Finding hundreds of phishing domains and IPs starting with a single IP address
In this post, we’ll use Validin’s comprehensive DNS and endpoint responses to uncover a threat actor that uses Calendly phishing domains to steal user credentials.
How it Started
This investigation started with a Twitter (X) post from AlphaSOC on April 8th about a threat actor impersonating Calendly to gain access to users’ cloud accounts by serving malicious OAuth applications.
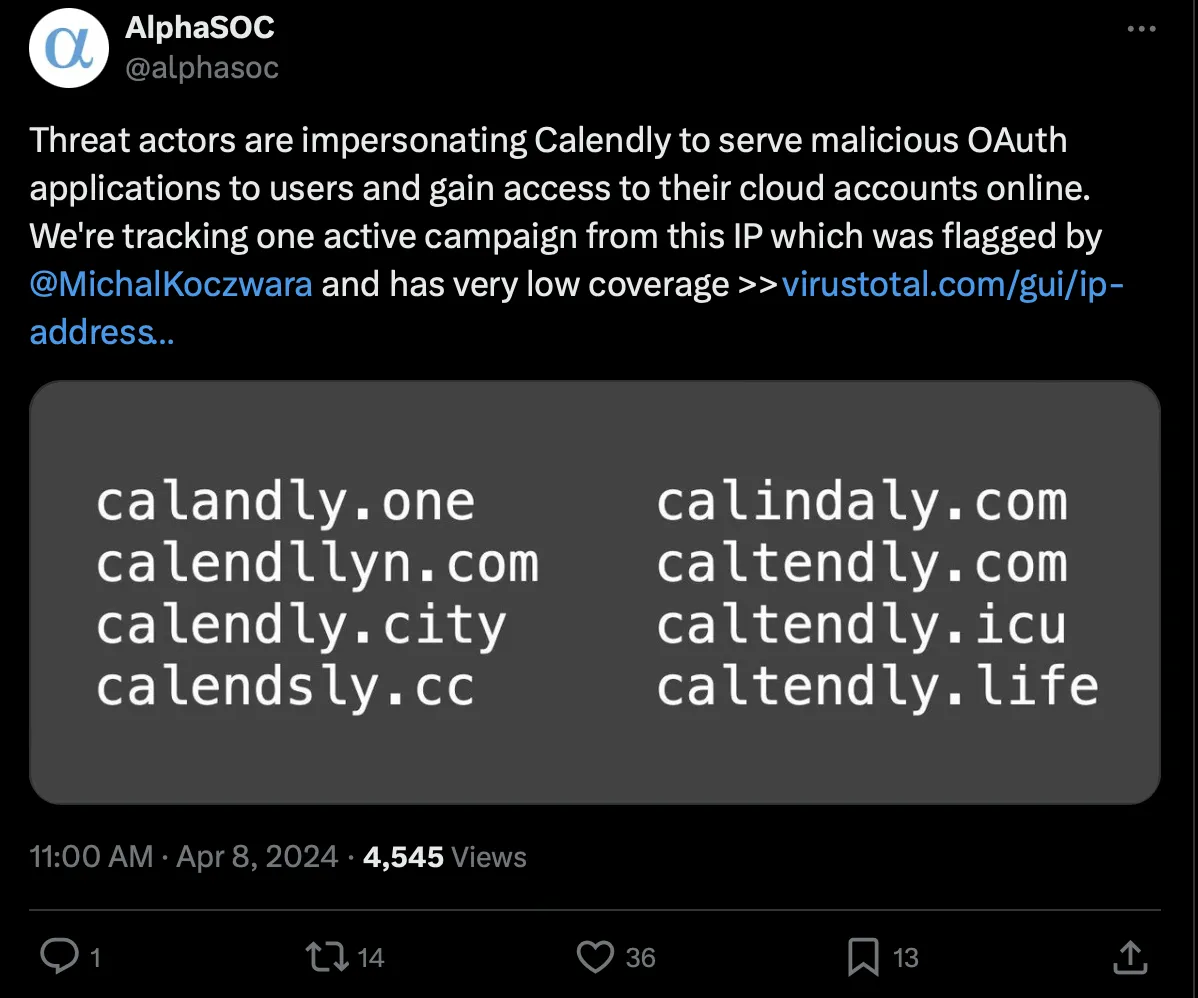
Original Tweet describing Calendly Phishing Campaign
Visiting one of these domains on urlscan.io shows something that looks like Calendly’s homepage, an evident attempt to trick users into giving up their credentials.
![Urlscan capture for calandly[.]one, an implicated domain in the original tweet Urlscan capture for calandly[.]one, an implicated domain in the original tweet](/images/finding-calendly-domains/image14.webp)
Urlscan capture for calandly[.]one, an implicated domain in the original tweet
The tweet shows a few examples of phishing domains and implicates this IP: 154.82.93[.]96. Going to the VirusTotal link shows 26 resolutions, of which 18 are Calendly lookalikes that were all resolved on 3/23 or later.
![Virus Total link for the IP 154.82.93[.]96 shows some resolving domains and their malicious indication by VT vendors Virus Total link for the IP 154.82.93[.]96 shows some resolving domains and their malicious indication by VT vendors](/images/finding-calendly-domains/image13.webp)
Virus Total link for the IP 154.82.93[.]96 shows some resolving domains and their malicious indication by VT vendors
Building our knowledge graph
We start our investigation by searching the IP address 154.82.93[.]96 on Validin. We found 40 additional resolutions for that IP address that were not on Virus Total. We use the table filters to select results observed after 3/24 since we see with both Validin and Virus Total’s data that the Calendly lookalikes started after that date for this domain.
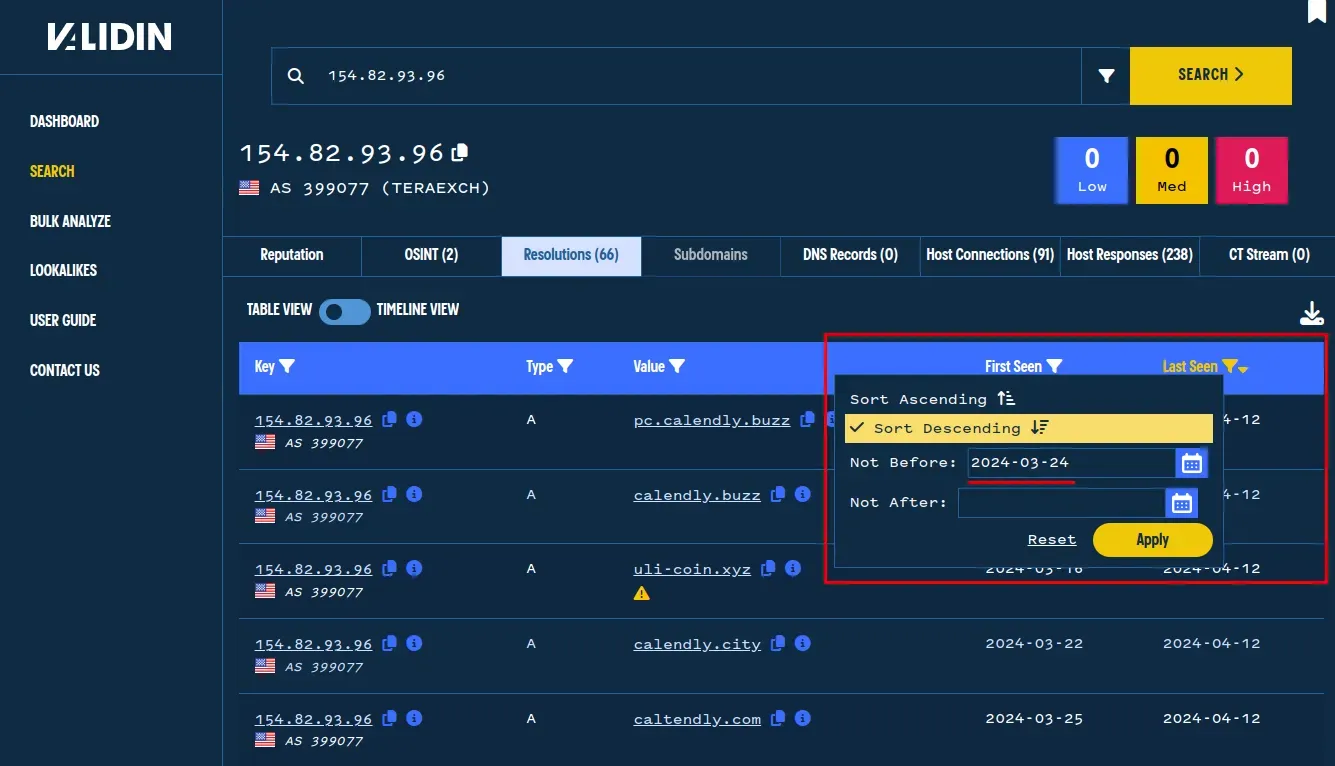
Validin search for the DNS resolution history of this malicious IP.
We found that with this results filer, Validin has 27 domains, all of which are Calendly lookalikes and hosted on the same IP in the same general timeframe, indicating they are related.
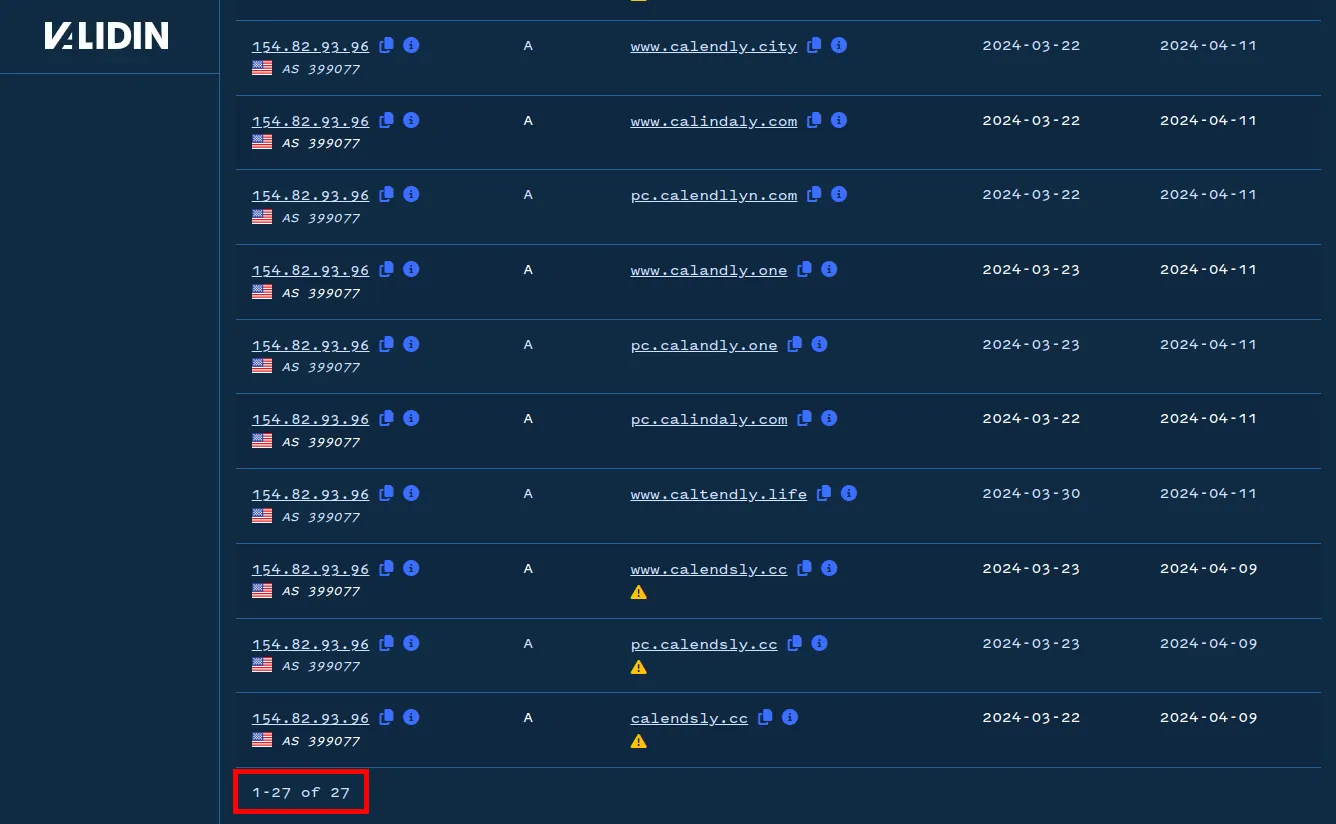
27 Calendly lookalike domains were found on this single IP address.
Pivoting off one of these domains and examining the host connections shows it is a typosquatting domain mimicking Calendly. We can see that it has the same page title as calendly.com. This leads to an exciting pivot: using the page title to see what else is trying to mimic Calendly.
![Host associations for calindaly[.]com shows evidence that the domain is impersonating Calendly by using the same title tag. Host associations for calindaly[.]com shows evidence that the domain is impersonating Calendly by using the same title tag.](/images/finding-calendly-domains/image6.webp)
Host associations for calindaly[.]com shows evidence that the domain is impersonating Calendly by using the same title tag.
We see 84 total hosts or IPs with identical page titles. We filter by the TITLE-HOST association to view only the domains that share this title.
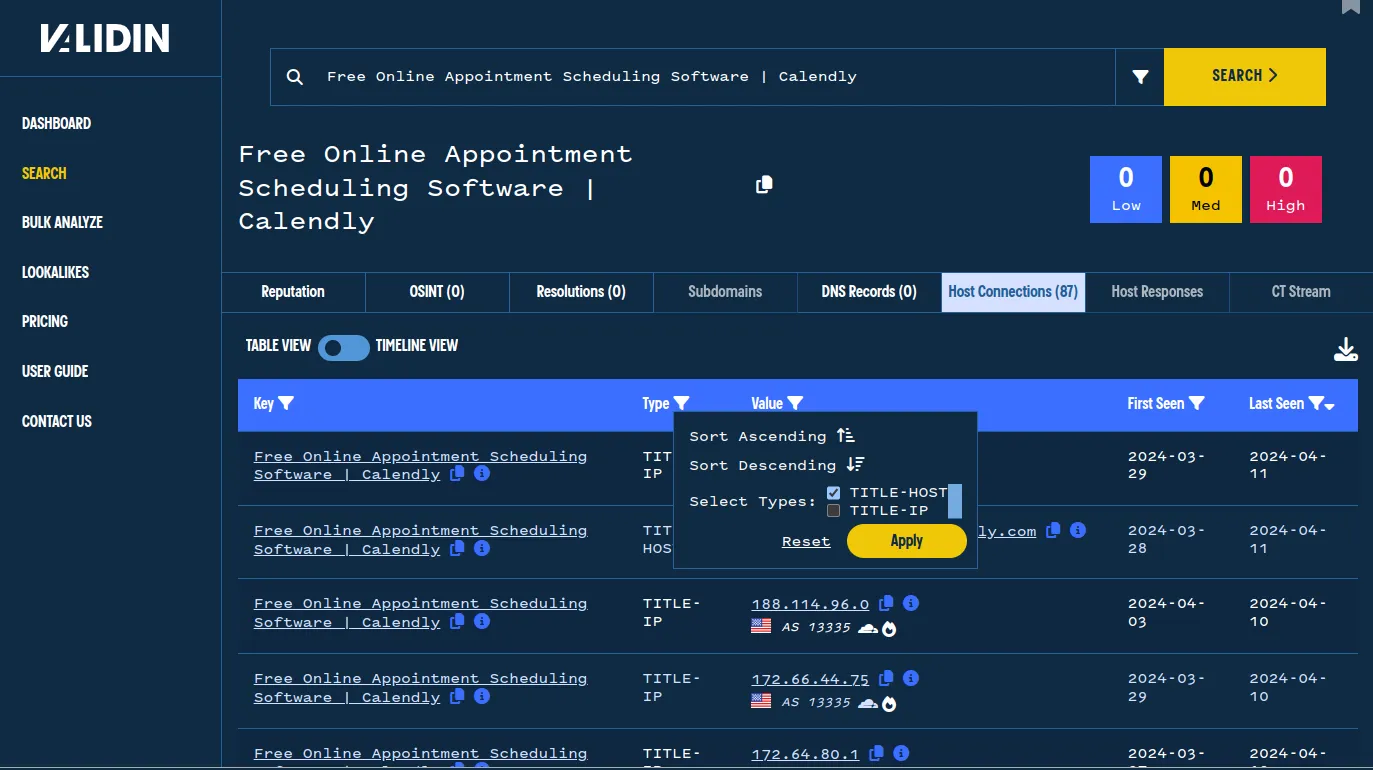
We use the table filters to find only the relevant information from this search.
Using this filter, we can see 44 results after excluding legitimate calendly.com domains, which likely Calendly phishing domains.
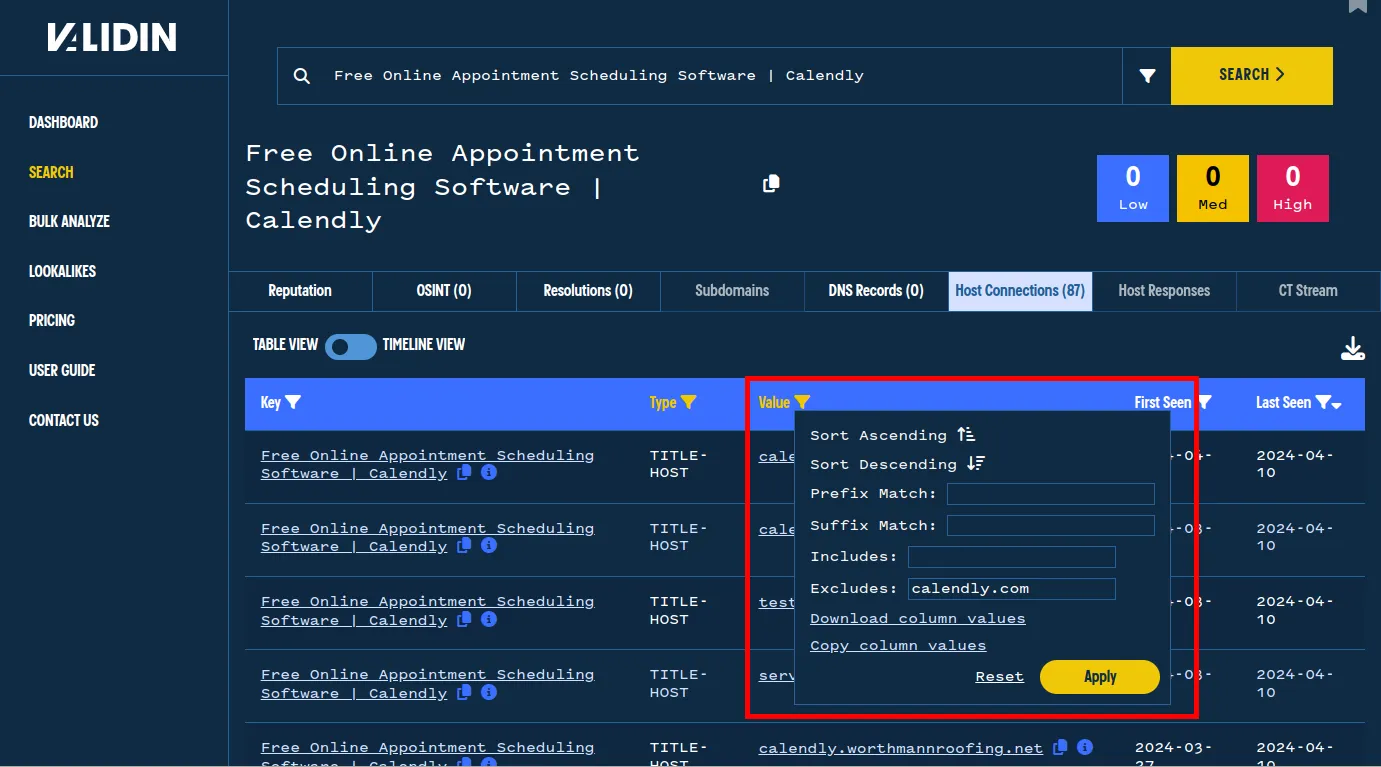
Using the value filter to exclude legitimate domains.
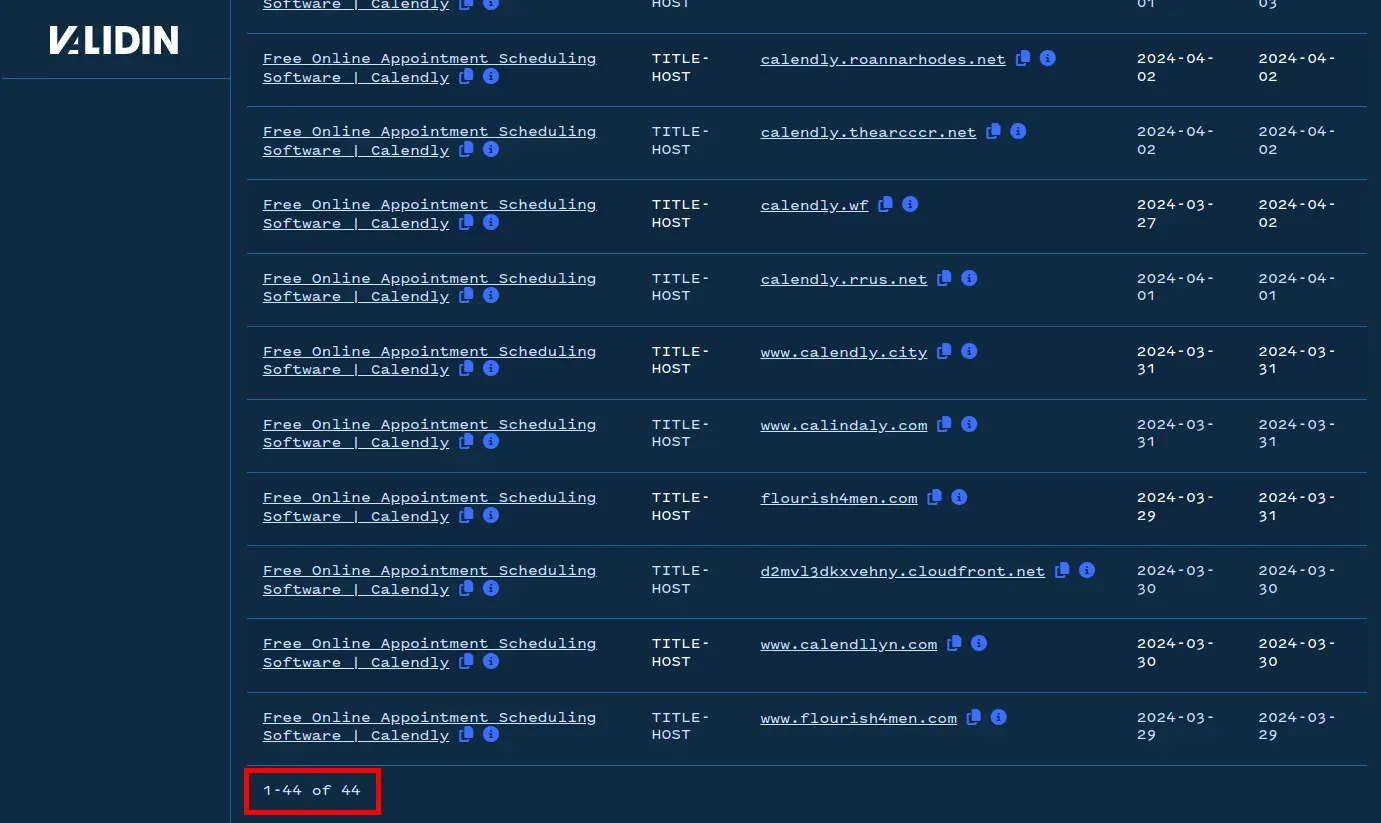
After filtering, 44 domains are suspected Calendly lookalikes.
Now, changing to TITLE-IP associations, we see 39 results, of which the vast majority are highly popular AWS or Cloudflare ASN. We can visually ignore these IP addresses, many of which include a white flame icon because they host many domains (the white flame icon indicates this). Highly popular IP addresses can be less valuable direct pivots because they host thousands of resolving domains. The Russian IP address 78.24.180[.]93 looks interesting because it is not highly popular and is in the Russian AS “SELECTEL,” so let’s pivot off of that.
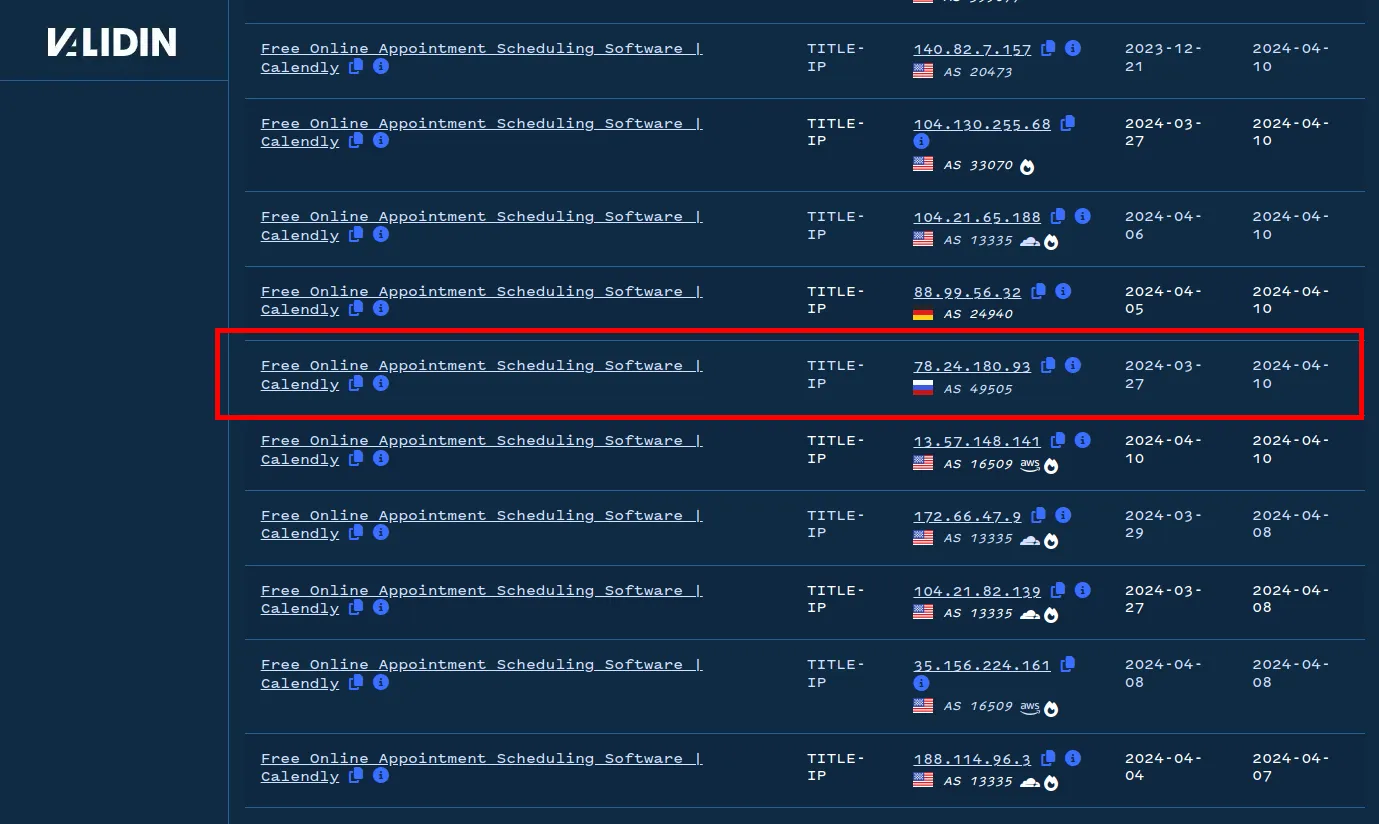
One IP that looks out of place returns the same title as the Calendly homepage.
Pivoting, we see 406 resolutions for this IP address, all of which are lookalikes and potential phishing domains, including lookalikes for Discord, Notion, Autodesk, and Blender.
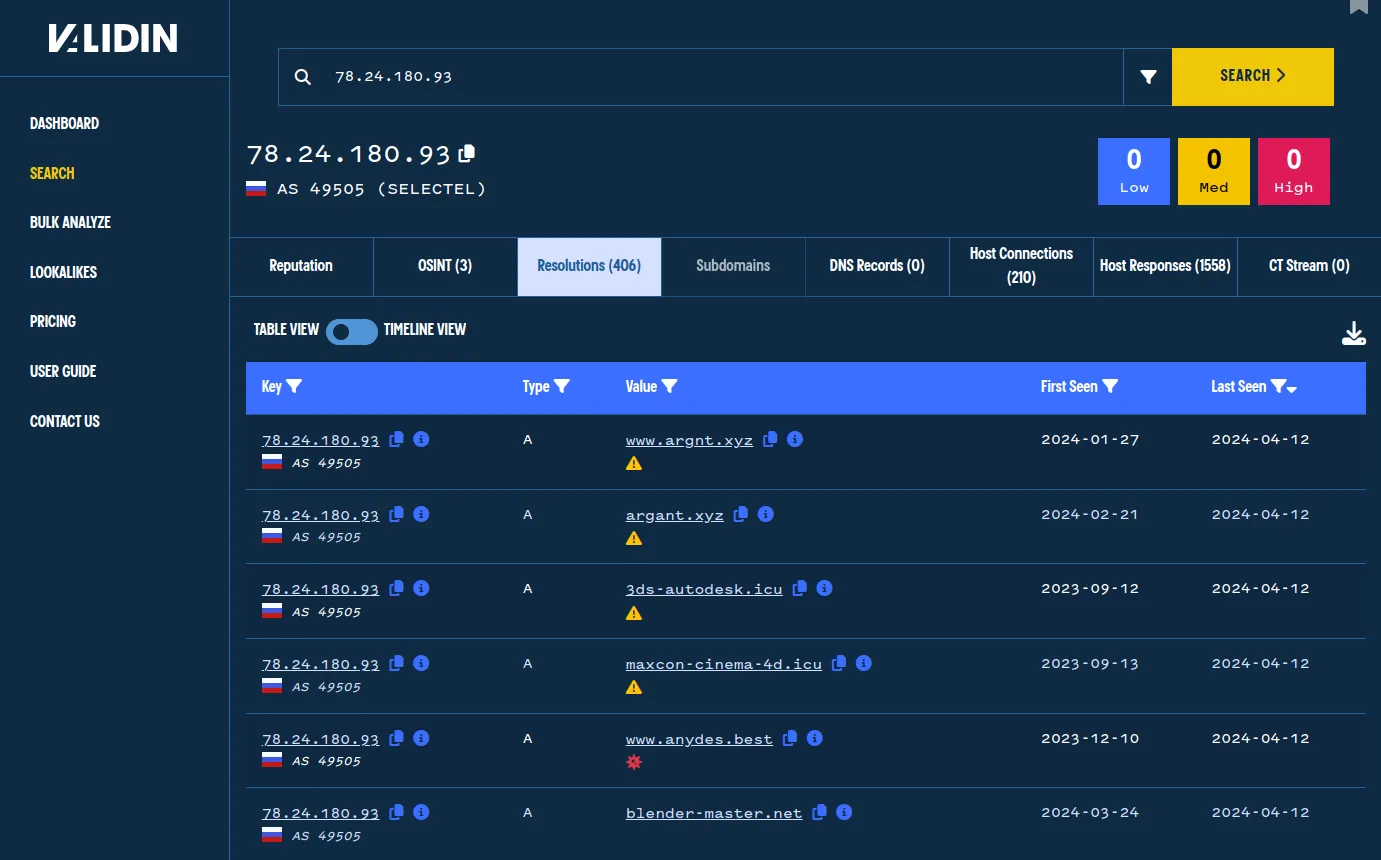
Resolutions for this suspected malicious IP address include many lookalikes, including some impersonating Calendly.
Going to the host connections and filtering by IP-TITLE leaves just 7 results, 4 of which look interesting as titles potentially indicative of phishing attempts.
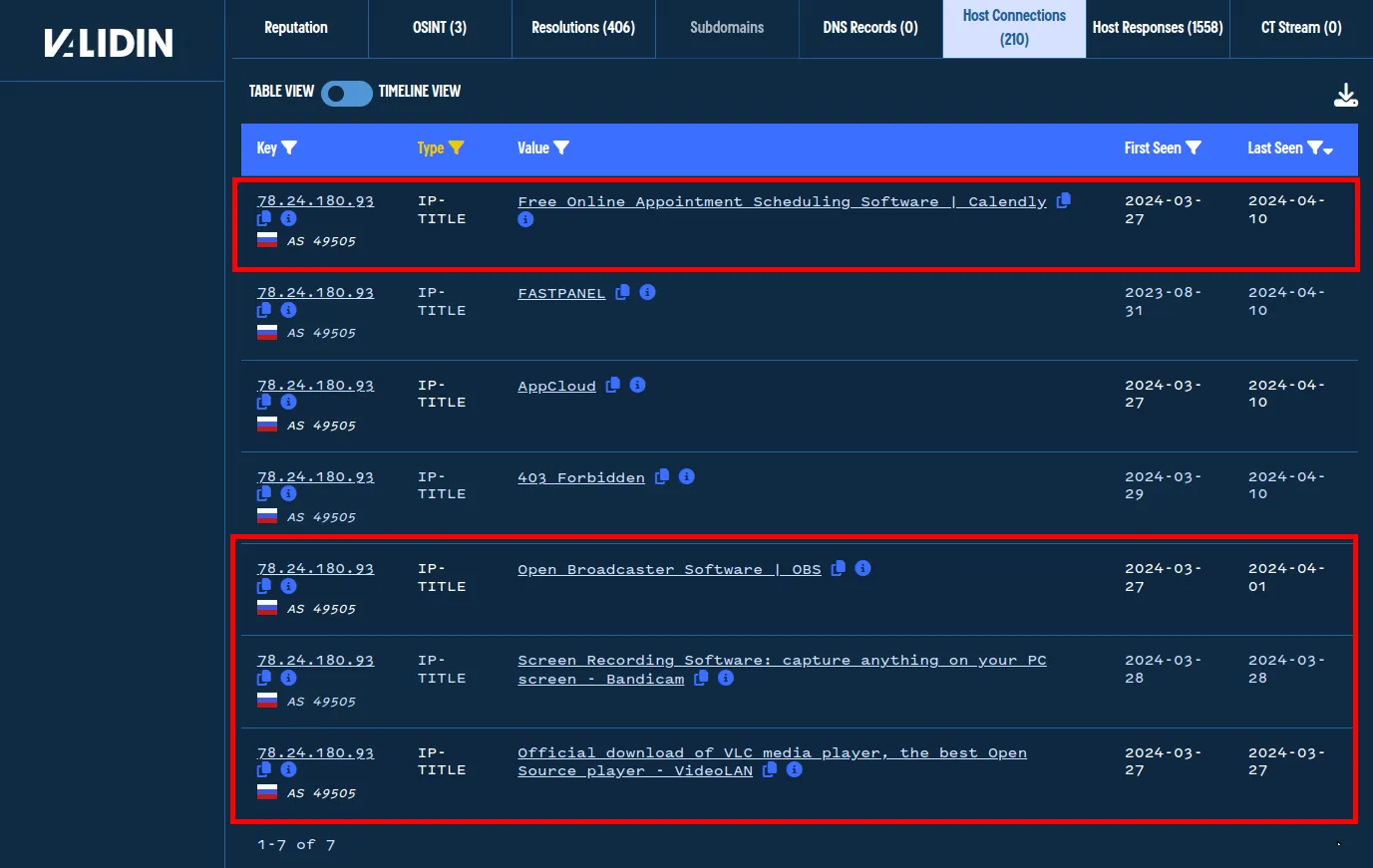
Interesting HTML titles returned from domains using this IP could be phishing attempts.
Using this methodology, by pivoting over specific elements in the HTML body, we quickly find lots of related infrastructure. In this case, we’ve also unearthed an IP that has hundreds of potential phishing domains, not just for Calendly, but for many other brands and websites.
Using Validin’s Data Effectively
Another interesting note about Validin’s data: the frequency with which we collect our data helps us track changes with high precision. I chose one random Calendly phishing domain to examine: airplanereference[.]com, and analyzed it. A quick check of Validin’s data and Urlscan.io confirms that this website imitates Calendly.
![Urlscan capture for airplanereference[.]com demonstrates how it imitates Calendly to steal user credentials. Urlscan capture for airplanereference[.]com demonstrates how it imitates Calendly to steal user credentials.](/images/finding-calendly-domains/image15.webp)
Urlscan capture for airplanereference[.]com demonstrates how it imitates Calendly to steal user credentials.
At Validin, we crawl hundreds of millions of domains we see every 2 days, allowing us to track infrastructure changes incredibly quickly. In the case of this domain, we observed that the page title was “Site is created successfully!” until sometime between April 4th and April 6th, when its content was changed to mimic Calendly. High-frequency web crawling and DNS resolution allow us to quickly track these changes and help us pinpoint changes to threat actors’ infrastructure.
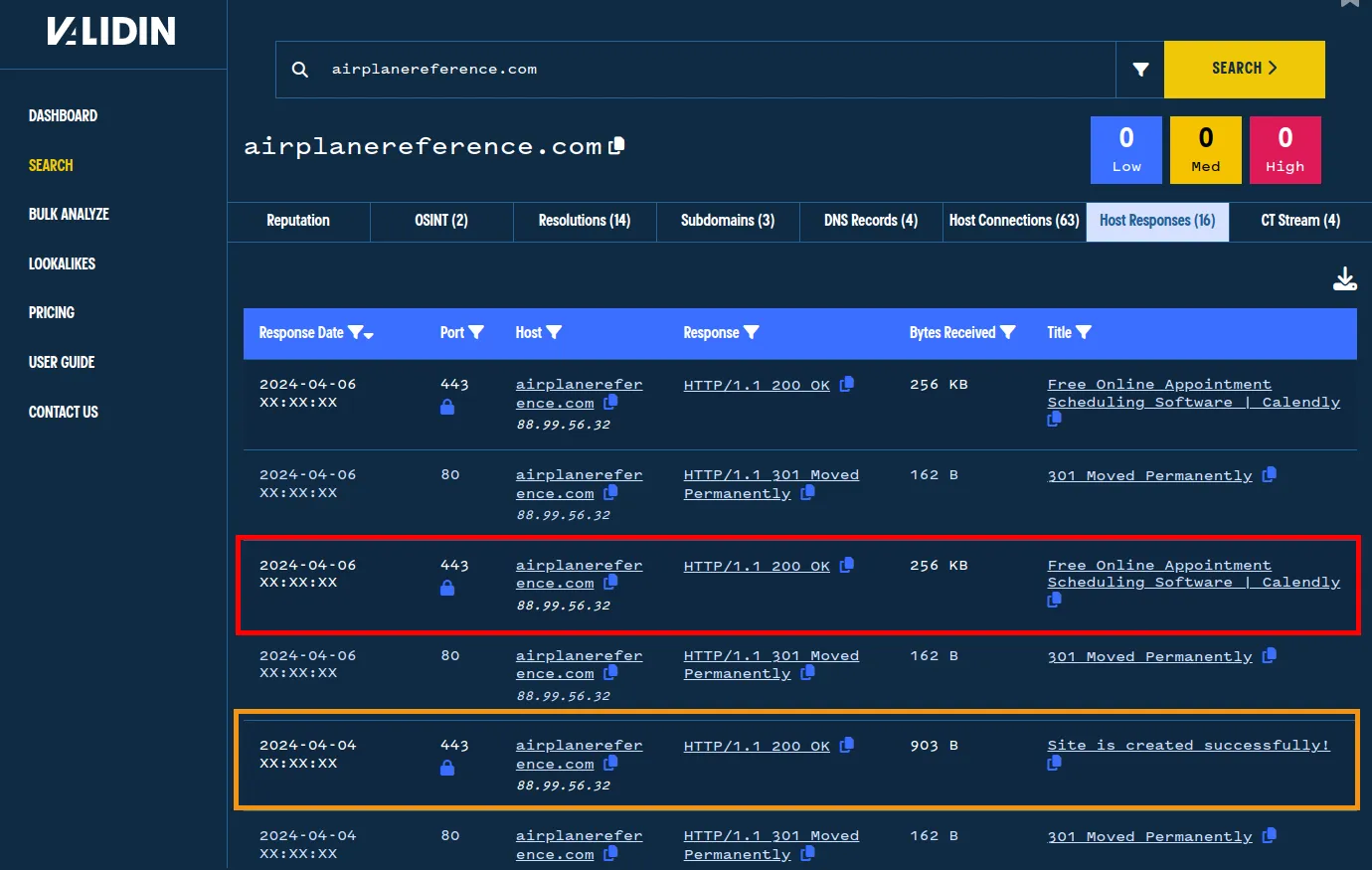
Validin saw that this website came online as a phishing domain between April 4th and April 6th.
Conclusion
Validin’s incredibly robust data is refreshed frequently, allowing users to track changes quickly and stay on top of threats.
Interested in leveraging Validin to build threat intelligence proactively? Check out our individual pricing and plans, or contact us to learn about our enterprise options.
154.82.93[.]96
78.24.180[.]93
calendsly[.]cc
www.calendsly[.]cc
meet.elemento[.]cloud
caltendly[.]life
www.caltendly[.]life
calandly[.]one
www.calandly[.]one
calendly[.]date
calendly[.]wf
www.calendly[.]wf
textbelt[.]click
airplanereference[.]com
ginger-software[.]com
www.ginger-software[.]com
calendly-meeting[.]com
flourish4men[.]com
www.flourish4men[.]com
calendllyn[.]com
www.calendllyn[.]com
historynatureinfo[.]com
cabalpartners[.]com
calindaly[.]com
www.calindaly[.]com
hh.ceshiym[.]shop
calendly-masai-group-3.netlify[.]app
calendly[.]events
www.calendly[.]events
calendly.worthmannroofing[.]net
calendly.thearcccr[.]net
calendly.roannarhodes[.]net
calendly.rrus[.]net
d35pdk54ela7r.cloudfront[.]net
d2mvl3dkxvehny.cloudfront[.]net
caltendly[.]icu
www.caltendly[.]icu
serverside-twitter.pages[.]dev
testingtwitter.pages[.]dev
ahcts-booking-injector.cybersec-defense.workers[.]dev
calendly[.]today
calendly[.]city
www.calendly[.]city
calendly.deltagaragedoor[.]biz
