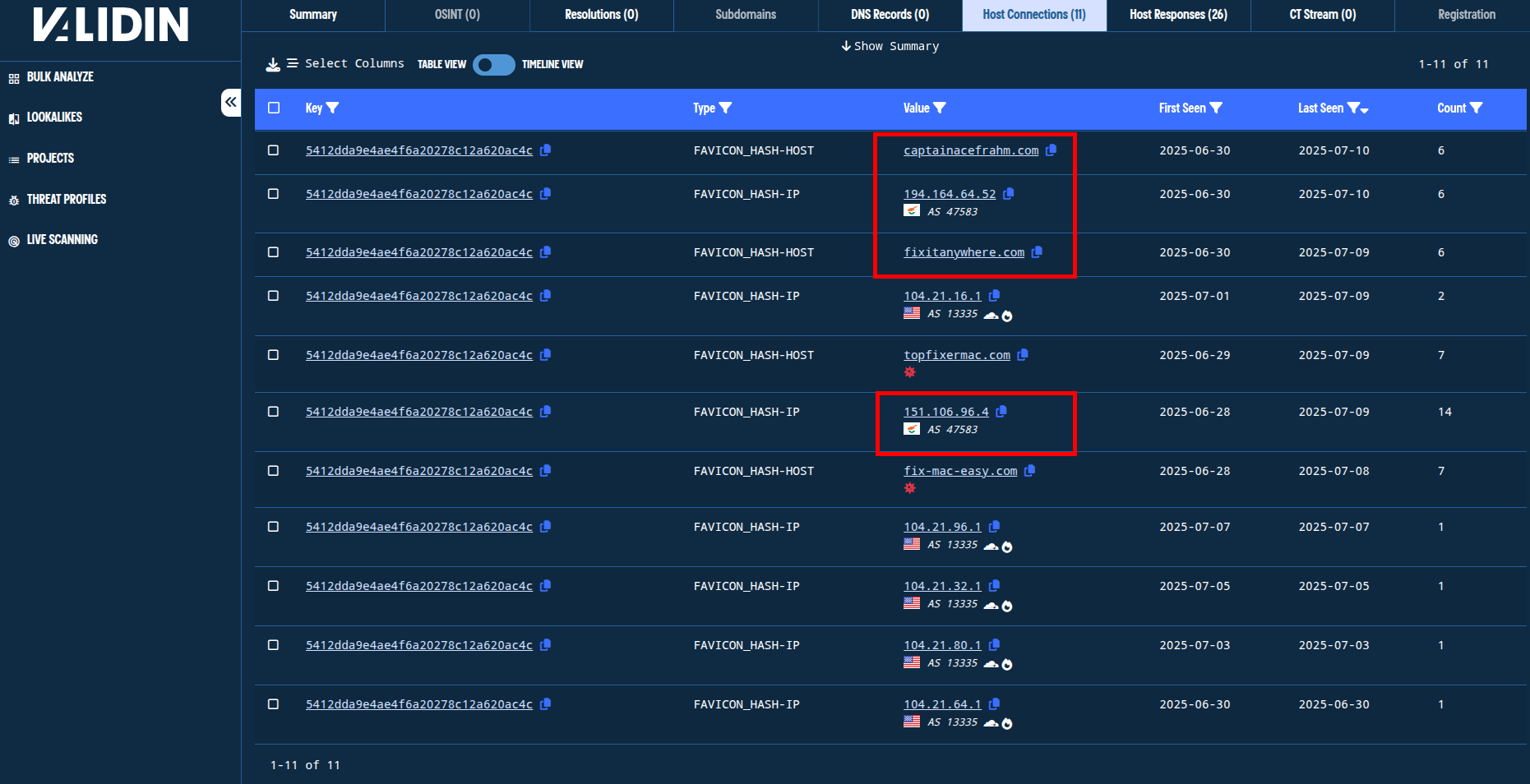
Figure 3. Pivoting from favicon hash shows related domain names and IP addresses.
These additional indicators have HTML title tags like “CAPTAIN MAC” and “FIX IT ANYWHERE” that show similarities to the title tag “FIX-MAC-EASY” observed in the initial search.
Phishing Redirectors - HTTP Header Pivoting
This pivot starts from this post on X: https://x.com/Sh4dow3x3/status/1943231391338008632
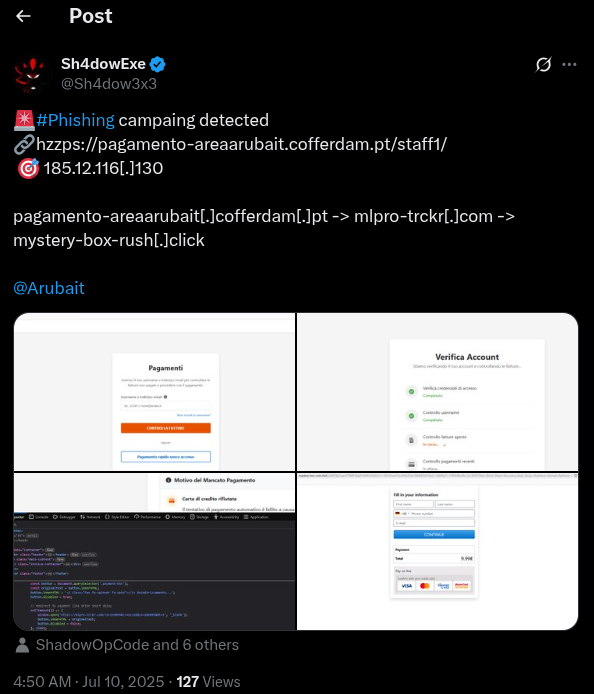
Figure 4. Fishing campaign reported on X by user Sh4dow3x3.
In this campaign, we note that the lure domain redirects to mlpro-trckr[.]com before finally redirecting to mystery-box-rush[.]click. One of the features Validin tracks is HTTP redirection (“Location:”) headers. By searching for mlpro-trckr[.]com in Validin, we can find other domains that are redirected to this domain via the “Host Connections” tab.
![Figure 5. Viewing other domains that were configured with HTTP redirects to mlpro-trckr[.]com. Figure 5. Viewing other domains that were configured with HTTP redirects to mlpro-trckr[.]com.](/images/http_feature_pivots/image5.png)
Figure 5. Viewing other domains that were configured with HTTP redirects to mlpro-trckr[.]com.
We can also discover other domains that are configured with very similar HTTP responses by looking at the HTTP response fingerprints, which validin records as “HOST-HEADER_HASH” and “HOST-BANNER_0_HASH.”
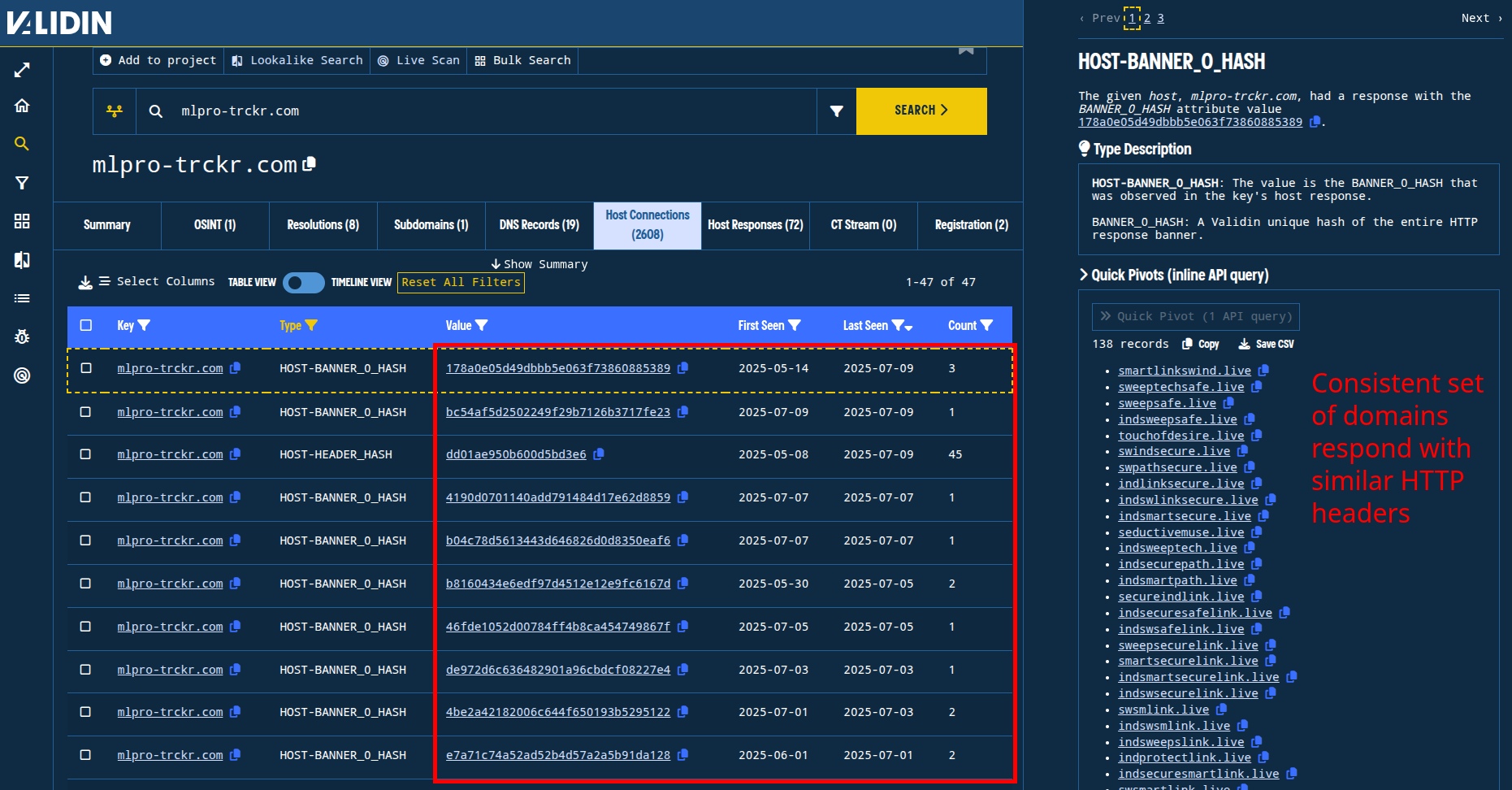
Figure 6. While the exact fingerprints have changed slightly over time, the domains that share these fingerprints remained consistent.
The HOST-HEADER_HASH fingerprints dd01ae950b600d5bd3e6, dd0175e9ae26da26f66e, and dd0130ee69ca5997b23f have been very consistent and are shared across a pool of only 72 other domains, including:
eml-pro[.]comml-pro-trckr[.]comsmlinksw[.]liveindsecurewin[.]livesweepsafe[.]live
Note: a full list of domains with this configuration is available at the end of this post.
These all appear to have been registered on Name.com, Inc. within the last year and their shared configuration patterns imply common management.
Malicious Extension C2 - HTTP Body Pivoting
The starting point for this pivot is from a Koi Security blog post describing malicious Chrome and Edge browser extensions. That blog post highlights domains used for command and control by malicious browser extensions, including:
admitab[.]comedmitab[.]comclick.videocontrolls[.]comc.undiscord[.]comclick.darktheme[.]netc.jermikro[.]comc.untwitter[.]comc.unyoutube[.]netadmitclick[.]netaddmitad[.]comadmiitad[.]comabmitab[.]comadmitlink[.]net
From the “Host Responses” tab for click.videocontrolls[.]com, we can see the HOST-BODY_SHA1 pivot has an estimated 9.1k total connections, and that the “quick pivot” finds a small number of other domains, including many that are on the original indicator list.
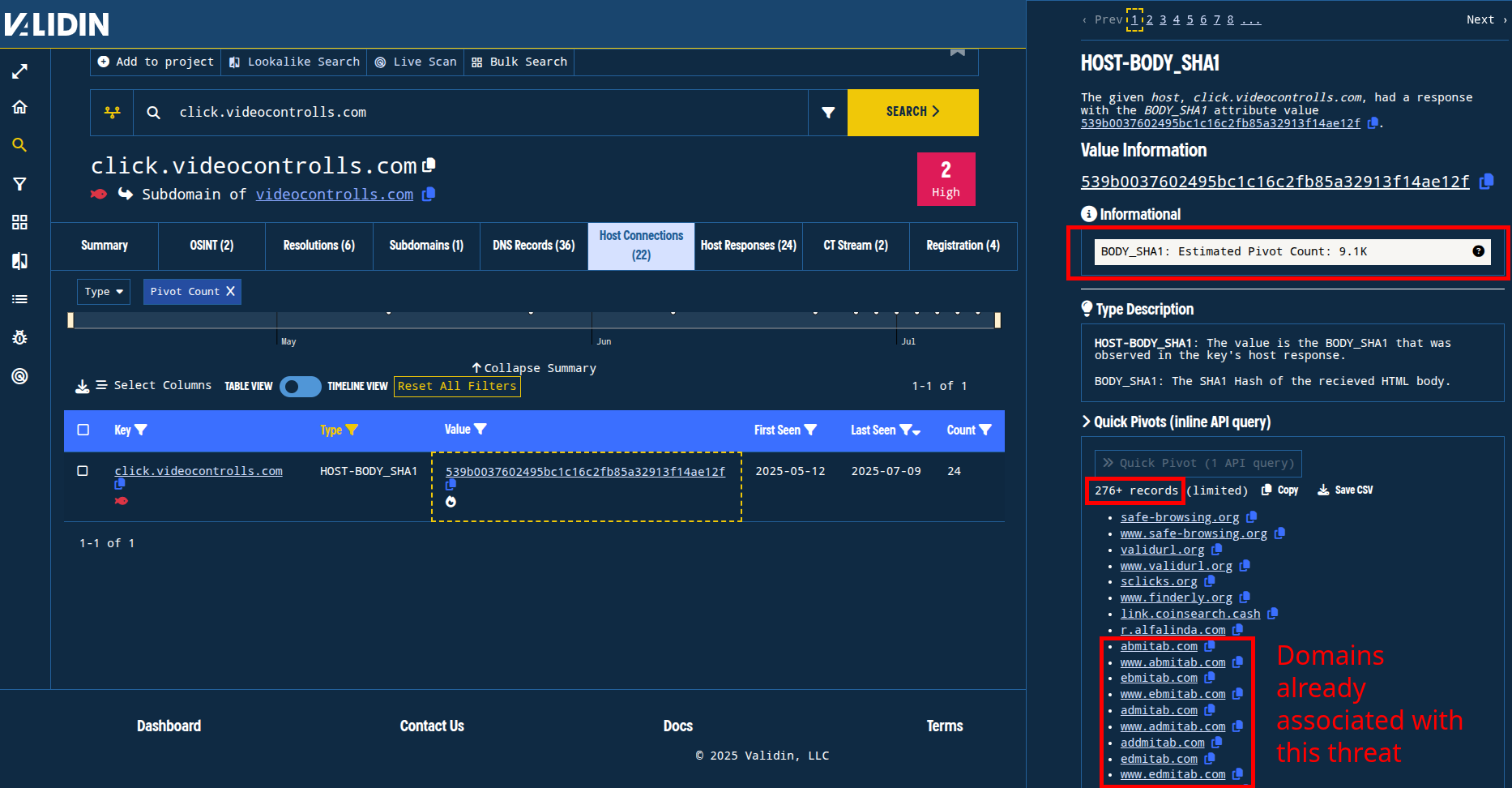
Figure 7. Quickly pivoting on HTTP body hash finds related domain names.
This HTML SHA1 hash 539b0037602495bc1c16c2fb85a32913f14ae12f is the following text:
<html><head><title>404 Not Found</title></head><body bgcolor=“white”><center><h1>404 Not Found</h1></center><hr><center>nginx/0.5.35</center></body></html>
This pivot yields little less than 300 other domains that might be associated with other malicious browser extensions or are being staged for future use.
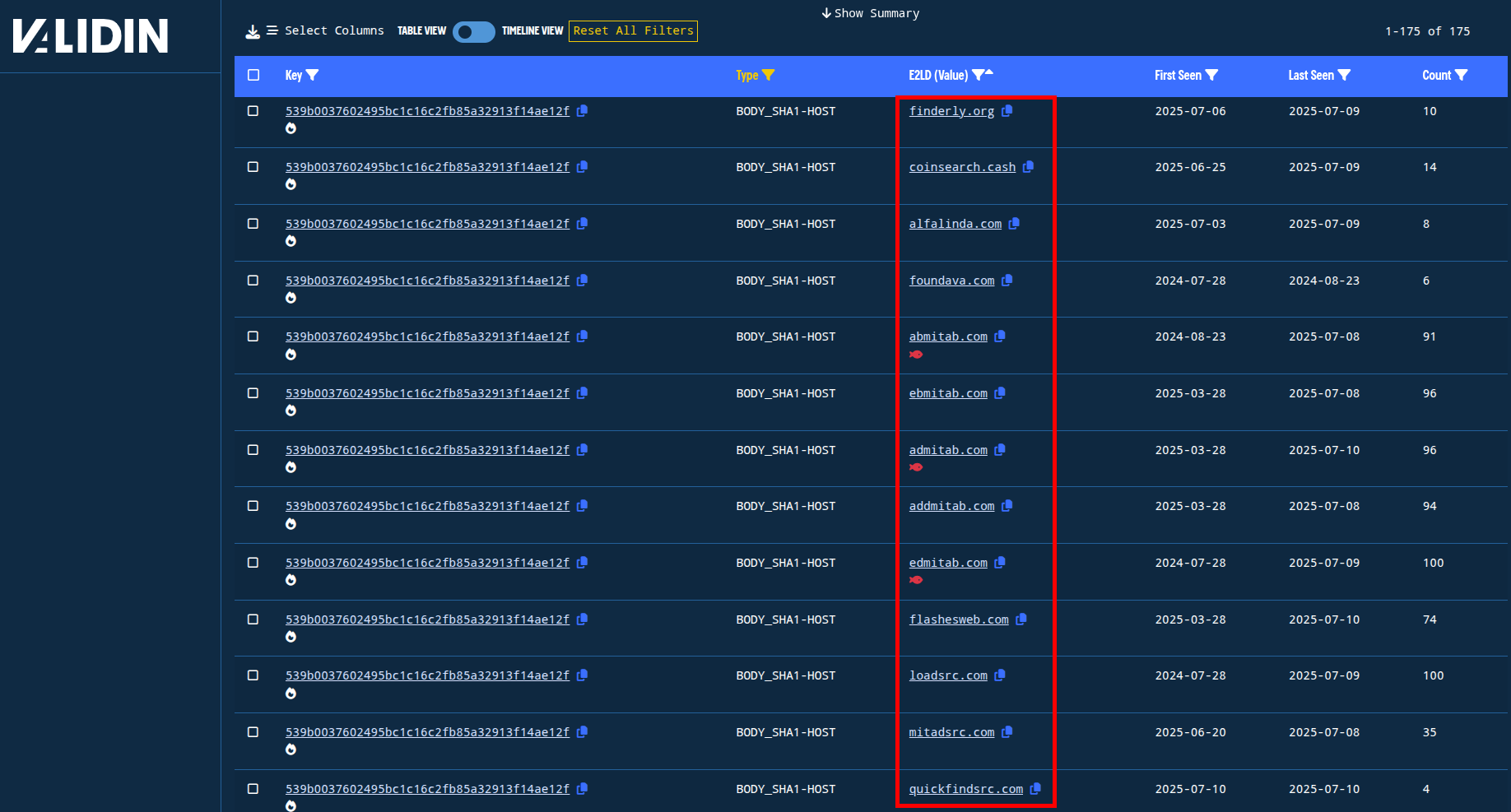
Figure 8. HTTP body SHA1 pivot showing other domains with identical responses.
Domains with this body hash include:
superiorurl[.]netquickfindsrc[.]comlinkfindr[.]comexplorelink[.]net
Note: a full list of domains sharing this pivot is available at the end of this post.
Fake Apps Download - HTML Title Pivots
The starting point for this last pivot is this post on X by @motuariki_ with the pivot identified by @500mk500:
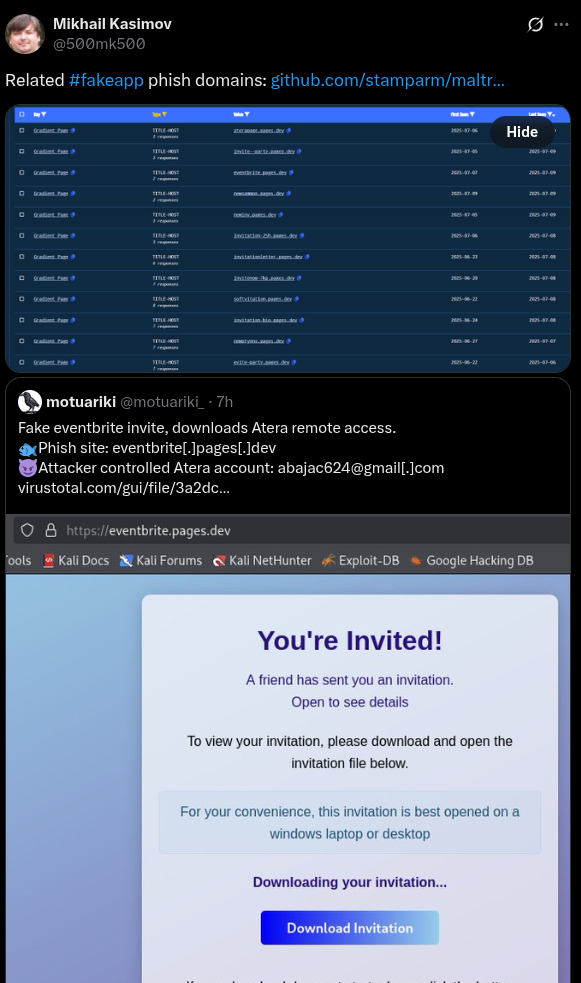
Figure 9. X post showing a fake eventbrite invitation that prompts a download of the Altera remote access tool.
By searching for the string “Gradient Page” in Validin, we can find 22 domains that share that title tag. A full evaluation of the responses indicates that they are all related.
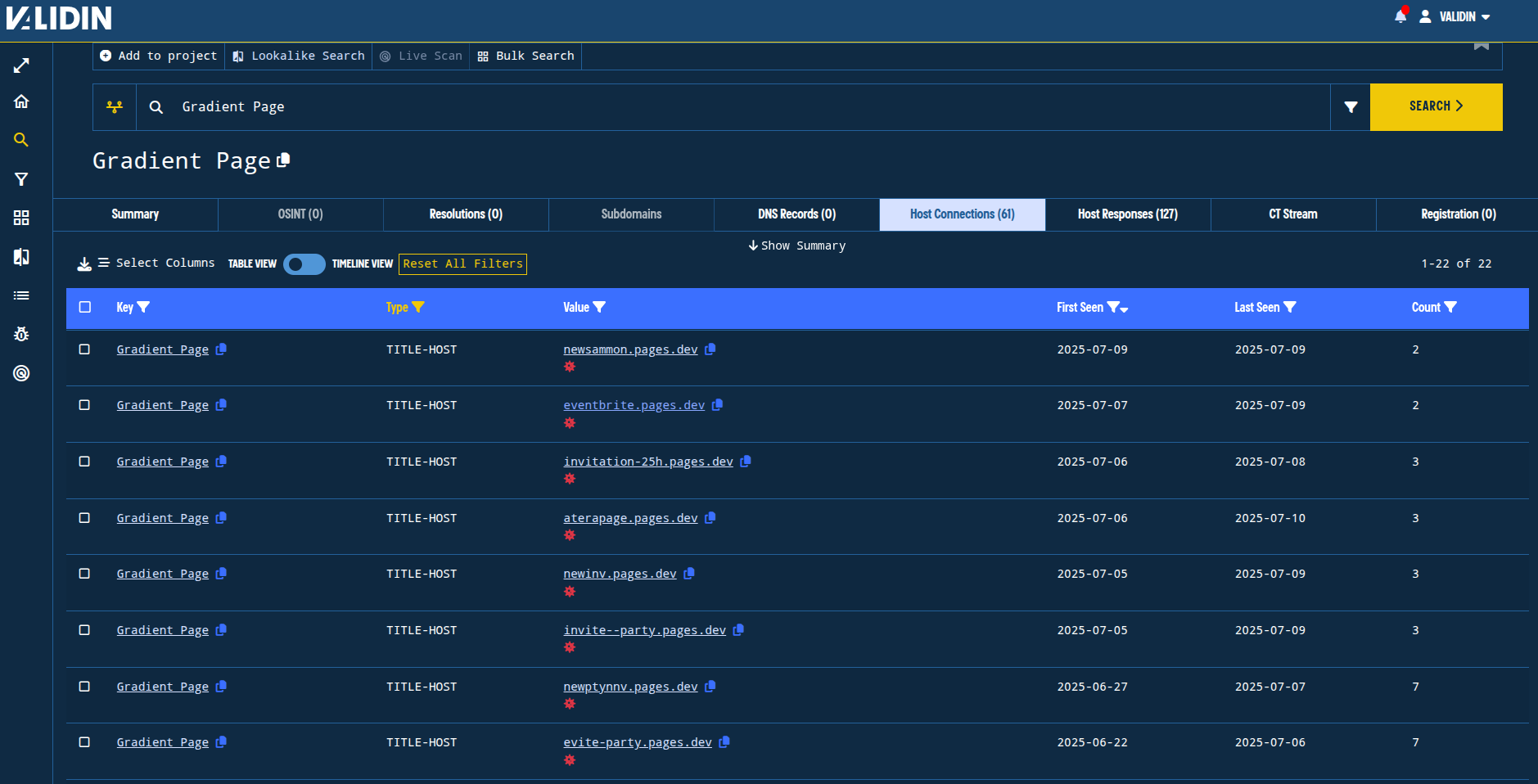
Figure 10. HTML title tag pivot in Validin helps discover other domains used for fake app downloads.
Conclusion
This post highlights some of the many ways to leverage Validin’s comprehensive virtual host responses and feature pivoting to enable malicious infrastructure hunting. Using these techniques, analysts can quickly, proactively, and comprehensively build intelligence to block and detect the threats most relevant to their organizations.
Ready to level up your threat hunting, threat attribution, and incident response efforts? Validin’s premium individual and enterprise solutions offer powerful tools, affordable pricing, and unparalleled insights to help your team work smarter and faster.
Contact us today to explore enterprise options and see how Validin can empower your threat intelligence team.
Indicators
fixitanywhere[.]com
captainacefrahm[.]com
topfixermac[.]com
194.164.64[.]52
151.106.96[.]4
dd0130ee69ca5997b23f
dd0175e9ae26da26f66e
dd01ae950b600d5bd3e6
betdownload[.]live
smartlinkswind[.]live
sweeptechsafe[.]live
sweepsafe[.]live
indsweepsafe[.]live
touchofdesire[.]live
swindsecure[.]live
swpathsecure[.]live
indlinksecure[.]live
indswlinksecure[.]live
indsweepsecure[.]live
indsmartsecure[.]live
seductivemuse[.]live
indsweeptech[.]live
indsecurepath[.]live
indsmartpath[.]live
secureindlink[.]live
indsecuresafelink[.]live
indswsafelink[.]live
sweepsecurelink[.]live
smartsecurelink[.]live
indsmartsecurelink[.]live
indswsecurelink[.]live
swsmlink[.]live
indswsmlink[.]live
indsweepslink[.]live
indprotectlink[.]live
indsecuresmartlink[.]live
swsmartlink[.]live
indswsmartlink[.]live
indswlink[.]live
safeswlink[.]live
indsafeswlink[.]live
indsecureswlink[.]live
indsmartswlink[.]live
securelinksm[.]live
indsecurelinksm[.]live
indswsecurelinksm[.]live
swlinksm[.]live
indswlinksm[.]live
indsweepsm[.]live
indsecurewin[.]live
smartindsweep[.]live
safelinksweep[.]live
indsmartsweep[.]live
linkssweeps[.]live
secretwhispers[.]live
safelinkforws[.]live
indsafelinkforws[.]live
securelinksws[.]live
indsecurelinksws[.]live
indswsecurelink-dt[.]live
indswsecurelinkdt[.]live
swsmlinkdt[.]live
indswsmlinkdt[.]live
indswlinkdt[.]live
indsweepsmdt[.]live
indswsmartdt[.]live
indsmartswdt[.]live
indsafesmart[.]live
indswsmart[.]live
secureindsw[.]live
safesw[.]live
indsecuresw[.]live
indsafelinksw[.]live
indsecurelinksw[.]live
smlinksw[.]live
indsmlinksw[.]live
indsmartlinksw[.]live
indsmartsw[.]live
eml-pro[.]com
mlpro-trckr[.]com
cashe-valid[.]org
validspace[.]org
validcashe[.]org
safe-browsing[.]org
validurl[.]org
hyperurl[.]org
linkprovider[.]org
sclicks[.]org
extratools[.]org
srcquest[.]org
finderly[.]org
coinsearch[.]cash
alfalinda[.]com
foundava[.]com
abmitab[.]com
ebmitab[.]com
admitab[.]com
addmitab[.]com
edmitab[.]com
flashesweb[.]com
loadsrc[.]com
mitadsrc[.]com
quickfindsrc[.]com
lablesrc[.]com
abmisrc[.]com
findedmisrc[.]com
clinsrc[.]com
src-load[.]com
check-load[.]com
uiload[.]com
progappload[.]com
standbyload[.]com
getadtad[.]com
admiitad[.]com
abmitad[.]com
addmitad[.]com
edmitad[.]com
tabbbed[.]com
loadchecked[.]com
linkvalid[.]com
chathamand[.]com
urglinkfind[.]com
clickbyfind[.]com
prodfound[.]com
bysourcefound[.]com
linkjohanfound[.]com
jooyfound[.]com
boostmysound[.]com
twitchadguard[.]com
undiscord[.]com
huperspace[.]com
link-fluence[.]com
static-resource[.]com
findlinksource[.]com
pipmode[.]com
expire-cashe[.]com
bonyture[.]com
onlyjuse[.]com
preload-site[.]com
goloadersite[.]com
loadbysite[.]com
loadingprog[.]com
gomainprog[.]com
linkadmi[.]com
srcedmi[.]com
toolsbytrack[.]com
domtoolsrtack[.]com
clickscheck[.]com
tools-click[.]com
standclick[.]com
edmiclick[.]com
admitclick[.]com
gourgelick[.]com
geturlnick[.]com
insrc-link[.]com
planet-link[.]com
eddmilink[.]com
hublosk[.]com
valid-url[.]com
validate-url[.]com
aviabilityurl[.]com
bysourceprem[.]com
suppdomain[.]com
domtoolsgo[.]com
jermikro[.]com
gosourcepro[.]com
brinato[.]com
vksaveapp[.]com
linkfindr[.]com
url-loader[.]com
sitepreloader[.]com
locatelinker[.]com
untwitter[.]com
tabrr[.]com
gositeloads[.]com
mainloads[.]com
domfounds[.]com
trubclocks[.]com
mitadlinks[.]com
videocontrolls[.]com
src-tools[.]com
findloudtools[.]com
standprogress[.]com
mkerookets[.]com
savevideoplus[.]com
url-exist[.]com
gostartserv[.]com
explorenex[.]com
standprogby[.]com
findsrc[.]net
foundsrc[.]net
spacesrc[.]net
urgegosrc[.]net
standbysrc[.]net
sitebysrc[.]net
toolsbysrc[.]net
lingsc[.]net
checksc[.]net
checkload[.]net
linksload[.]net
cachevalid[.]net
garryfloid[.]net
toolsfind[.]net
matchfound[.]net
clickfound[.]net
yourfound[.]net
unyoutube[.]net
validationspace[.]net
srcservice[.]net
livebrance[.]net
mikesource[.]net
matchsource[.]net
clicksource[.]net
suppsource[.]net
pilotrole[.]net
darktheme[.]net
cacheexpire[.]net
spacevalidate[.]net
prerender-site[.]net
linkloadsite[.]net
clickbysite[.]net
srcing[.]net
urling[.]net
heresearch[.]net
glowsrctrack[.]net
foundtrack[.]net
click-check[.]net
urlcheck[.]net
requestcheck[.]net
admitclick[.]net
check-link[.]net
explorelink[.]net
admitlink[.]net
check-url[.]net
click-url[.]net
spaceurl[.]net
superiorurl[.]net
findsrcdom[.]net
prowagon[.]net
load-down[.]net
api-resources[.]net
urclicks[.]net
uclicks[.]net
premlinks[.]net
srcfindtools[.]net
maintools[.]net
usdelivers[.]net
purplemat[.]net
rdrect[.]net
cdn-javascript[.]net
arequest[.]net
jullyambery[.]net
rquery[.]net
dataprovider[.]biz
istat[.]biz
newsammon.pages[.]dev
eventbrite.pages[.]dev
invitation-25h.pages[.]dev
aterapage.pages[.]dev
newinv.pages[.]dev
invite--party.pages[.]dev
newptynnv.pages[.]dev
evite-party.pages[.]dev
softvitation.pages[.]dev
special-invitation-7dh.pages[.]dev
inviteletr.pages[.]dev
pbinvitaton.pages[.]dev
freshpbinv.pages[.]dev
newpb.pages[.]dev
invitationletter.pages[.]dev
pbinvitationnew.pages[.]dev
invitenow-7kp.pages[.]dev
invitation-bio.pages[.]dev
pbinvitation.pages[.]dev
invitenow.pages[.]dev
newinvitation.pages[.]dev
invprocess.pages[.]dev