How to use the Validin UI and host responses to find related infrastructure quickly
X User @JAMESWT_WT posted the following tweet on April 8th about a site impersonating Booking.com that was related to an ongoing ClickFix campaign. Visiting this Booking.com themed page leads to a redirector that downloads executables from the IP address 92.255.85[.]66 and installs the well-known Remote Access Trojan AsyncRAT. In this post, I’ll use Validin’s current and historic host response data to uncover related Booking.com themed domains.
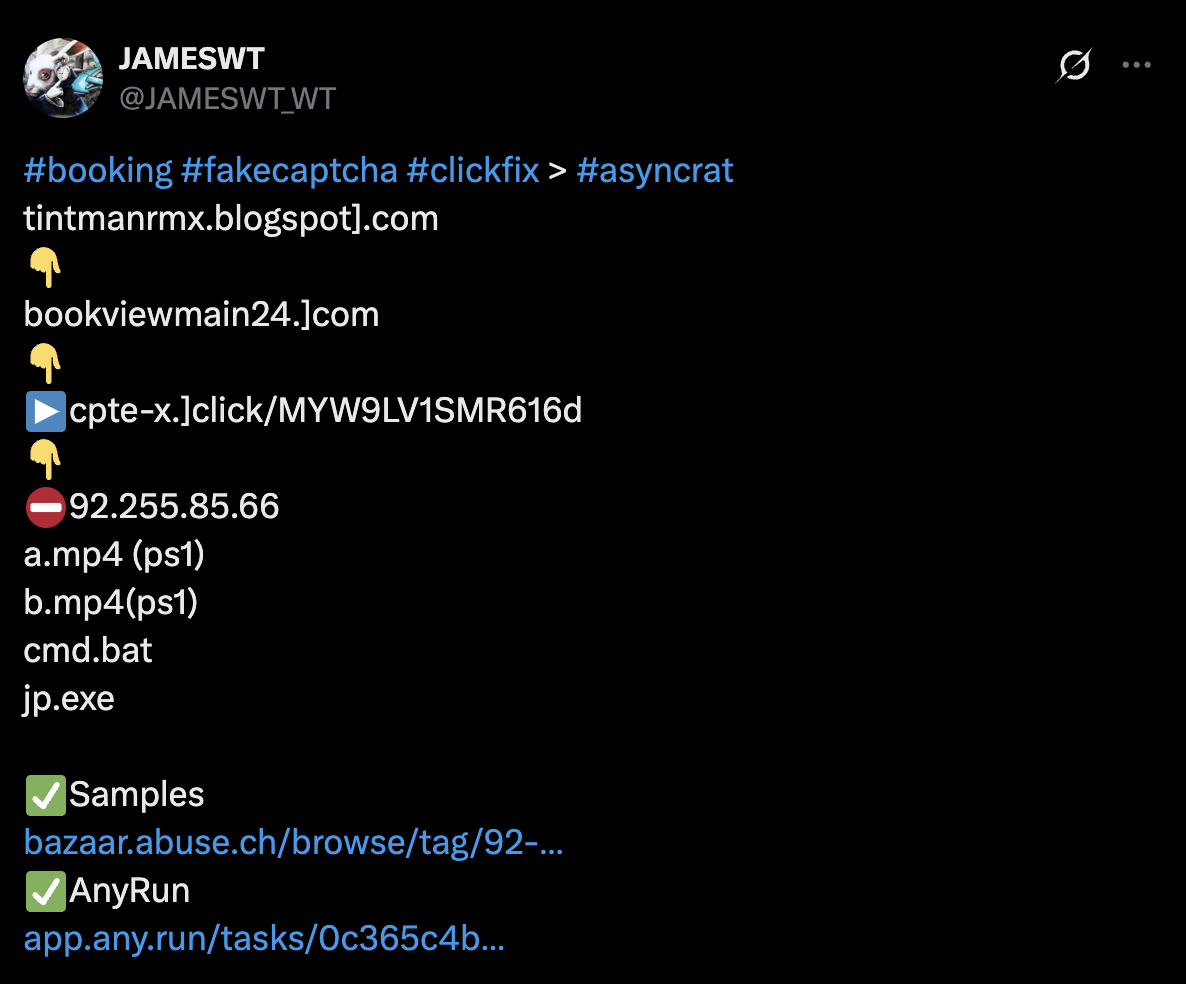
Figure 0. Original tweet that led to this investigation.
Initial Investigation
We begin this investigation with a handful of known domains and IPs, as highlighted in the tweet above:
tintmanrmx.blogspot[.]com
bookviewmain24[.]com
cpte-x[.]click
92.255.85[.]66
Starting with the phishing domain bookviewmain24[.]com, we see that Validin has observed this domain several times, but some responses are protected by a Cloudflare turnstile. However, for a handful of observations, Validin successfully fetched pages with the title, Booking.com. We also have the registration information for bookviewmain24[.]com showing that the domain was registered earlier this month on WEBCC.
![Figure 1. Host Response Data for bookview24[.]com Figure 1. Host Response Data for bookview24[.]com](/images/booking_themed_clickfix/image15.png)
Figure 1. Host Response Data for bookview24[.]com
![Figure 2. Registration summary for bookview24[.]com Figure 2. Registration summary for bookview24[.]com](/images/booking_themed_clickfix/image1.png)
Figure 2. Registration summary for bookview24[.]com
Pivoting on Title Tag
We continue our investigation by pivoting off the title Booking.com to see what other pages had this title.
Note: The default search for Validin will treat Booking.com as a domain. To search Booking.com as a title: expand the search filters next to the “Search” button and override the type to “String”.
This search finds a total of 795 connections. We apply a result filter on the “Type” column to only include domains where Booking.com as a title and also apply a “Value” filter to eliminate known legitimate Booking.com domains, resulting in 236 domains.
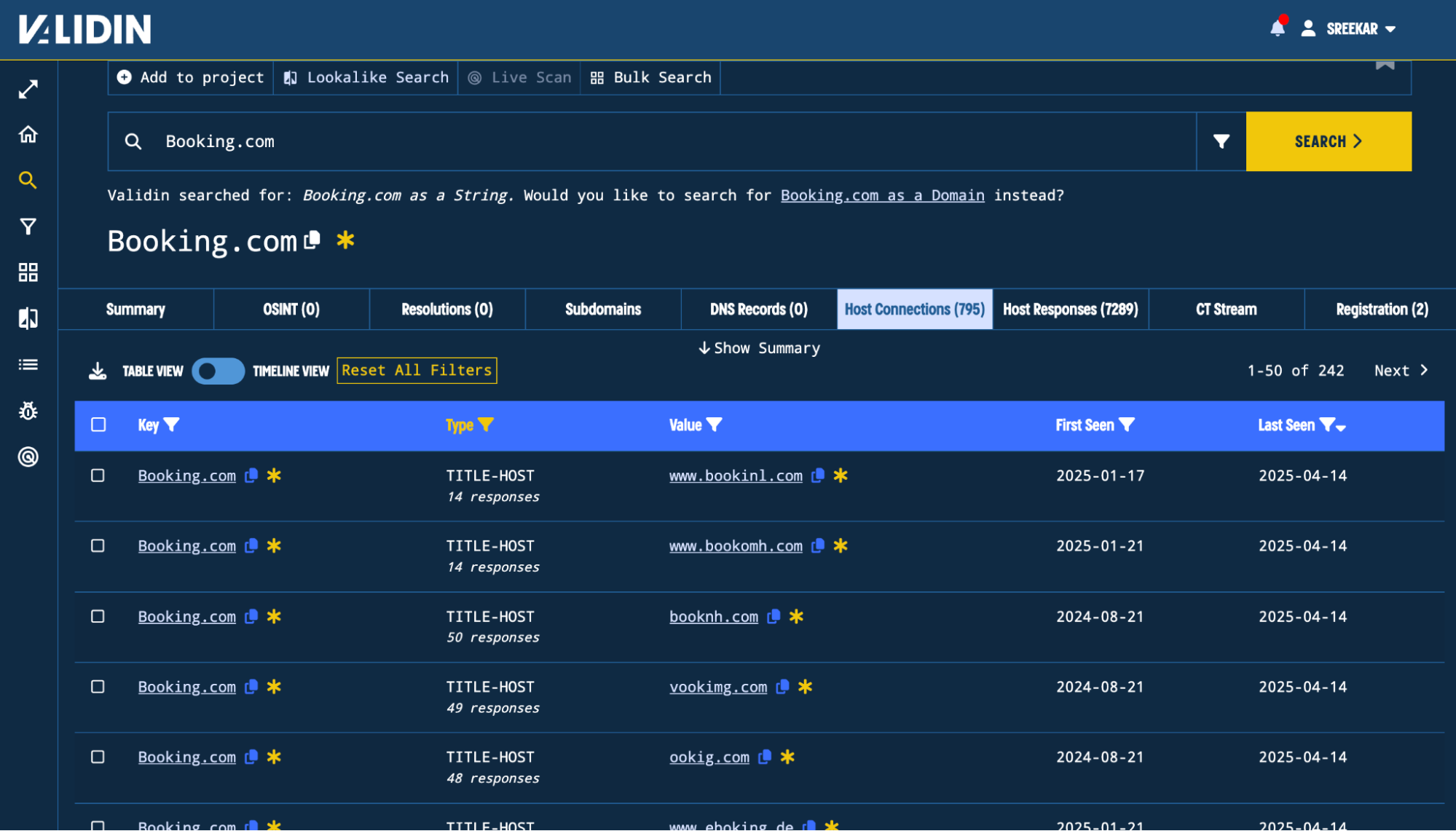
Figure 3. Domains where Booking.com is a title
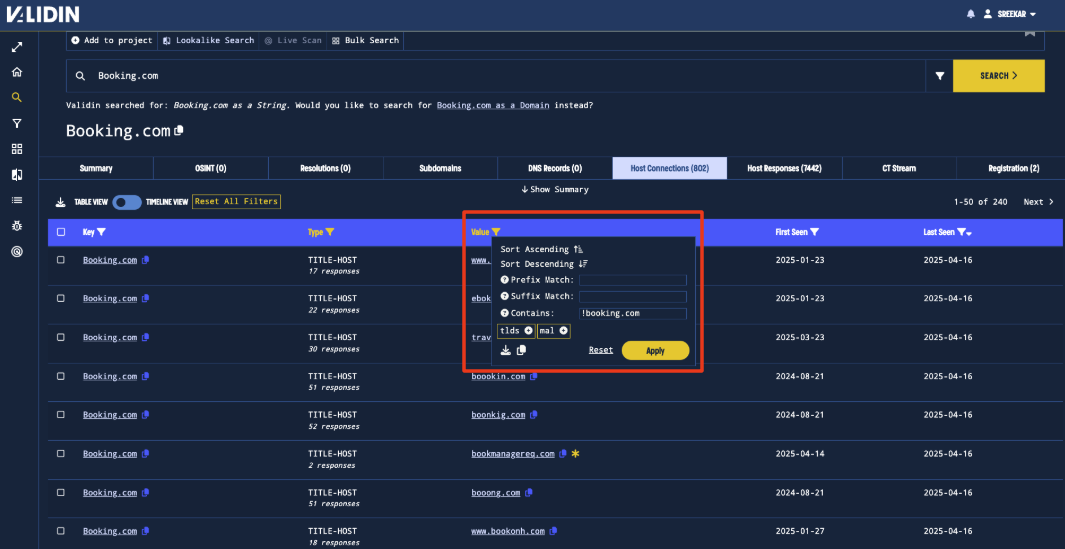
Figure 4. Value Filter to exclude domains that are actually Booking.com domains
Validating Domains
Looking at all the domains we found, there is a common theme: almost all of them look like typos of Booking.com.
We need to validate that most of these domains are actually phishing, so we start by looking at the registration times. Opening the slideout, we fetch the registration details and see that most of the domains were actually registered many years ago and they’re all registered on Dynadot. (Aged domains are typically less likely to host malicious content.) We pivot on another one of these domains and see that it’s hosted on an Hetzner IP, which is different from our original domain (which was hosted on Cloudflare).
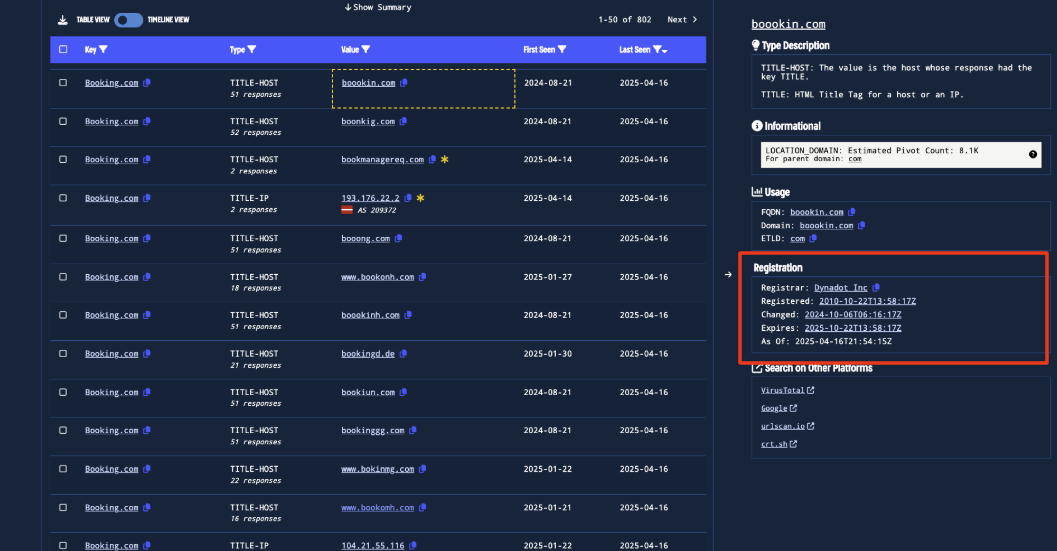
Figure 5. Registration Information for some Booking.com suspected phishing domains
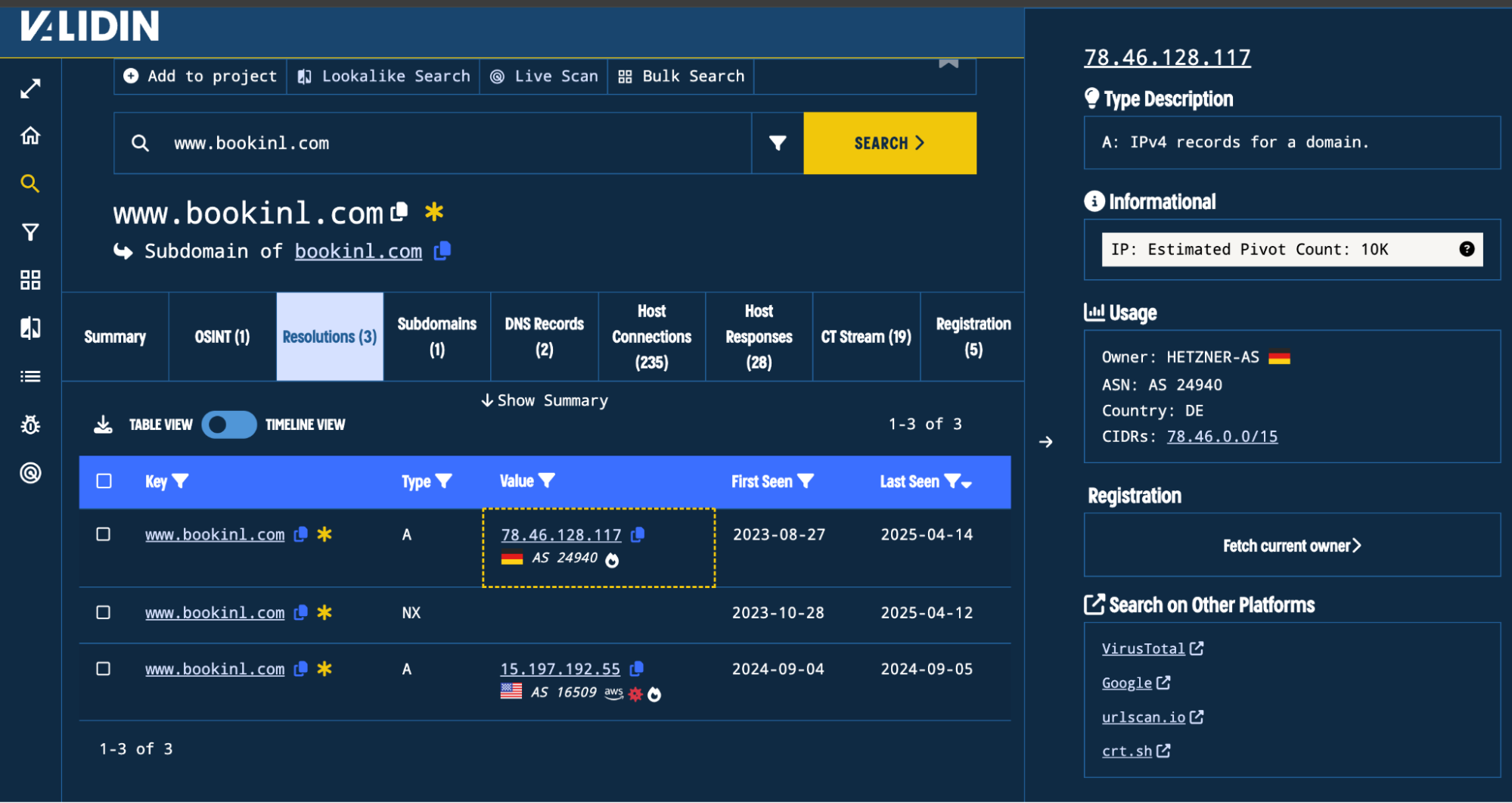
Figure 6. Showing hosting on a Hetzner ASN for phishing site
The fact that many of these domains were registered 9+ years ago, are all registered on Dynadot, and are all hosted on the same Hetzner IP suggests that many of these typosquatting domains were preemptively registered by Booking.com to prevent phishing attempts. Further, they all share a valid certificate that includes all these aged domains.
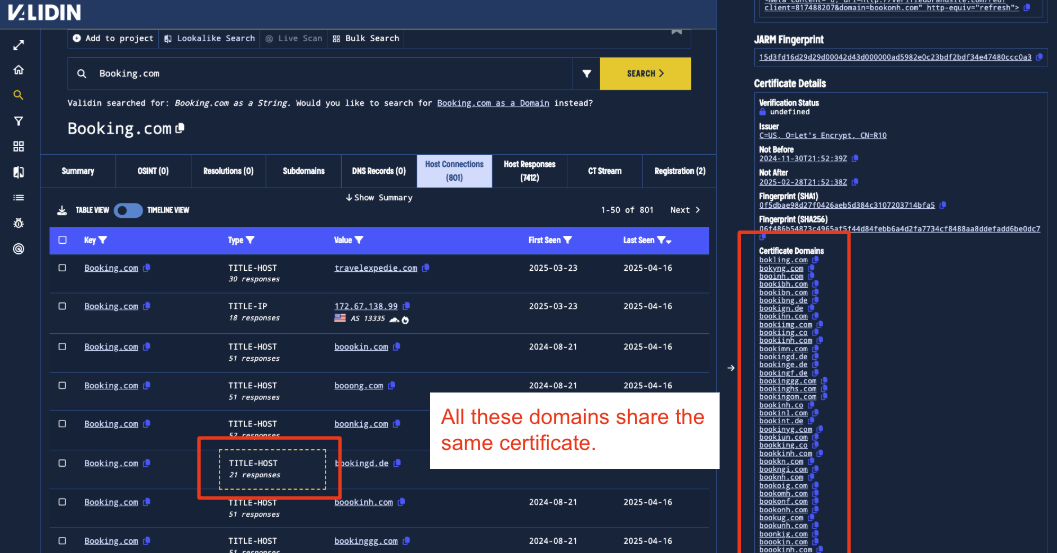
Figure 7. All the Booking.com domains are on the same certificates.
Alternatively, some of the domains in the subset use the same registrar as the original domain.
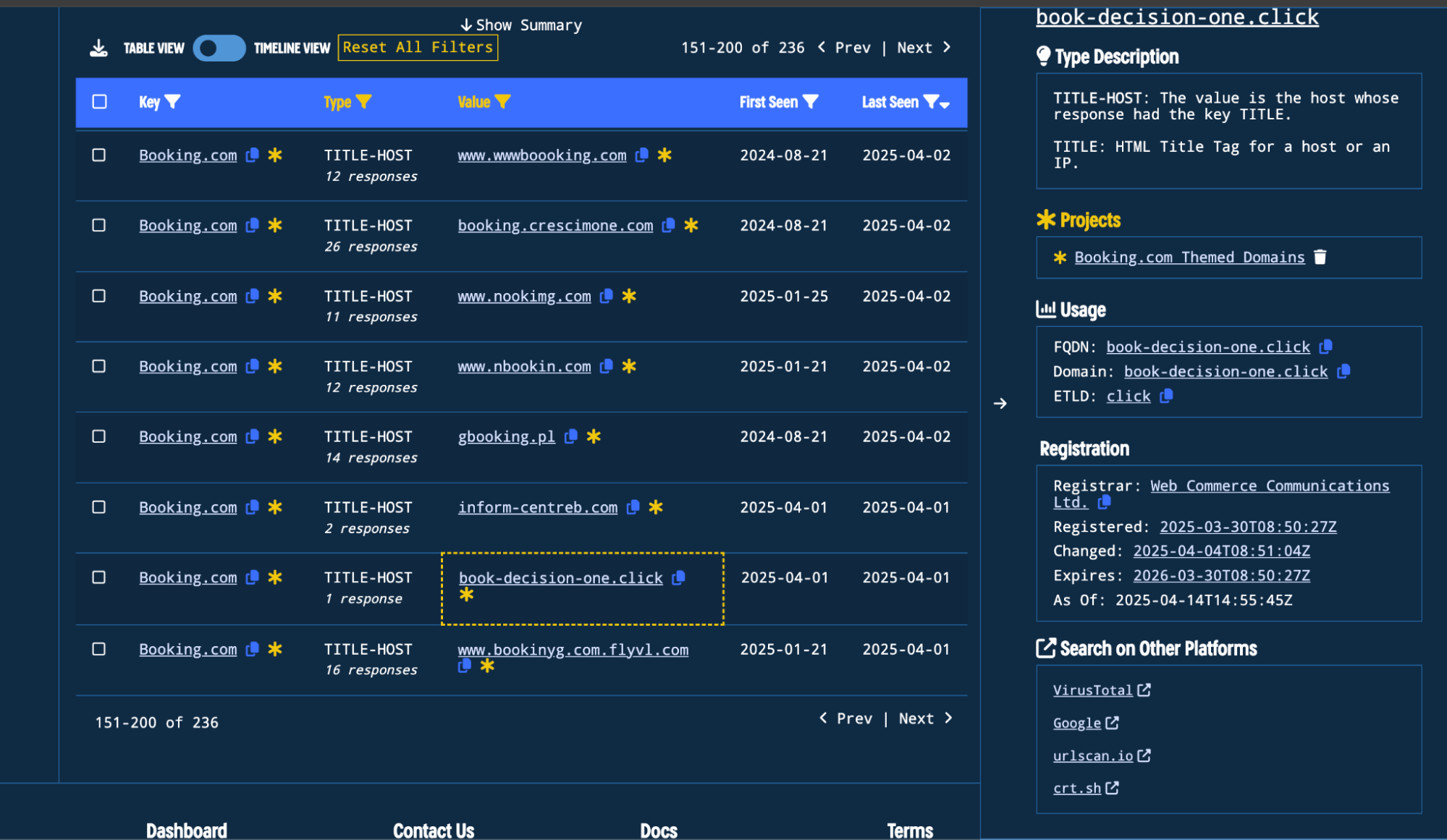
Figure 7. Example of a Booking.com themed domain that uses the “Web Commerce Communications” registrar.
I’ll add the domains that use WEBCC as the registrar and are hosted on Cloudflare to our result set.
Pivoting on Hashes
Knowing that the Title Tag includes false positives, I’ll look for other features that are better indicators of relatedness to the original domain, bookviewmain24[.]com.
Validin creates content hashes to provide additional fingerprinting of the content returned by domains and IPs. Validin assembles fingerprints numerous attributes and structure of webpages with the goal of finding reuse of tooling and templates, e.g. CSS, HTML, or HTTP Server configurations.
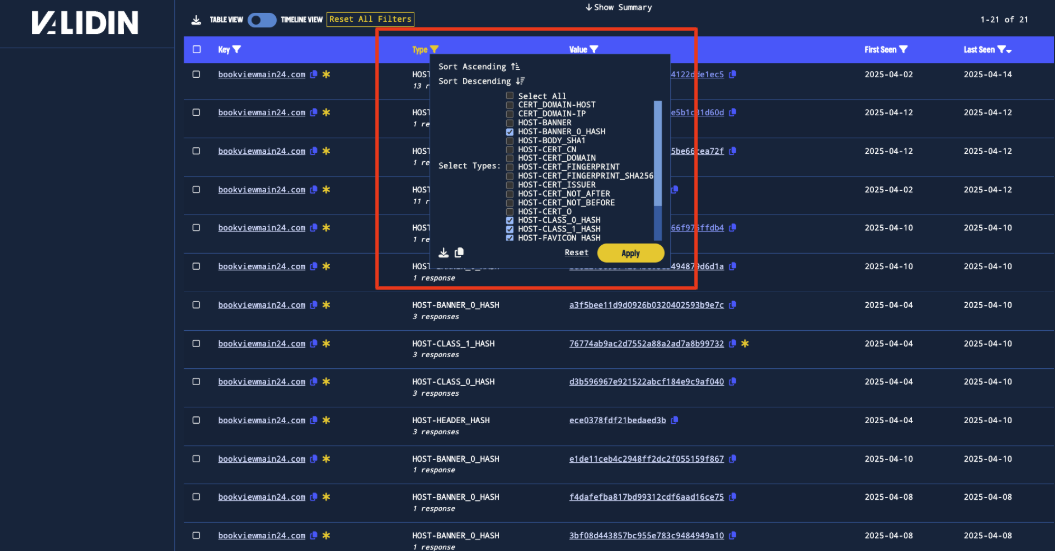
Figure 8. Using the type filters to select only connections to various hashes.
Pivoting through these hashes, I find that the CLASS_0_HASH and ``CLASS_1_HASH` are both interesting for two reasons: they are not highly popular according to Validin (indicated by a white “flame” icon in the value and a cardinality estimate) and they all connect to multiple domain names that we haven’t observed yet. When we pivot off these two hashes, I find 34 domains that all look very similar.
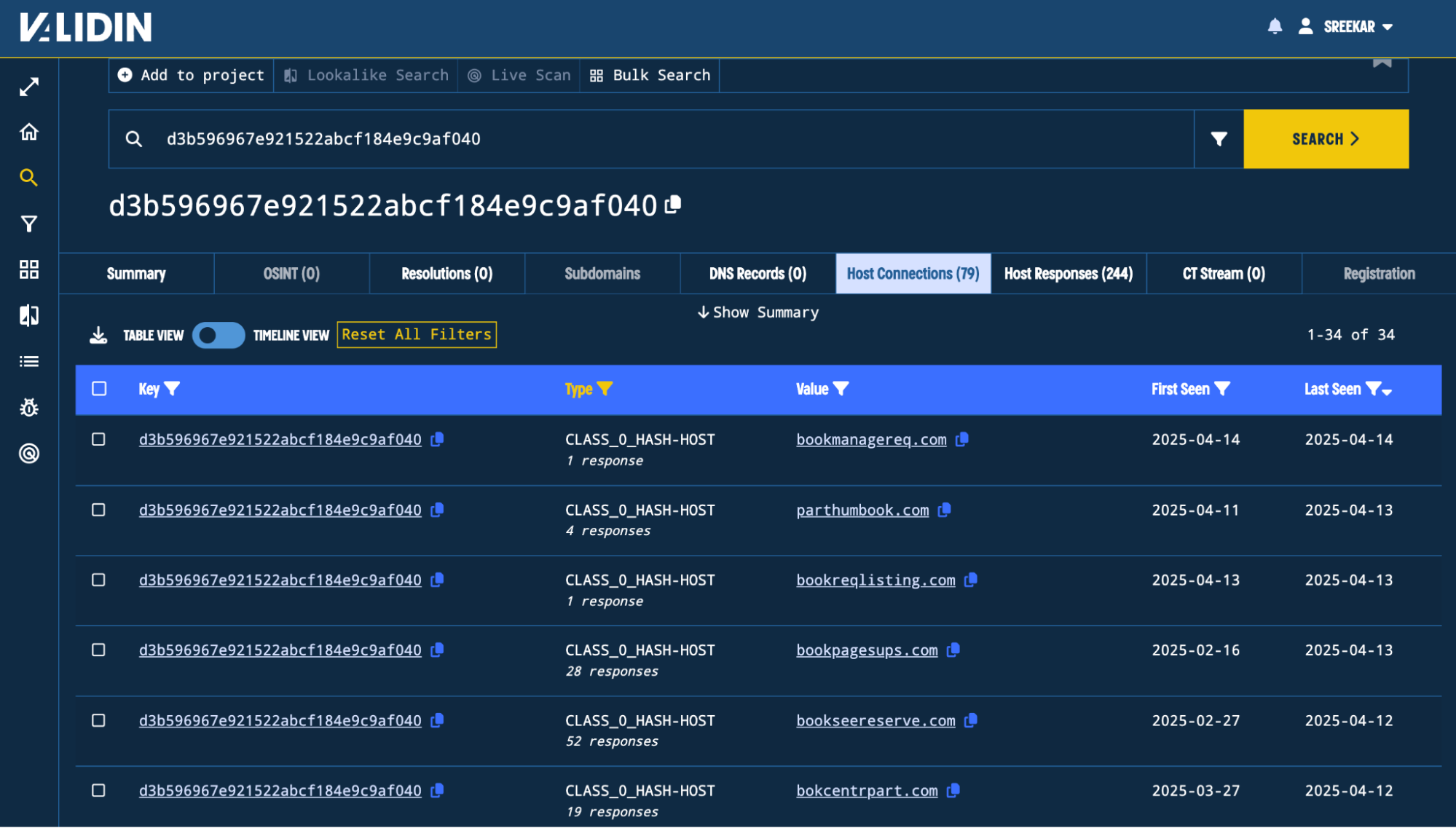
Figure 9. All the domains linking to the class hash d3b596967e921522abcf184e9c9af040
Clicking on the Host Response, I observe that all of these domains have responses with the title Booking.com.
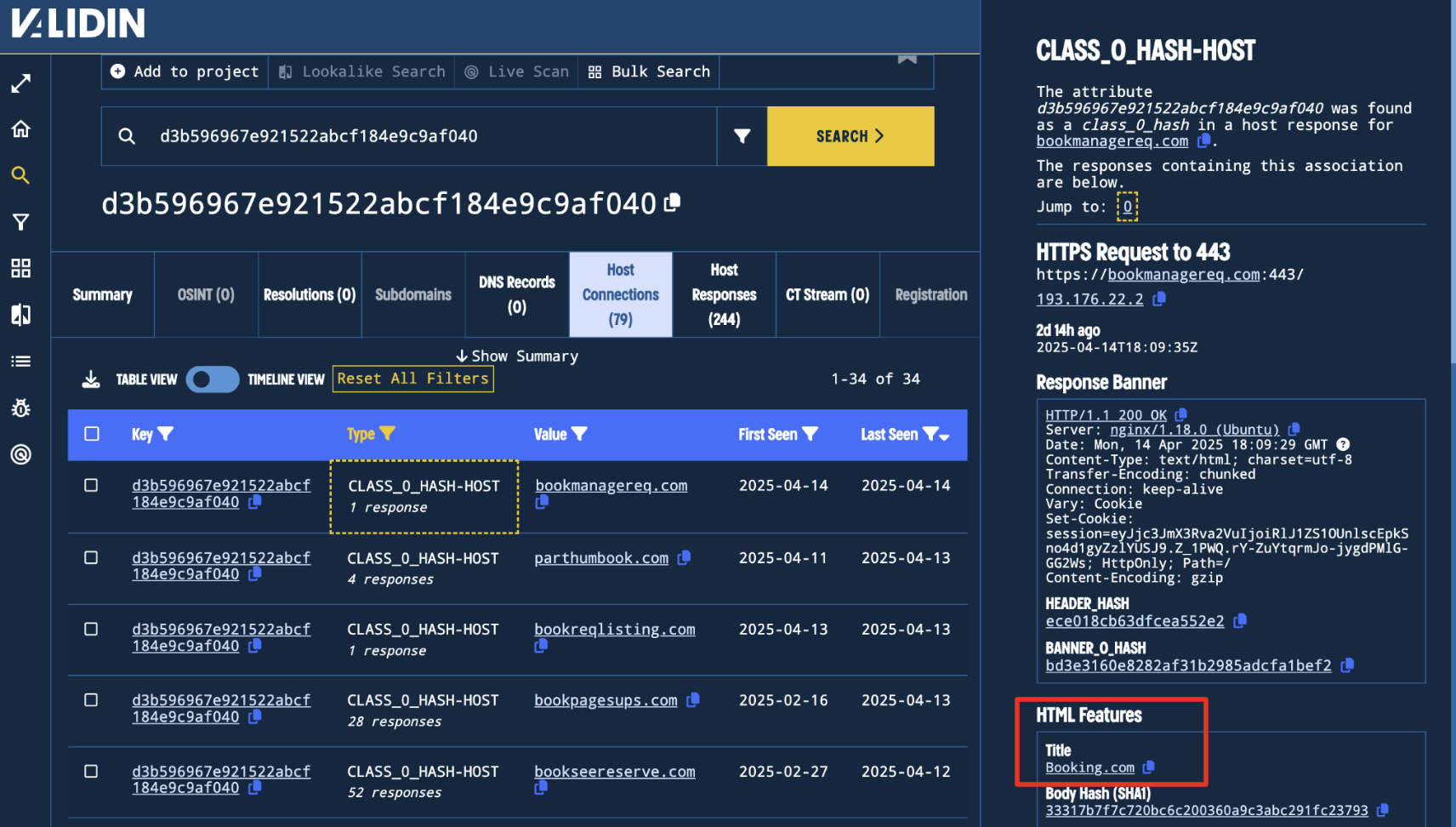
Figure 10. Host Response for bookmanagereq.com with the title Booking.com
Using Live Scanning to Validate Domains
We want to confirm that these domains are related to the ClickFix campaign that was originally reported.
We can use Validin’s live scanning feature (available to Enterprise users) to visit these domains and confirm that they’re part of the ClickFix campaign.
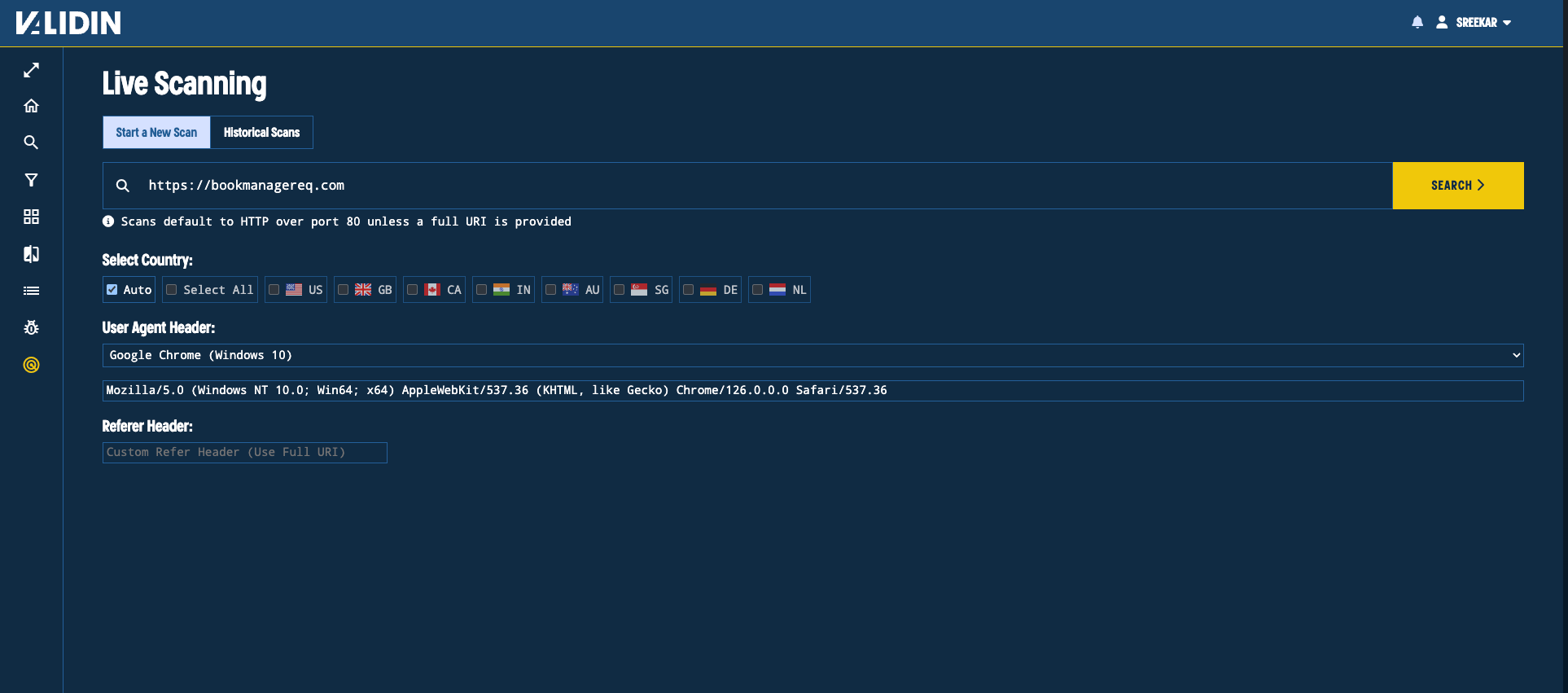
Figure 11. Starting a live scan for the domain bookmanagereq.com
Running a live scan on the most recently observed domain bookmanagereq[.]com results in a 200 OK response with the title “Booking.com”.
When we examine the page HTML, we see a handful of interesting features. We first see a comment in Russian at the top of the CSS that translates to “Global Styles”, along with CSS for a captcha.
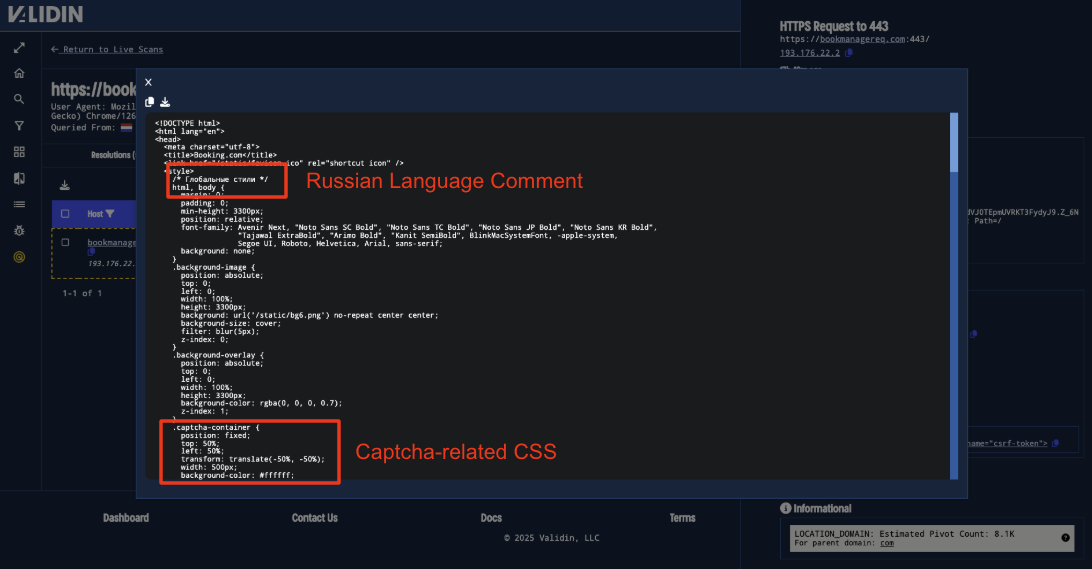
Figure 12. CSS for this domain with a Russian language comment and Captcha-themed CSS.
ClickFix is well known for its use of fake captchas. Pulling this thread, we observe a client-side fetch request for the relative path /get_captcha_text.
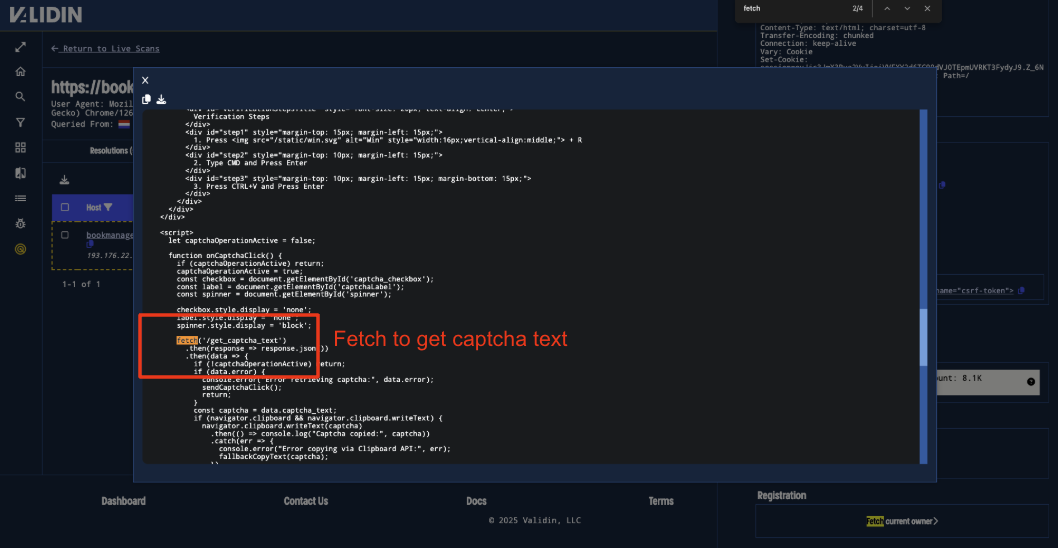
Figure 13. The domain HTML includes a fetch request to /get_captcha_text.
We also observe suspicious instructions in the HTML that all look very similar to ClickFix:
Verification Steps
1. Press [Windows] + R
2. Type CMD and Press Enter
3. Press CTRL+V and Press Enter
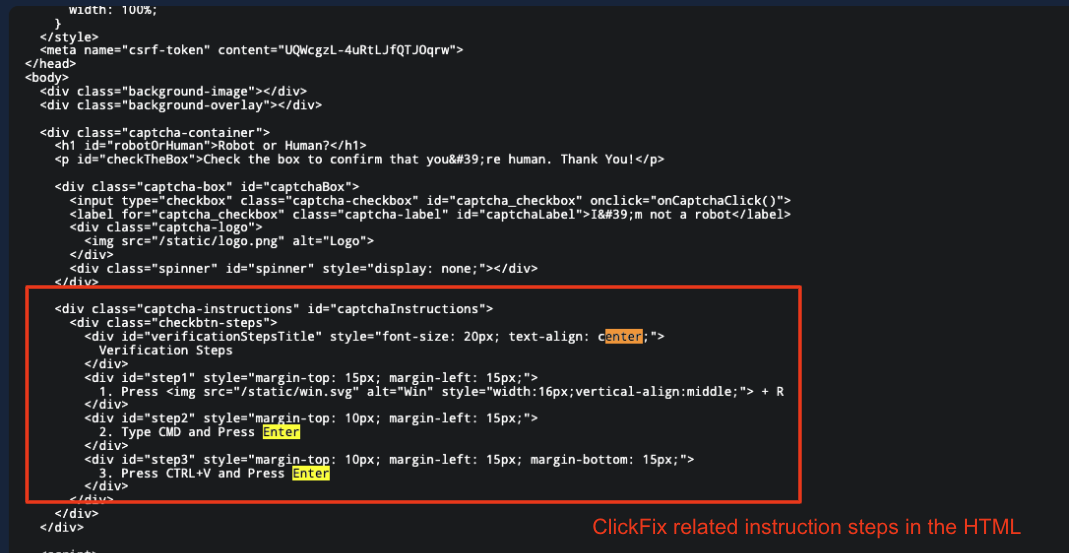
Figure 14. The HTML also includes ClickFix related instructions.
Requesting /get_captcha_text from the same host returns the HTML below, which includes the link to a redirector https://cpthevrf[.]click/F44GTGHOVB0snx.
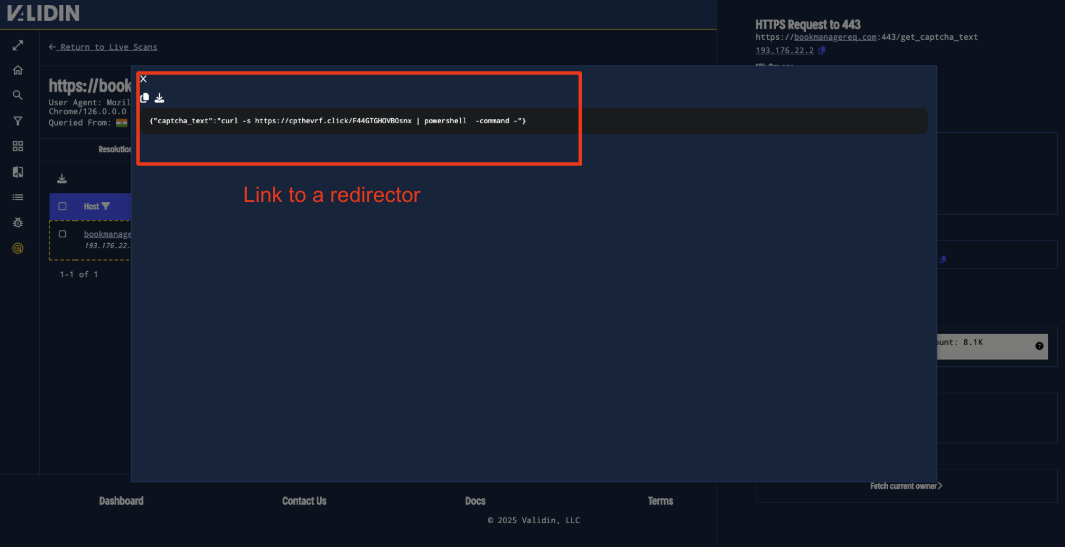
Figure 15. The fetch for captcha text pulls the above URL.
When we visit this link, we see a lot of javascript being loaded on the page that downloads various files from 92.255.85[.]207.
![Figure 16. Visiting this redirector downloads the following executables from the IP 92.255.85[.]207. Figure 16. Visiting this redirector downloads the following executables from the IP 92.255.85[.]207.](/images/booking_themed_clickfix/image19.png)
Figure 16. Visiting this redirector downloads the following executables from the IP 92.255.85[.]207.
This is pretty interesting on its own, but we can now take this executable identified in the javascript: http://92.255.85[.]207/ret.exe and run it in a sandbox, e.g., any.run.
Looking at the sandbox results: we can see that this executable downloads a second executable from the same IP address, and runs an AsyncRAT trojan on the device.
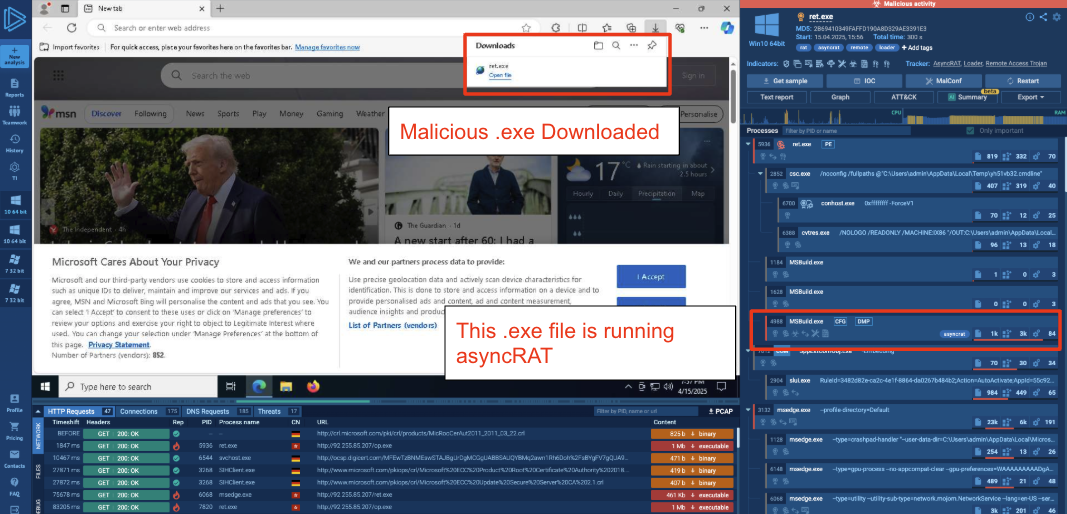
Figure 17. Running this executable in the sandbox shows that it downloads additional payloads from the IP and installs the trojan AsyncRAT.
These findings align with the original reported tweet. Link to the sandbox run here: https://app.any.run/tasks/d30588af-053f-4080-88b4-fc50407a8328.
Many of the domains in the original set are non-responsive or have already been taken down, so we can only examine the ones that are still live. However, with this validation, we can confidently convict all of these domains given the similarities in the content (CSS hashes, title tags, and approximate response sizes).
Using Lookalikes to discover additional infrastructure
We notice that both “redirector” domains start with cp and share the top-level domain .click
We can do a lookalikes search (a premium individual and enterprise feature) to discover other potential domains related to this one. This can be done through both the UI and the API.
We can initiate a regex search in lookalikes for domains that start with cp, and end with .click
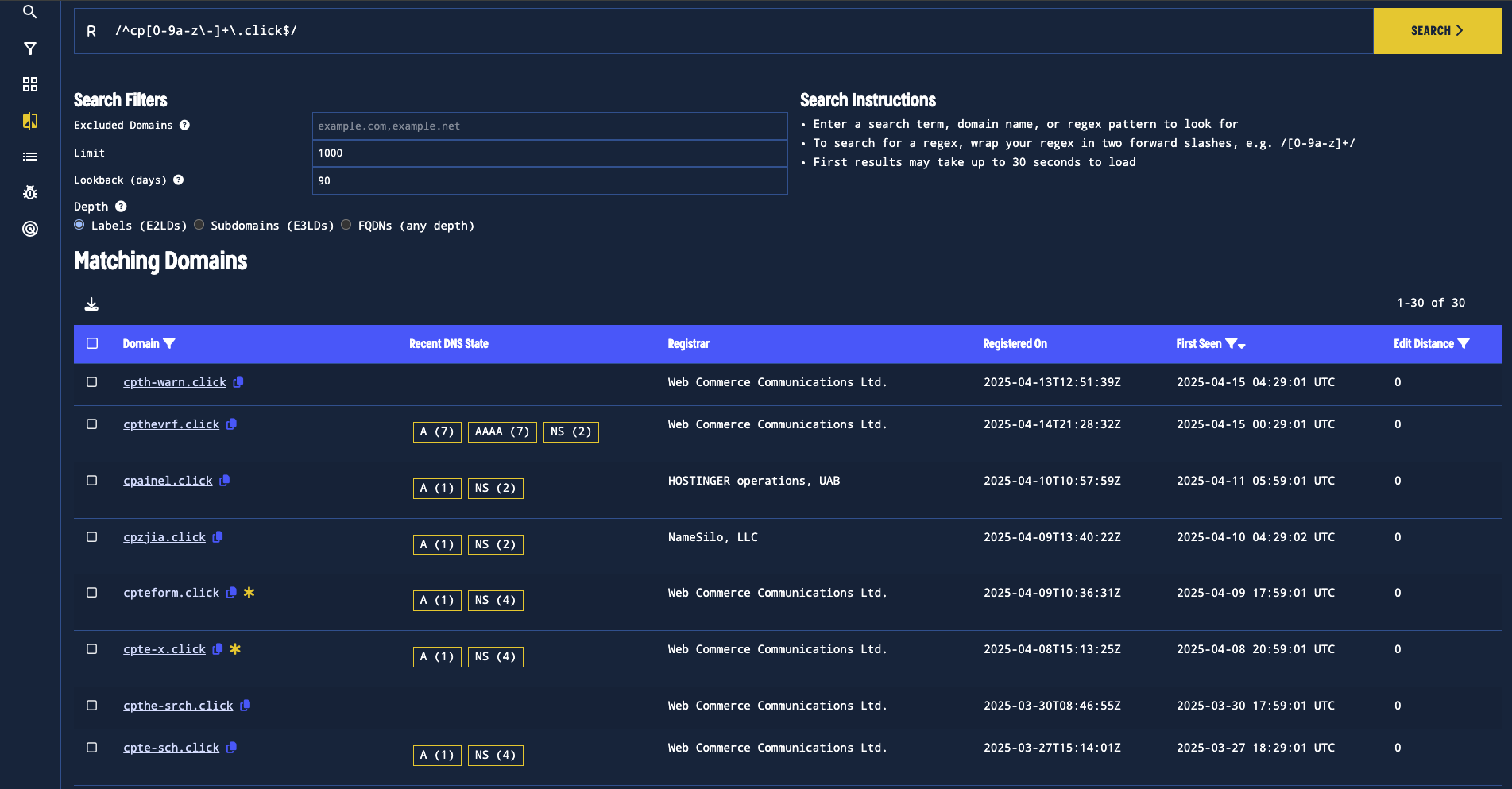
Figure 18. Running a lookalikes search for recently-observed domains finds many domains that are recently registered on Web Commerce Communications.
We find 30 domains, of which many of them can be linked to this suspicious domain through the use of the registrar “Web Commerce Communications”.
Let’s take a deeper dive at the domains in this set that are still currently resolving to see if we can uncover additional infrastructure.
Looking at cpte-x[.]click we see a few interesting things.
- Hosted on the same ASN as the two IPs where the malicious executables were downloaded from
![Figure 19. 92.255.85[.]89 is hosted on an IP in the same ASN as the other IPs where the malicious executables were downloaded from. Figure 19. 92.255.85[.]89 is hosted on an IP in the same ASN as the other IPs where the malicious executables were downloaded from.](/images/booking_themed_clickfix/image6.png)
Figure 19. 92.255.85[.]89 is hosted on an IP in the same ASN as the other IPs where the malicious executables were downloaded from.
When you pivot on that IP address, you also see a lot of domains that look very similar to this one.
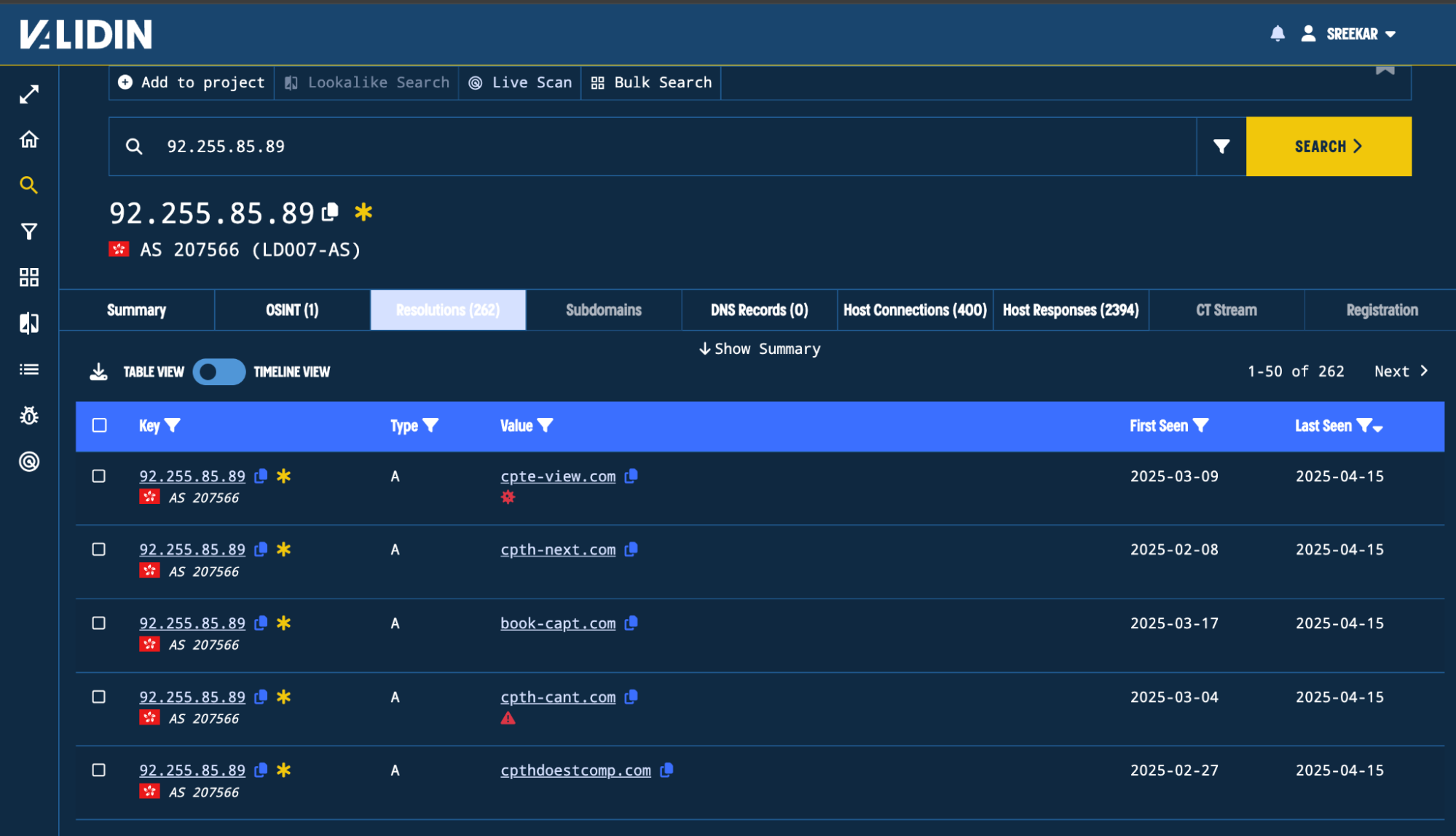
Figure 20. This IP address resolves to many domains that all look related to this campaign.
Pivoting Off Favicons to find related infrastructure
Going back to the domain cpte-x[.]click, we can pivot off of one of the interesting hashes to see if any of them provide additional domains of interest. We see that the favicon hash is shared among this set of domains that all look very related to this campaign.
![Figure 21. The Favicon Hash for the domain cpte-x[.]click connects to additional related domains that are part of this campaign. Figure 21. The Favicon Hash for the domain cpte-x[.]click connects to additional related domains that are part of this campaign.](/images/booking_themed_clickfix/image14.png)
Figure 21. The Favicon Hash for the domain cpte-x[.]click connects to additional related domains that are part of this campaign.
We can follow this same thread for the domain bookmanagereq[.]com, pivoting off the favicon hash, 6018807017afead14417566f975ffdb4, for this domain to find other related domains.
![Figure 22. The Favicon Hash for bookmanagereq[.]com connects to hundreds of suspicious domains and IP addresses, the very first one of which looks similar to our existing themes. Figure 22. The Favicon Hash for bookmanagereq[.]com connects to hundreds of suspicious domains and IP addresses, the very first one of which looks similar to our existing themes.](/images/booking_themed_clickfix/image4.png)
Figure 22. The Favicon Hash for bookmanagereq[.]com connects to hundreds of suspicious domains and IP addresses, the very first one of which looks similar to our existing themes.
Note: These domains are all highly suspicious, because they use a Booking.com favicon, but at this point it is unclear whether they are associated with the same kit, or are part of a different campaign. We leave this as open question.
Doing a live scan of this new domain bobkngsiggn[.]com results in almost identical HTML to the original domain we scanned, and following this pattern leads to the following domains and IP addresses.
https://rekaphcentre[.]site/2BN64A77wVxndU
http://193.176.22[.]172/args.bat
http://193.176.22[.]172/voice.exe
This new IP address is hosted on the same Russian ASN as the IP 193.176.22[.]2, which is where the domain bookmanagereq[.]com resolves to.
![Figure 24. HTML for the domain bobkngsiggn[.]com that shows the same Russian language comment for “Global Styles” and captcha-themed CSS. Figure 24. HTML for the domain bobkngsiggn[.]com that shows the same Russian language comment for “Global Styles” and captcha-themed CSS.](/images/booking_themed_clickfix/image2.png)
Figure 24. HTML for the domain bobkngsiggn[.]com that shows the same Russian language comment for “Global Styles” and captcha-themed CSS.
Conclusion
A single tweet highlighting a ClickFix infection path has uncovered a network of hundreds of indicators that are part of a malicious cluster of ClickFix domains. There are definitely opportunities for researchers to continue pulling these threads to uncover additional scope for this campaign. If you are interested in collaborating, please reach out to the Validin team!
Validin’s extensive, high-fidelity data on host responses and registration details provide extensive, proactive data about domain and IP activity at internet scale. This makes Validin a powerful platform and data source for any threat researcher or analyst tracking malicious domain names and IP addresses on the public internet. Ready to elevate your threat hunting, threat attribution, and incident response efforts? Whether you’re an individual analyst or part of a larger enterprise team, Validin offers solutions that meet your needs. Individual users can create a free account with their professional email and self-upgrade to access more advanced features and data.
Part of a team? Contact us today to explore our enterprise options and discover how Validin can provide your teams with powerful tools unparalleled data. Let Validin help you work smarter, faster, and more effectively in the fight against cyber threats.
Indicators
bookviewmain24[.]com
https://cpte-x[.]click/MYW9LV1SMR616d
92.255.85[.]66
92.255.85[.]207
https://92.255.85[.]207/ret.exe
https://92.255.85[.]207/module.bat
92.255.85[.]66
re-capte[.]cfd
recapte[.]click
re-cpte[.]click
www.re-capte[.]cfd
add-recpte[.]click
www.bookmanagereq[.]com
bookmanagereq[.]com
www.capte-req[.]click
capte-req[.]click
193.176.22[.]172
193.176.22[.]2
cpte-csv[.]click
cpth-warn[.]click
cptc-book[.]click
cpte-sch[.]click
cpthe-srch[.]click
cpthevrf[.]click
https://cpthevrf[.]click/F44GTGHOVB0snx
booker-auth[.]com
www.booker-auth[.]com
bobkngsiggn[.]com
captchviews[.]click
www.cpte-x[.]click
cpte-x[.]click
cpteform[.]click
www.cpteform[.]click
www.captchviews[.]click
cpte-view[.]com
cpth-next[.]com
book-capt[.]com
www.cpth-cant[.]com
cpth-cant[.]com
www.cpthdoestcomp[.]com
cpthdoestcomp[.]com
cpt-en[.]com
cpte-expl[.]com
cpth-book[.]com
next-cpth[.]com
www.bookreqlisting[.]com
bookreqlisting[.]com
cpt-exmple[.]com
www.cpte-sch[.]click
www.re-cpte[.]click
www.cpte-expl[.]com
www.cpte-view[.]com
www.recapte[.]click
www.cpthe-srch[.]click
bookcpche[.]com
92.255.85[.]89
bookviewmanage[.]click
bookinghhs[.]com
bookpart[.]click
bookingconfirmatorr[.]com
rekaphcentre[.]site
https://rekaphcentre[.]site/2BN64A77wVxndU
http://193.176.22[.]172/args.bat
http://193.176.22[.]172/voice.exe
7d326ee03b94c0c1854b5a669aa046b1
6018807017afead14417566f975ffdb4
8c4ddd3659782109a5bd7fb8bc9dc674
