Fake DMCA Takedown Notice Scam Hunting
On November 5, 2025, at least two high profile YouTube content creators reported receiving fake DMCA takedown notices with links to malicious downloads, including Scott Manley and John Hammond. By publicly reporting their experiences on X, several other accounts (vxunderground, wbmmfq, and John Hammond via YouTube) quickly dissected this scam, analyzing the malware, the AI-generated lure pages, and identifying a number of related malicious domain names.
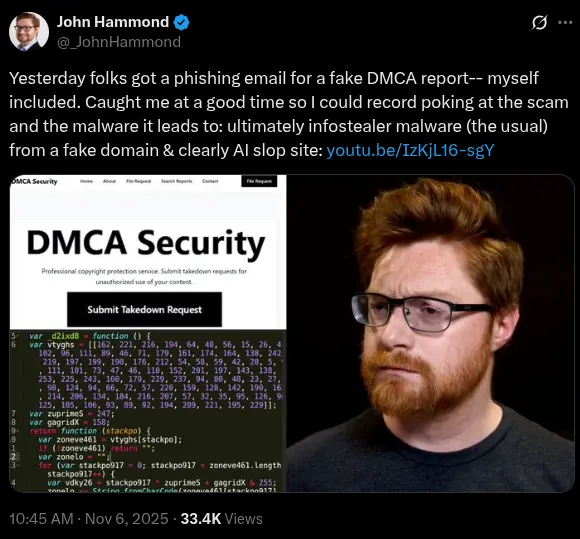
Figure 0. Post on X describing fake DMCA phishing email.
What is a DMCA takedown notice, and why is this scam effective? The Digital Millennium Copyright Act (DMCA) is a United States copyright law that criminalizes production and dissemination of technology, devices, or services intended to circumvent measures that control access to copyrighted works. The DMCA heightens penalties for copyright infringement on the Internet. Content creators on social media like YouTube may receive a “copyright removal request” citing the DMCA, which can affect their monetization or result in a ban on the platform. DMCA takedown scams involve threat actors creating pressure for content creators to remove content by surrendering money, sensitive information like logins, or in this case, downloading malware like credential stealers.
In this post, we’ll take a deeper look at the public infrastructure tied directly to this campaign, then show how to use Validin to discover other likely-related domain names and IP addresses based on DNS, host response, and other features.
Initial Indicators
The domain originally flagged as malicious by both Scott Manley and John Hammond was dmca-security[.]com. Through analysis by Tanner (@wbmmfq) and John Hammond (@_JohnHammond), we’re able to gather the following domains, IPs, and URLs connected to this threat:
From @wbmmfq‘s pivoting on Validin and Shodan:
101.99.92[.]246
takedownsecurity[.]com
takedownglobal[.]media
dmca-shield[.]com
dmca-security[.]com
dmca-hub[.]com
dmca-guardian[.]com
dmca-guard[.]com
dmca-abuse[.]com
youtube-dmca[.]com:3009
101.99.89[.]94:5000
From John Hammond’s analysis on any.run:
http[:]//185.153.198[.]115/
https[:]//45.80.231[.]244/gateway/fc2lje6m.mprui
national-competition-arise00[.]org:443
https[:]//ms-team-ping4[.]com/adlauncher.content
ms-team-ping7[.]com
ms-team-ping8[.]com
ms-team-ping9[.]com
ms-team-ping10[.]com
Note that the domain names ms-team-ping*[.]com were reported as far back as July 4, 2025 and further enriched through Validin host response pivots. X user @smica83 noted similar download patterns in these two domains: ms-team-ping2[.]com and azure-expresscontainer1[.]com.
Initial Analysis
I’ll begin by adding the 15 domain names and 4 IP addresses to a project in Validin so that I can quickly identify which ones I’ve seen and which are new as I pivot through indicators. I’ll also add tags and notes to each indicator to track how I found them and why they were added.
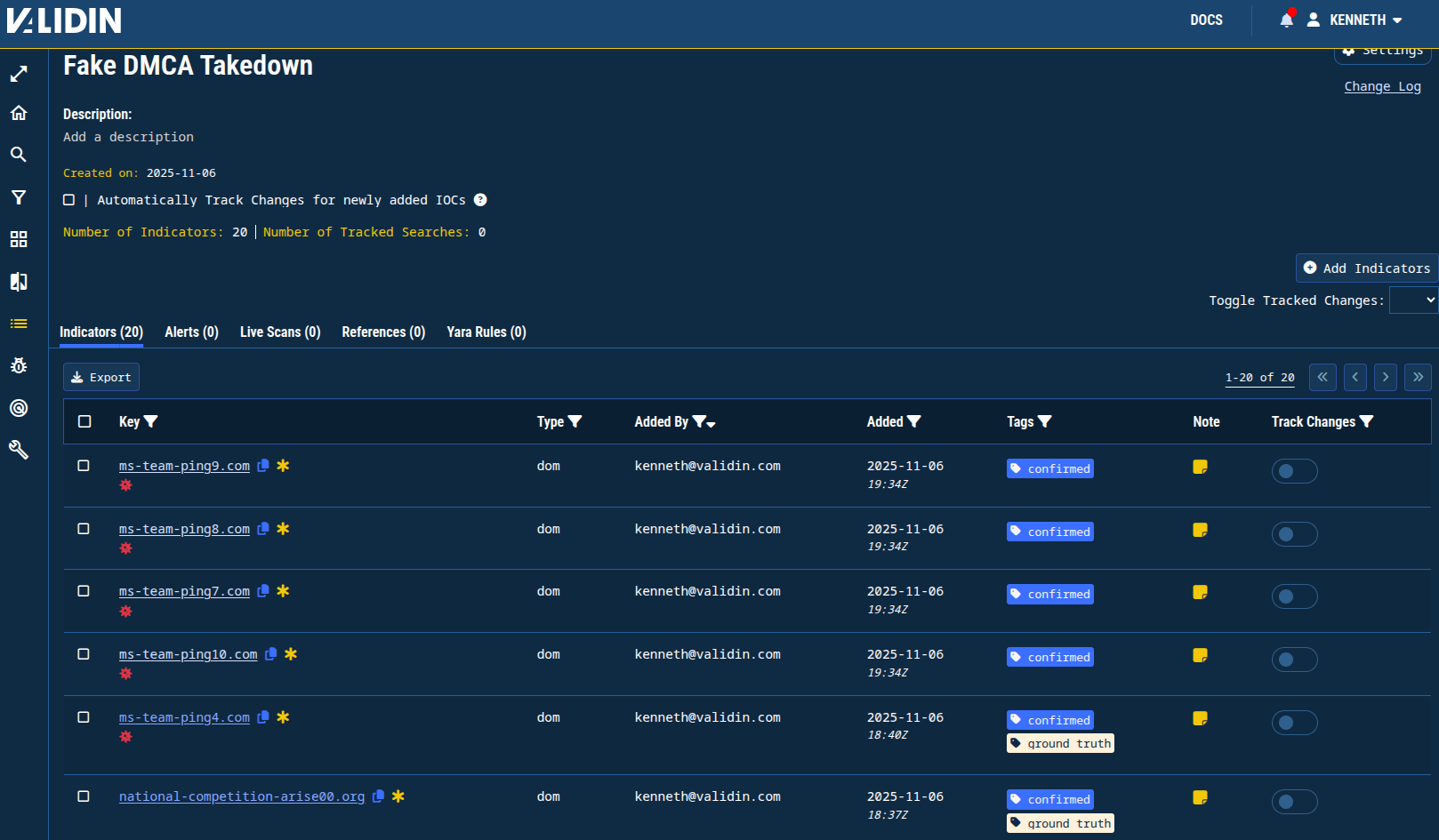
Figure 1. Indicators added to a project, tagged and with notes.
Of all the indicators publicly reported since November 5, 2025, only ms-team-ping*[.]com domains were already flagged in Maltrail as part of a cluster of over 150 other “fake software download” domains. Those domains include variations like ms-team-connect*[.]com, my-team-space*[.]com, and ms-onedrive-updater*[.]com. This pattern could be useful for lexicographic-based hunting rules like regex and lookalike domain searching.
Phishing Domain Pivots
Tanner (@wbmmfq) investigated the initial phishing domain, dmca-security[.]com, to uncover additional indicators, so I’ll briefly touch on that and then look for additional pivots.
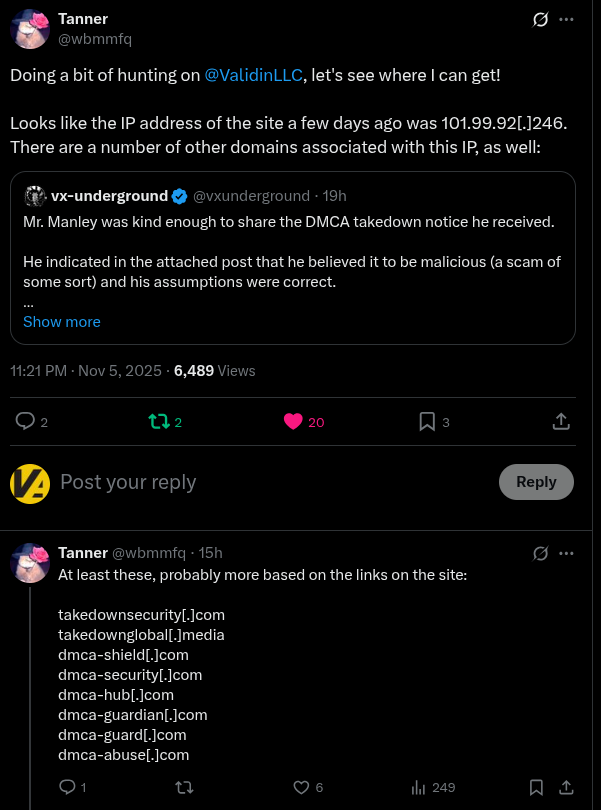
Figure 2. Public reporting of other related domain names.
In Validin, I see that the domain was registered on NICENIC just a few days ago and is hosted behind Cloudflare proxies.
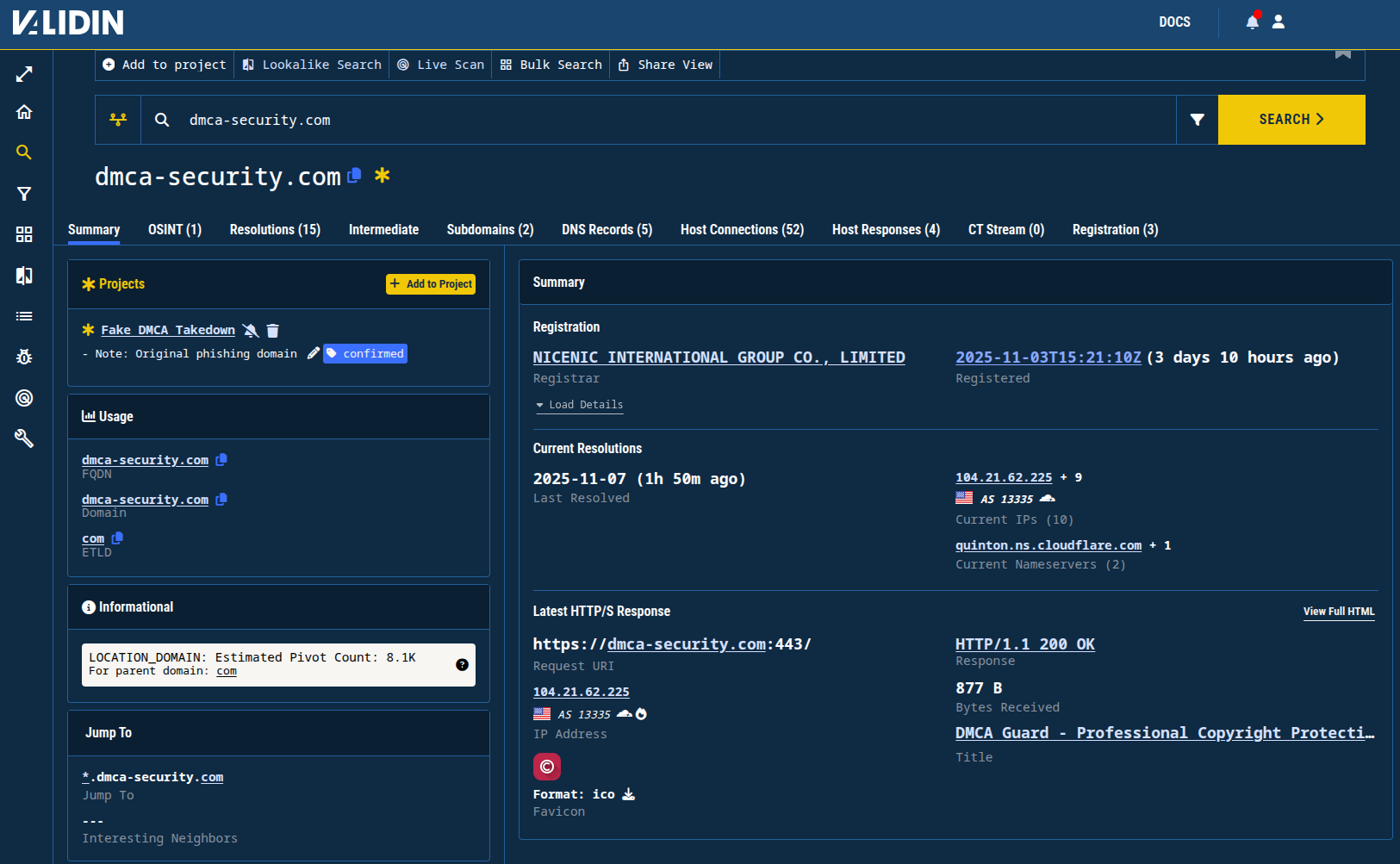
Figure 3. Validin’s summary of the initial phishing domain.
DNS Pivots
Following the approach used by @wbmmfq, I’ll look for pivots in DNS history. On the timeline view of the DNS resolutions, we see that the IP used for pivoting, 101.99.92[.]246, was used very briefly right after the phishing domain was registered. Validin uses a uniquely thorough approach to capturing DNS resolutions that enable us to capture these invaluable DNS pivots.
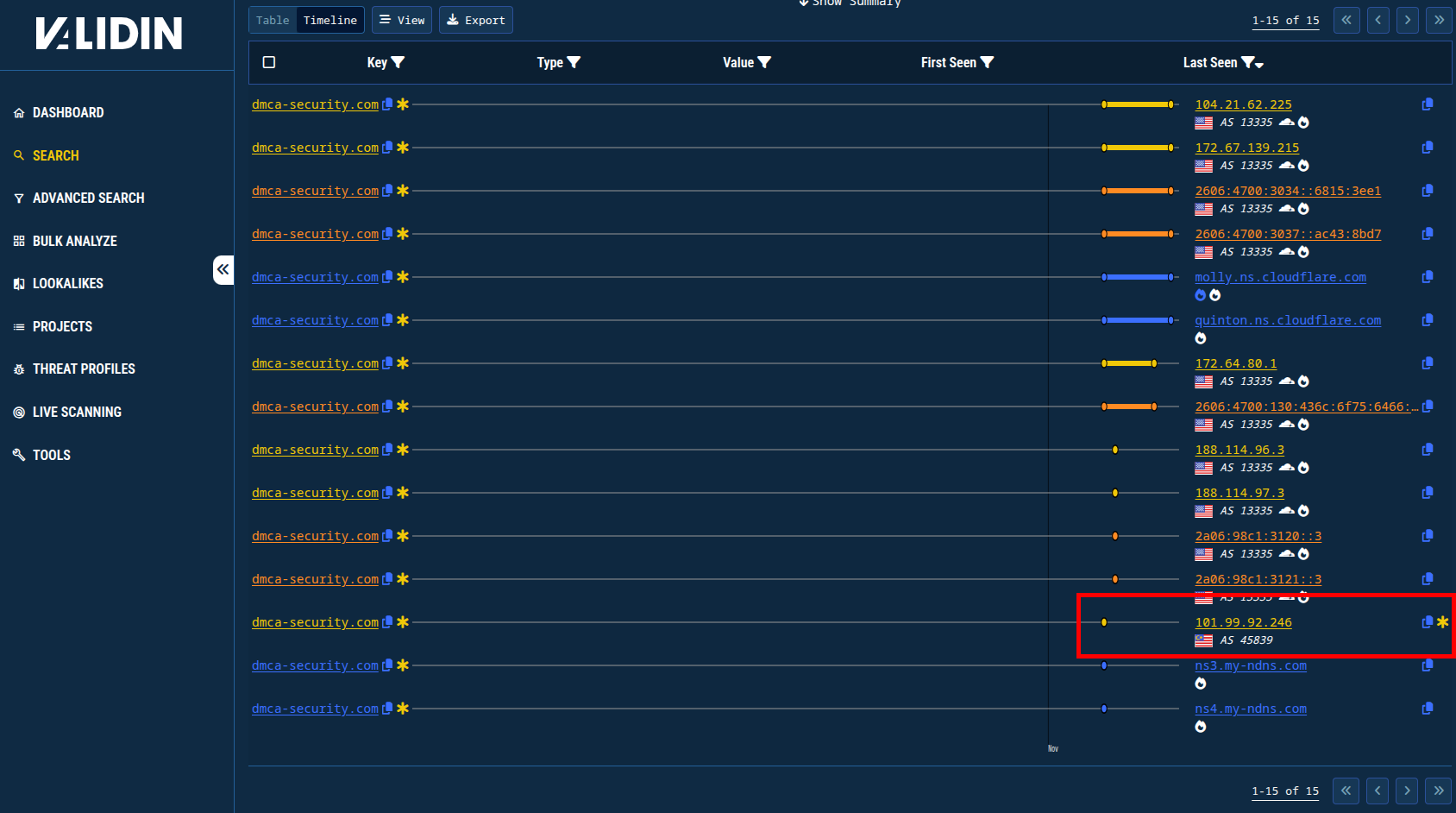
Figure 4. Validin’s DNS history timeline view shows briefly-resolving DNS answers that serve as invaluable pivots.
Even today, there is a new domain resolving to that IP address that is almost certainly related, dmca-abuse[.]video. This domain wasn’t there yesterday, so this IP should be monitored for new activity.
![Figure 5. Showing the additional capture of the domain name dmca-abuse[.]video in DNS history from Validin. Figure 5. Showing the additional capture of the domain name dmca-abuse[.]video in DNS history from Validin.](/images/fake_dmca_notice_scam/image2.png)
Figure 5. Showing the additional capture of the domain name dmca-abuse[.]video in DNS history from Validin.
I’ll add the new domain (and all of the visible subdomains) to my project.
Looking at 101.99.89[.]94, also reported by @wbmmfq, I find DCMA, takedown, YouTube, and other related domain names starting around August 10, 2025.
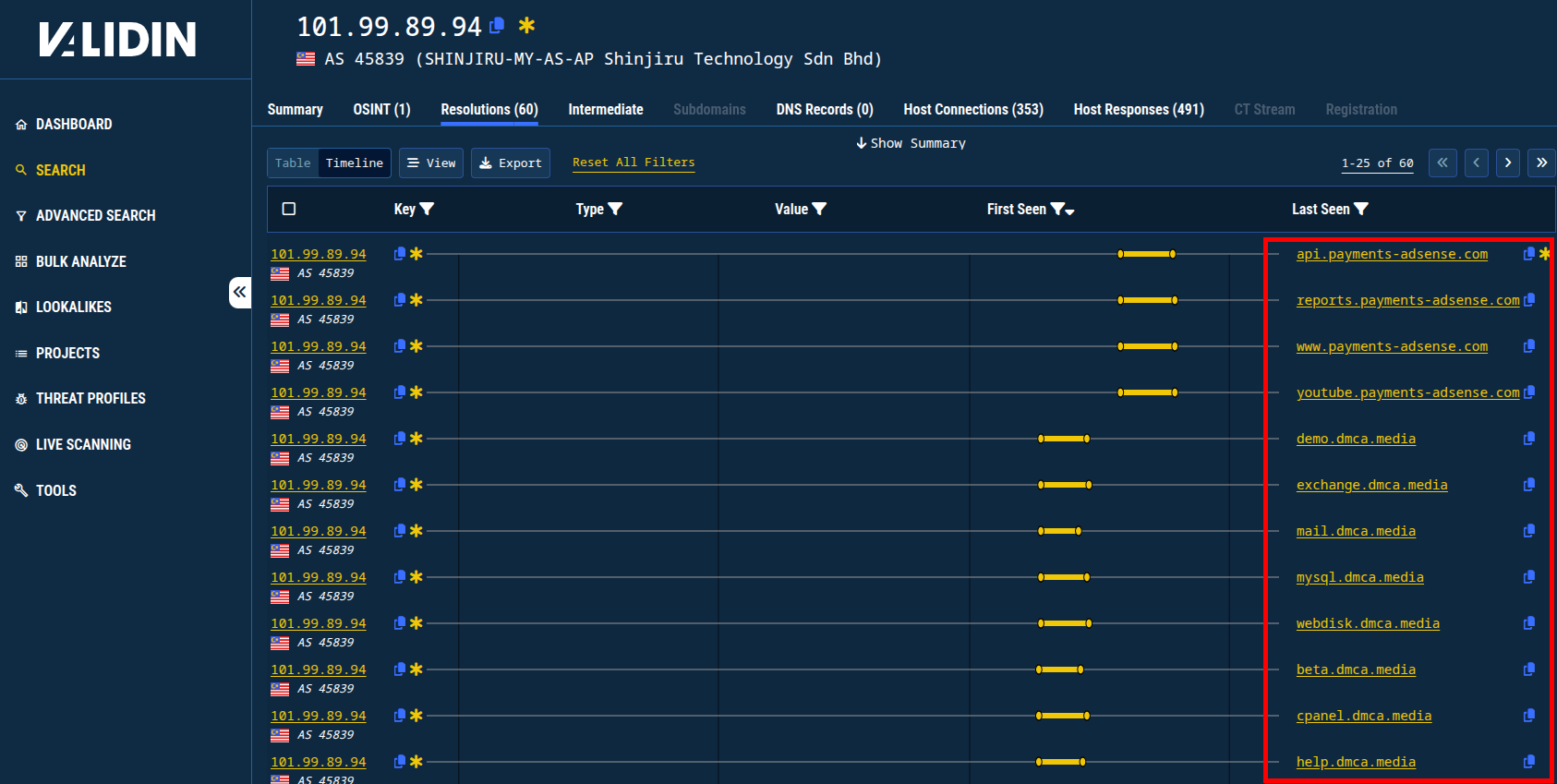
Figure 6. More historic DNS pivoting reveals additional connections to another reported IP address.
Host Response Pivots
Validin also has a uniquely comprehensive approach to measuring how domain names and IP addresses respond over HTTP/S, extracting features from those responses, and allowing analysts and researchers to use those extracted features to identify related domain names and IP addresses. I’ll use those extracted features to attempt to identify other domains that haven’t been flagged as being related.
I’ll begin by visiting the “Host Connections” tab for the origin IP address and selecting only the features with low connectivity. I’ll also filter out any features first seen before August 1, 2025, which is around the time this campaign was initially associated with the IP.

Figure 7. Selecting only the pivots with low connectivity to find rare pivots.
I’ll then quickly go through the remaining pivots, focusing on HOST-BANNER_0_HASH, HOST-HEADER_HASH, HOST-CLASS_0_HASH, HOST-BODY_SHA1, and HOST-FAVICON_HASH to find those that yield new connections using the “Quick Pivots” feature in the UI.

Figure 8. Using Validin’s “Quick Pivot” feature to determine if a pivot is worth following.
Most resulting pivots found things already in my project or were too broad (1000 or more connections). However, a few led to meaningful expansion of confirmed indicators:
takedownabuse[.]com
takedownfl[.]com
worldwidetakedown[.]report
wwtakedown[.]media
86.54.25[.]88
86.54.25[.]77
dmca-global[.]com
www.dmca-global[.]com
payments-adsense[.]com
amazon-us953[.]com
partner.mayandmary[.]net
www.mayandmary[.]net
FAVICON_HASH 863a129608d053b67081c8243c72e9e1 - This favicon hash was observed with this domain and IP cluster from late March to early May 2025.
www.copifyright[.]info
217.119.129[.]87
copifyright[.]info
www.copify[.]net
copify[.]net
famousfoxfederation[.]com
109.71.252[.]89
cavra[.]org
www.cavra[.]org

Figure 9. One version of the favicon used for these DMCA and copyright-related phishing domains.
From these new connections, the IP address 217.119.129[.]87 is interesting because historic DNS links it to cavradocuments[.]top, which was associated by @malwrhunterteam (X) with an open directory hosting malware in April 2025.
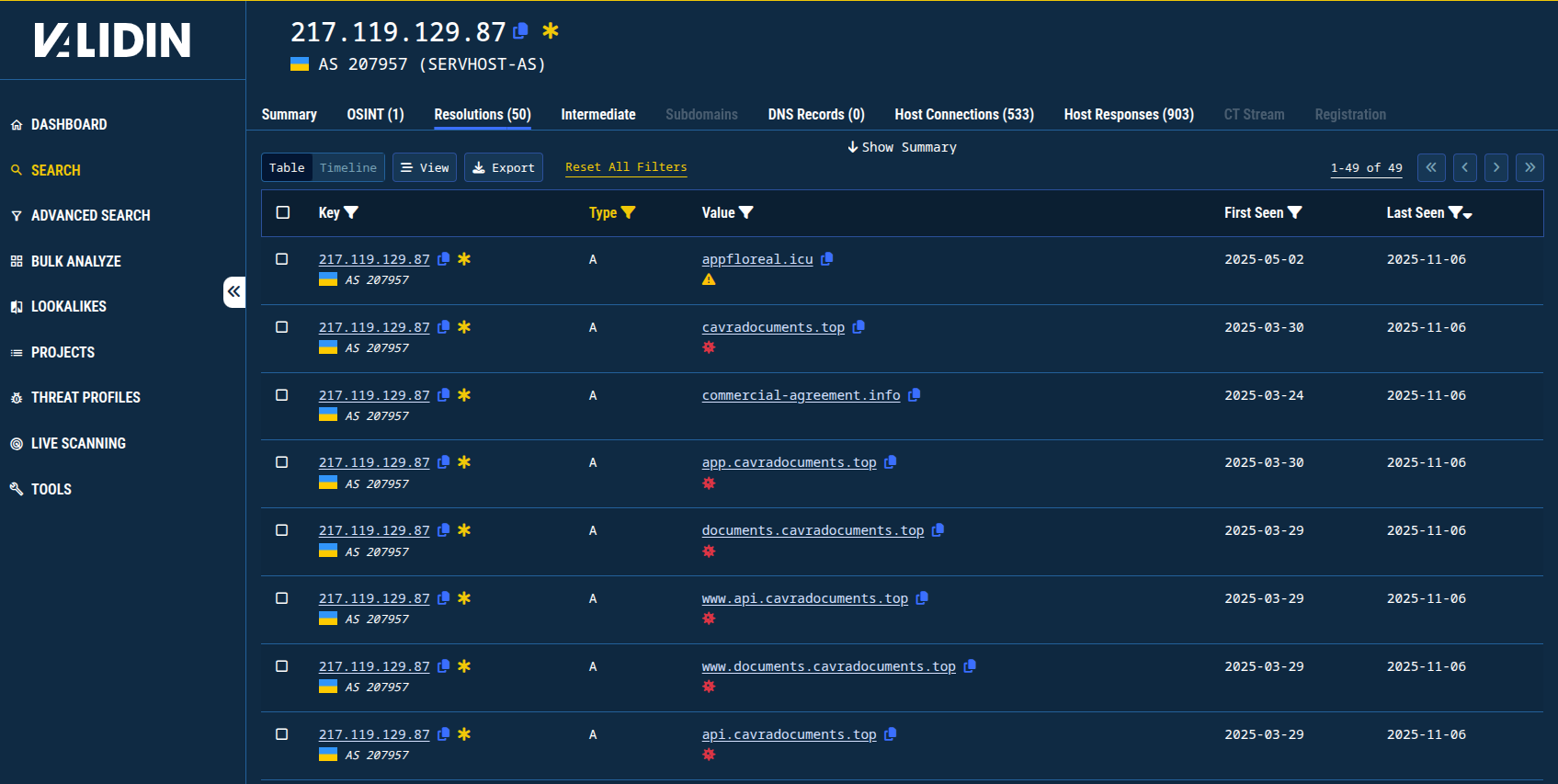
Figure 10. Passive DNS history (with filters for recency) of one of the IP addresses connected by favicon hash to malicious domain names.
That IP address is also associated with the following suspicious domain names:
appfloreal[.]icu
floreal[.]icu
appfree[.]icu
cavradocuments[.]top
commercial-agreement[.]info
bookwhisp[.]com
C2 IP Pivots
From the any.run analysis, there were 2 connections to IP addresses:
http[:]//185.153.198[.]115/https[:]//45.80.231[.]244/gateway/fc2lje6m.mprui
The first, 185.153.198.115, returns a very generic HTTP response on port 80 and a unique certificate on port 3389 (RDP). Neither of these responses lend themselves to pivoting, but with additional knowledge of how this IP address was used, it may be possible to investigate further.
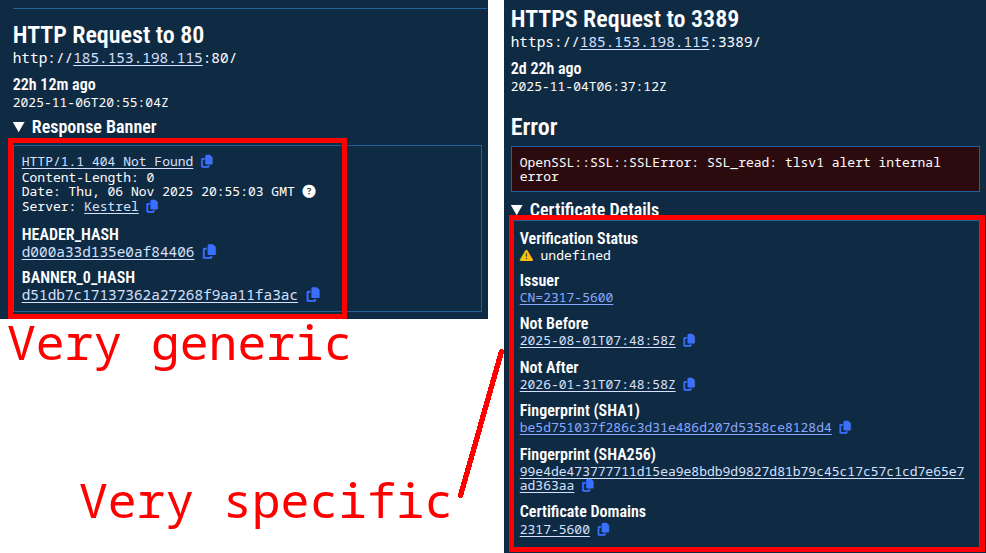
Figure 11. Two recent responses on ports 80 and 443 from an IP observed in the any.run analysis.
The IP address 45.80.231[.]244, on the other hand, returned features on port 443 (the port shown by any.run) that might lead to related infrastructure, including the BANNER_0_HASH 5dab1fa5f7d42e5eca2385ce3dad1f03. This is a hash that captures the very specific server response highlighted below, which includes the location path, server name and version, and full response line:
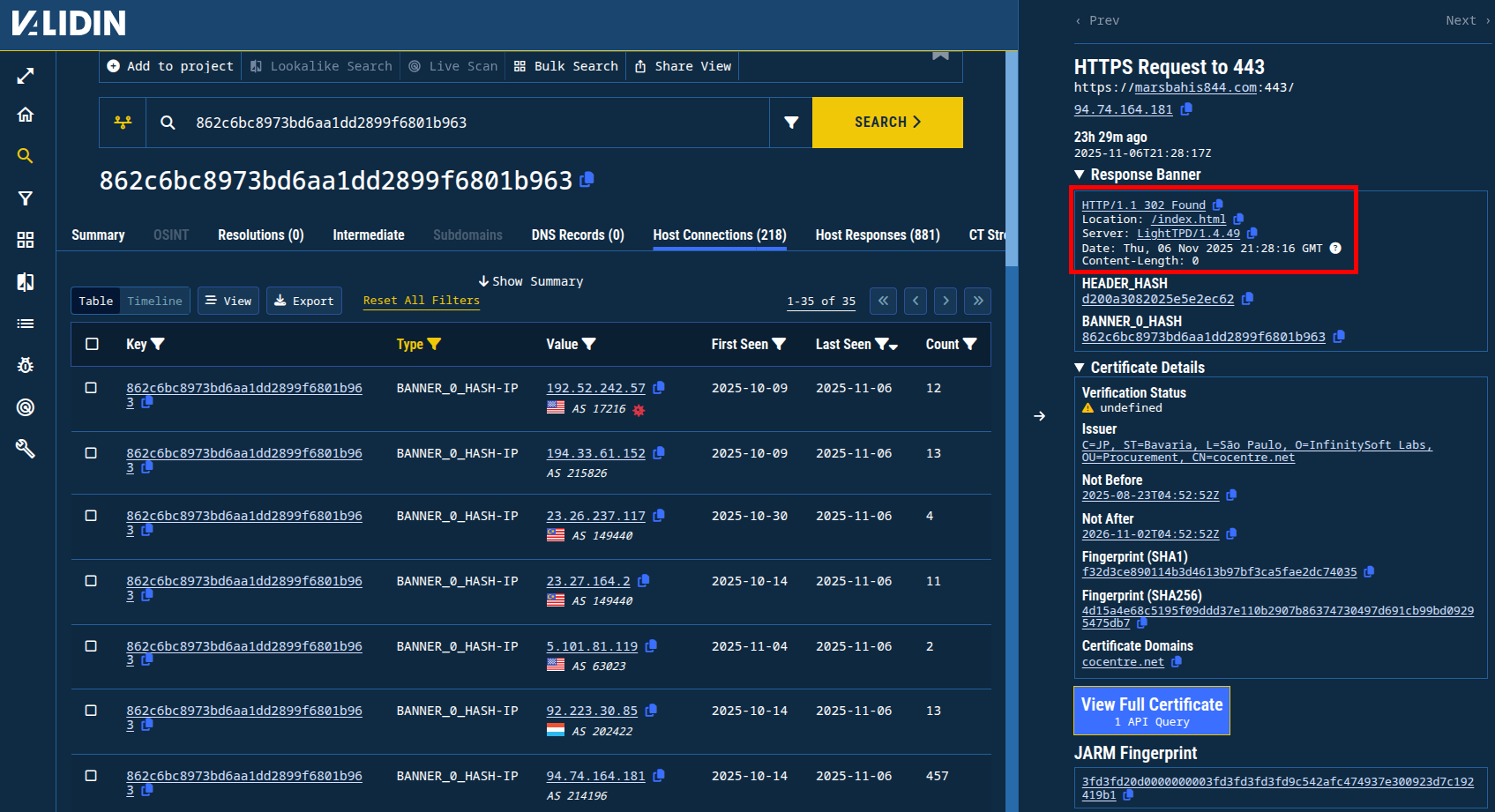
Figure 12. IPs returning the banner highlighted in red, which corresponds to the banner hash 5dab1fa5f7d42e5eca2385ce3dad1f03.
A notable trait of nearly all of these matching IPs (except for 62.3.15[.]94) is the certificate: it’s self-signed and appears to use randomized values for country, state, city, organization, organization unit, and common name. This is apparent in the view below:
/C=AT/ST=Georgia/L=Melbourne/O=PhantomTech AI/OU=Web/CN=throughcanada.net
/C=AT/ST=Georgia/L=Paris/O=PhantomTech Works/OU=Web/CN=processa.digital
/C=AT/ST=Moscow/L=Houston/O=InfinitySoft Labs/OU=Testing/CN=technologystart.company
/C=BR/ST=Washington/L=Paris/O=Elevatech Dynamics/OU=HR/CN=optionsmean.io
/C=CA/ST=Ontario/L=Munich/O=FuturistIQ Media/OU=Network/CN=writtendirector.solutions
/C=CH/ST=Illinois/L=São Paulo/O=NeuroNet Systems/OU=Sales/CN=privatefebruary.company
/C=CH/ST=New York/L=Moscow/O=Linkedin Resources/OU=Frontend/CN=requestpoints.org
/C=CH/ST=North Carolina/L=Vancouver/O=SilicoBrain Corporation/OU=Marketing/CN=janrights.company
/C=DE/ST=Massachusetts/L=Chicago/O=QuantumByte Dynamics/OU=Analytics/CN=upbaby.co
/C=ES/ST=London/L=San Francisco/O=VirtuSphere Analytics/OU=Planning/CN=checkmanagement.solutions
/C=ES/ST=Ontario/L=Chicago/O=NeuroNet Design/OU=Web/CN=movieare.co
/C=ES/ST=Texas/L=Moscow/O=ZenithCode Media/OU=Marketing/CN=nextdisplay.systems
/C=FR/ST=Massachusetts/L=San Francisco/O=MirageMatrix Consultants/OU=Finance/CN=frontlight.cloud
/C=GB/ST=Bavaria/L=Berlin/O=NexGen Enterprises/OU=Integration/CN=payarchives.systems
/C=GB/ST=Moscow/L=Chicago/O=Facebook Platform/OU=Procurement/CN=authorlong.software
/C=GB/ST=Quebec/L=Moscow/O=InfinitiCode Works/OU=Frontend/CN=acceptedbetter.global
/C=IN/ST=North Carolina/L=Houston/O=PhantomTech Consultants/OU=Support/CN=doingred.global
/C=IN/ST=Tokyo/L=Vancouver/O=FusionFlare Systems/OU=R&D/CN=plangolf.solutions
/C=JP/ST=Bavaria/L=São Paulo/O=InfinitySoft Labs/OU=Procurement/CN=cocentre.net
/C=JP/ST=Georgia/L=Sydney/O=CodeCrafters Enterprises/OU=Integration/CN=awayjan.network
/C=JP/ST=Illinois/L=Tokyo/O=Amazon Dynamics/OU=AI/CN=unitedreading.company
/C=JP/ST=Sydney/L=Berlin/O=Apple Solutions/OU=Sales/CN=gamecall.cloud
/C=JP/ST=Washington/L=Toronto/O=Siri Technologies/OU=R&D/CN=peopleno.io
/C=JP/ST=Île-de-France/L=Munich/O=Orbitronics Software/OU=Security/CN=californiare.systems
/C=KR/ST=Sydney/L=London/O=SonicSeed Resources/OU=AI/CN=linuxmade.net
/C=KR/ST=São Paulo/L=San Francisco/O=InfinitySoft Studio/OU=Customer Success/CN=saygoing.cloud
/C=MX/ST=North Carolina/L=Munich/O=QuantumQuotient Analytics/OU=Operations/CN=augustwell.dev
/C=MX/ST=Tokyo/L=Houston/O=NeonByte Platform/OU=Engineering/CN=likeknowledge.systems
/C=NL/ST=Ontario/L=Atlanta/O=SonicSeed Networks/OU=Frontend/CN=xfood.software
/C=SE/ST=Moscow/L=Tokyo/O=Microsoft Inc/OU=Network/CN=archivespress.solutions
/C=SE/ST=North Carolina/L=Vancouver/O=Facebook IoT/OU=Web/CN=playflorida.app
/C=US/ST=Ontario/L=Tokyo/O=NeuroNet Systems/OU=Analytics/CN=coursematerials.com
/C=ZA/ST=Georgia/L=Moscow/O=InfinitySoft Technologies/OU=HR/CN=ifstates.global
The IPs sharing this banner hash and certificate configuration since August 2025 include:
5.101.81[.]119
94.74.191[.]123
144.172.110[.]194
23.26.237[.]117
83.217.208[.]54
94.103.1[.]38
45.80.231[.]244
23.27.164[.]2
64.188.91[.]83
92.223.30[.]85
94.74.164[.]181
185.65.202[.]76
192.52.242[.]57
194.33.61[.]152
80.97.160[.]202
193.221.200[.]48
198.105.126[.]187
88.119.169[.]128
95.164.53[.]62
166.88.117[.]149
185.102.115[.]211
62.60.179[.]33
91.196.34[.]202
64.188.77[.]34
185.102.115[.]194
62.3.15[.]94
85.209.158[.]14
178.17.62[.]16
192.124.176[.]56
193.68.89[.]59
185.100.168[.]91
77.110.127[.]54
195.66.25[.]103
95.217.96[.]242
195.66.25[.]23
These IP addresses also appear to be active for between a few hours and a few weeks and are rotating regularly:
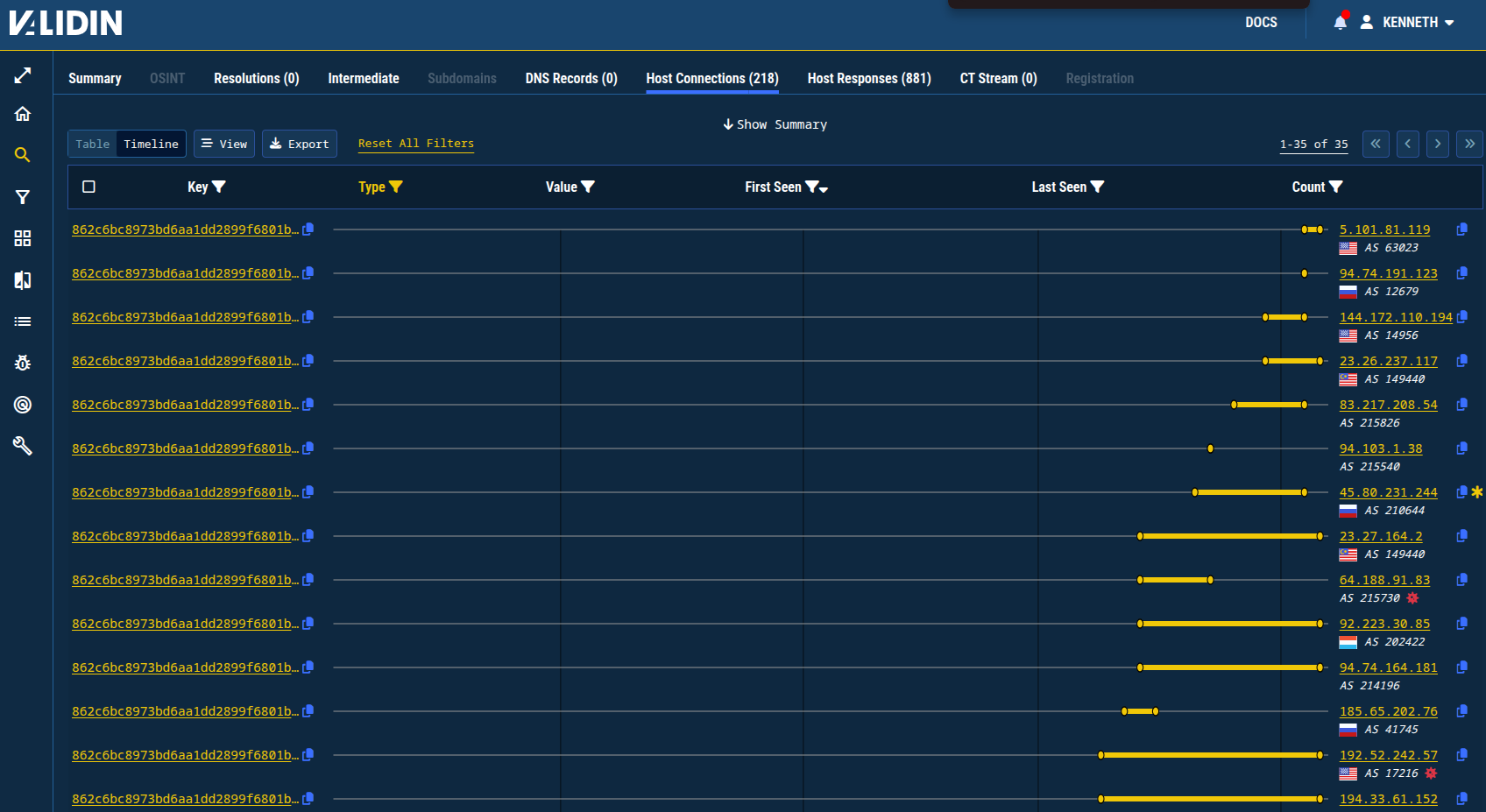
Figure 13. Validin timeline of banner hashes associated with different IP addresses.
These IPs also appear to host domain names that use some kind of domain generation algorithm. Pivoting from the host response features in these connected domains will result in a large network of related domains, but it’s unclear how related they are to the original set of indicators. So, I’ll leave this as an interesting footnote for future research.
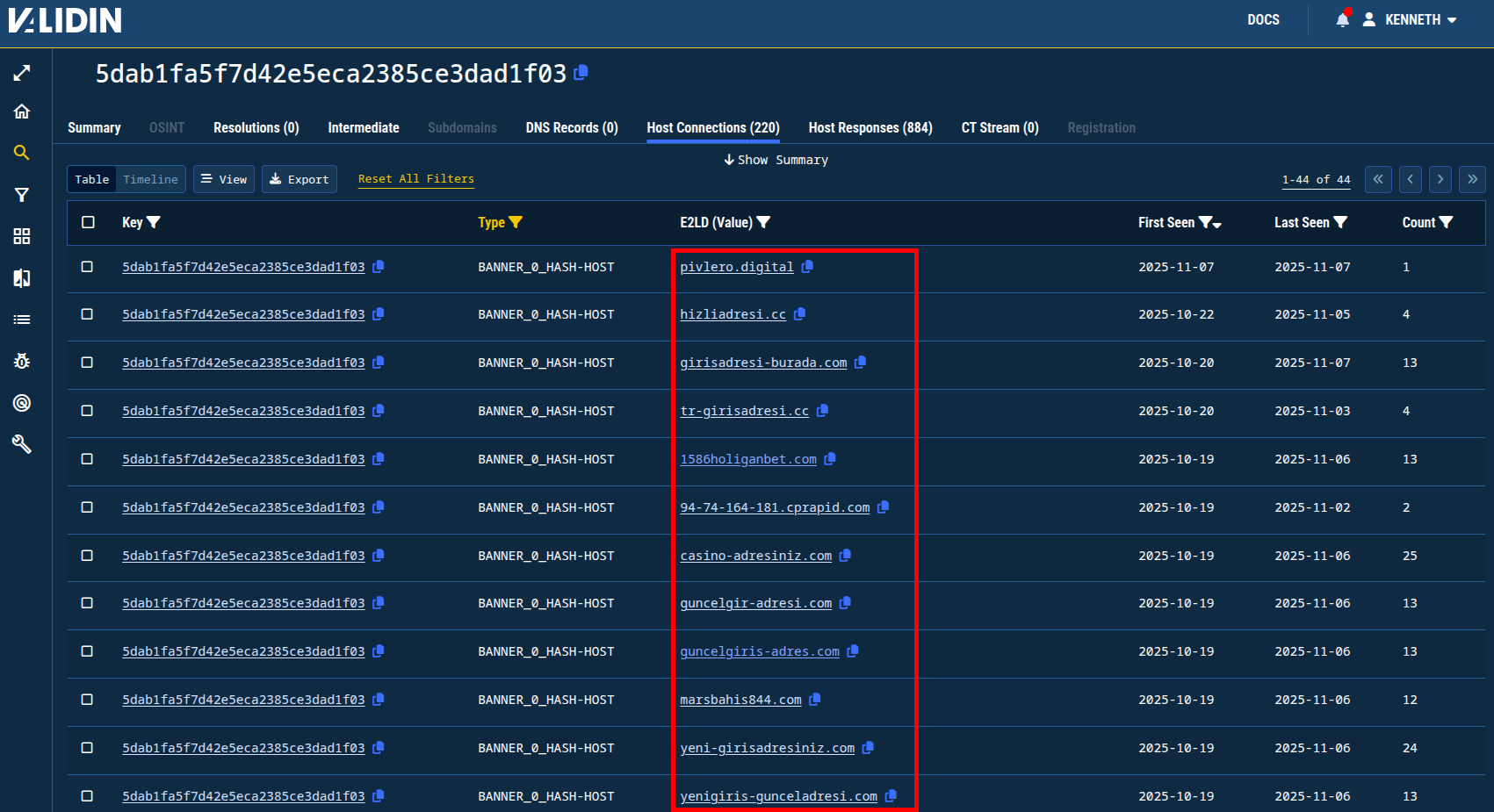
Figure 14. A network of domains that appear to employ some kind of domain generation algorithm that share host response header similarities and resolve to IPs identified as part of the C2 network.
C2 Domain Pivots
In the live analysis on any.run, the malicious executable reached out to ms-team-ping4[.]com and several other similar domain names. The domain ms-team-ping4[.]com does not return any content when contacted directly through an HTTP GET request. It would seem at first glance that there wouldn’t be much to pivot from given that the domain also resolves to Cloudflare IP addresses and name servers, which are notoriously dead ends for traditional DNS-based pivoting.
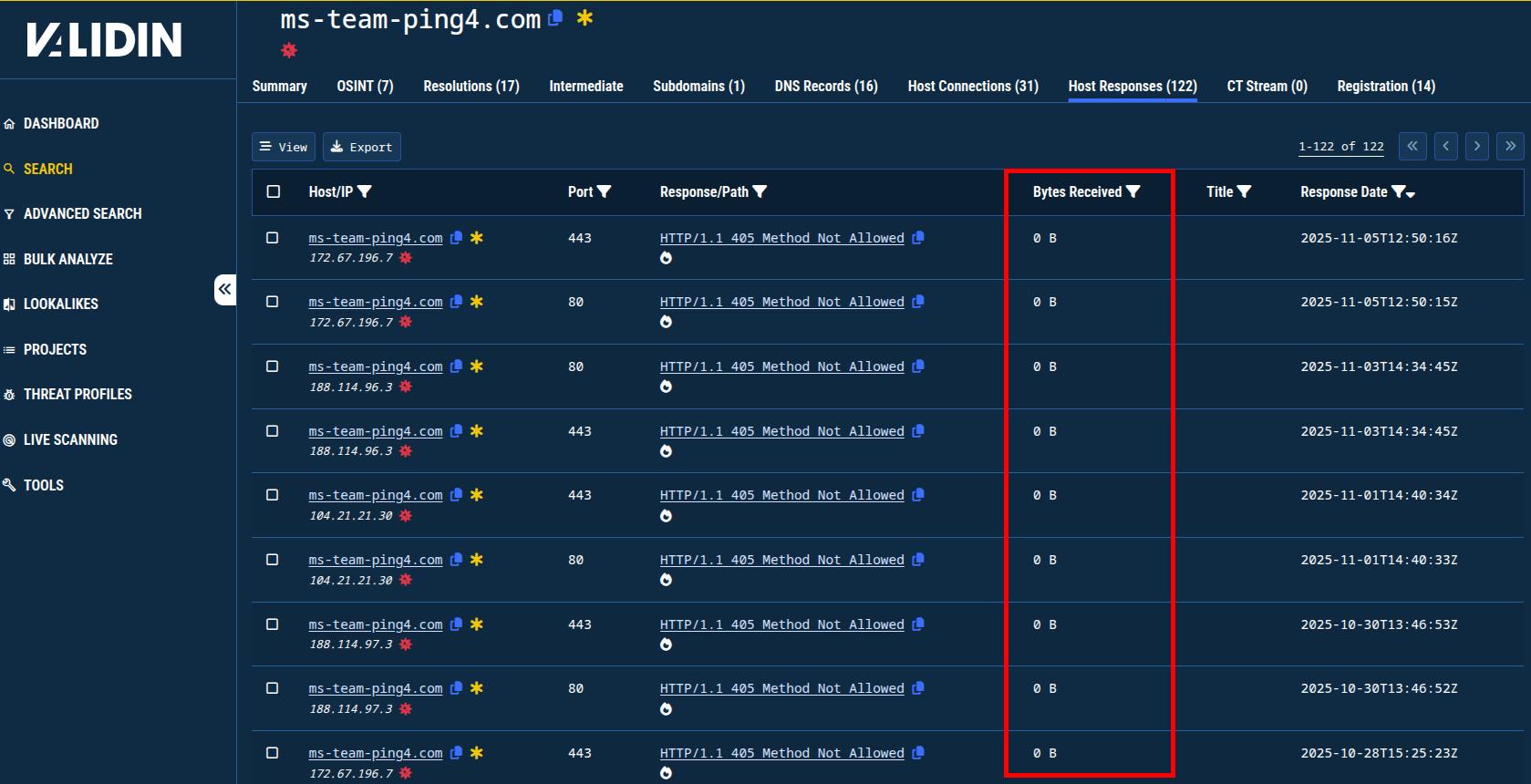
Figure 15. All of the responses recorded for this domain are empty.
However, the response banners, even from Cloudflare, appear to have enough uniqueness to them that they generate highly interesting header hashes, including:
d40097143f9b1abeee08d40097143f9b99e0163dd40097143f9bb3172887
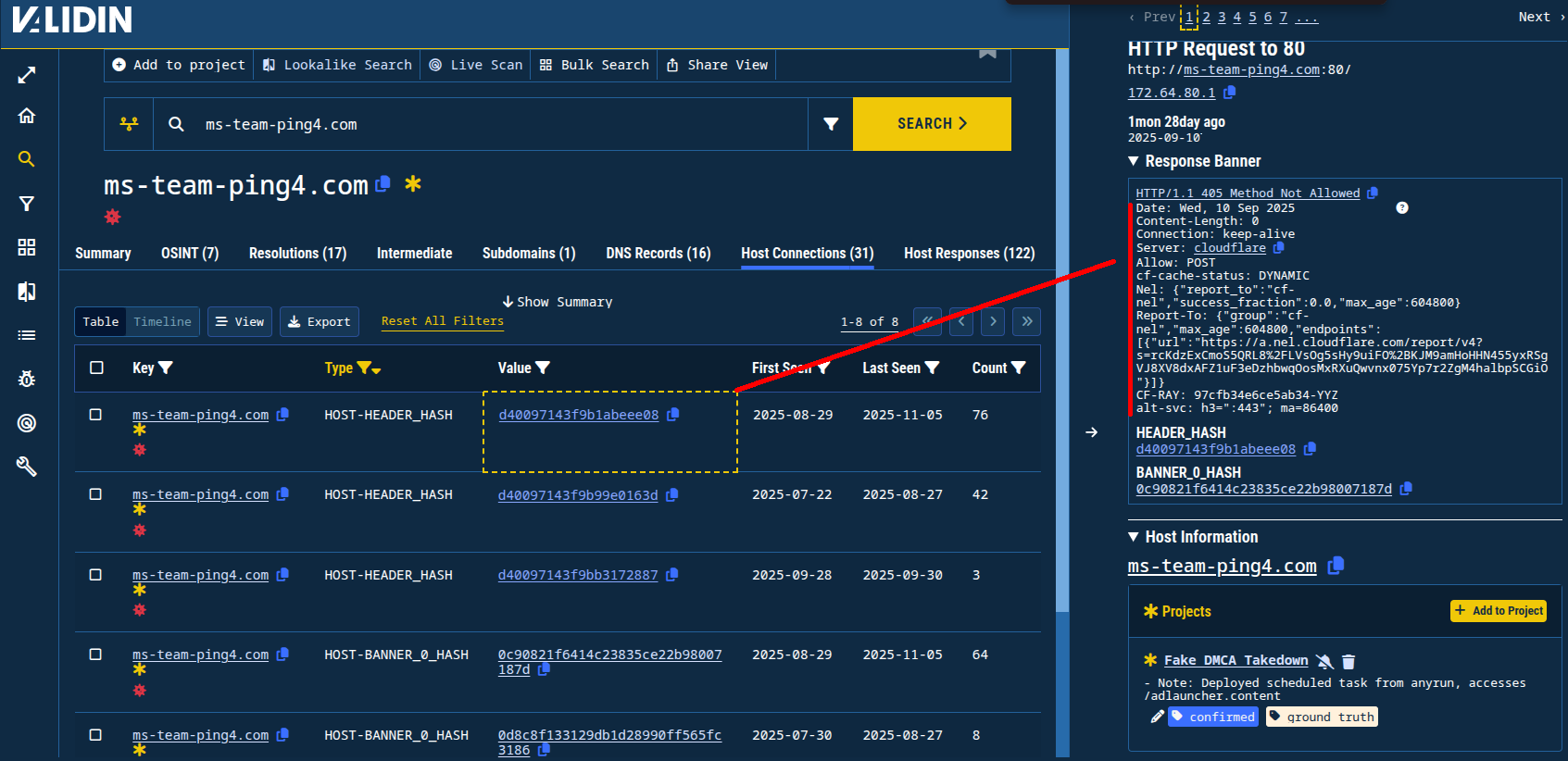
Figure 16. Highlighting the virtual host response banner that generated the header hash d40097143f9b1abeee08.
Pivoting from these banner hashes yields domains mostly already flagged in earlier public reporting, but also reveals a few newer variations not previously identified. These domains have similar naming patterns, but look slightly different:
health-smooth-eu1[.]combucket-aws-s2[.]combucket-aws-s1[.]com
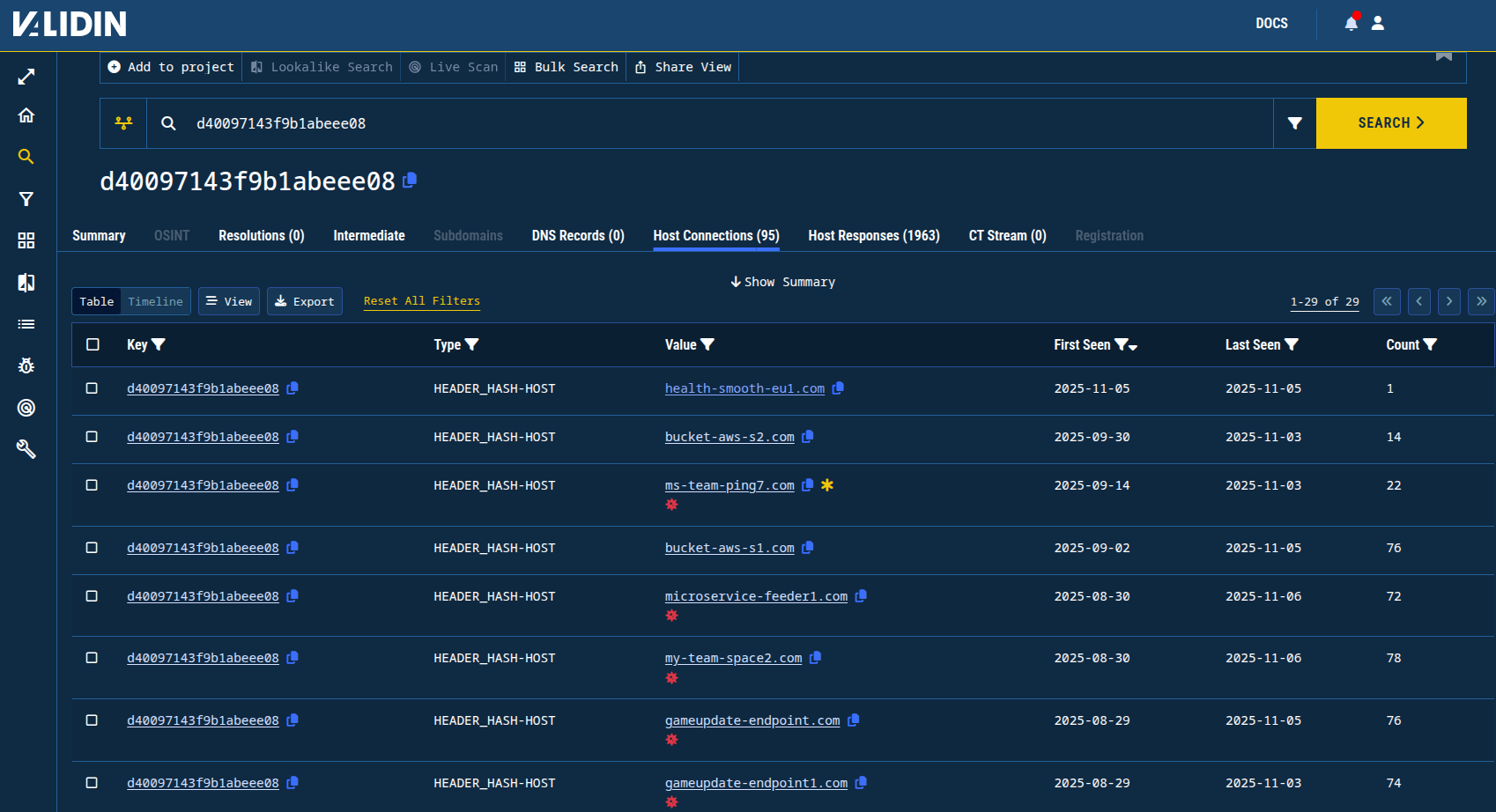
Figure 17. Header hash results for d40097143f9b1abeee08 showing a few domains not previously identified.
Conclusion
Like we’ve seen with invoice scams, targeted scams used to take a lot of resources to pull off convincingly, but the barrier has never been lower for attackers with the availability of AI tools. Validin provides defenders the tools they need to investigate, detect, and proactively block countless varieties of threats on the public internet and the Validin team is dedicated to providing the best possible platform to defenders in service of that core mission.
Validin enables:
- identifying and tracking the TTPs used by attackers through a comprehensive and multi-layered approach to data collection and insight correlation
- comprehensive and exhaustive coverage of DNS history enabling insights into attacker infrastructure that would otherwise go unnoticed
- uniquely thorough and granular insights into virtual host response history not found anywhere else
Ready to elevate your threat hunting, threat attribution, and incident response efforts? Whether you’re an individual analyst or part of a larger enterprise team, Validin offers solutions that meet your needs. Individual users can create a free account and self-upgrade to access more advanced features and data.
Part of a team? Contact us today to explore our enterprise options and discover how Validin can power your organizations with powerful tools and unparalleled data. Let Validin help you work smarter, faster, and more effectively in the fight against cyber threats.
Indicators
The complete set of domains (E2LDs only) that are likely related to this campaign:
amazon-us953[.]com
app-updater[.]app
app-updater1[.]app
app-updater2[.]app
appfloreal[.]icu
appfree[.]icu
azure-expresscontainer1[.]com
bookwhisp[.]com
bucket-aws-s1[.]com
bucket-aws-s2[.]com
cavra[.]org
cavradocuments[.]top
collaborations[.]center
commercial-agreement[.]info
copify[.]net
copifyright[.]info
dmca-abuse[.]com
dmca-abuse[.]video
dmca-global[.]com
dmca-guard[.]com
dmca-guardian[.]com
dmca-hub[.]com
dmca-security[.]com
dmca-shield[.]com
dmca[.]center
dmca[.]media
dmca[.]social
famousfoxfederation[.]com
fast-node[.]com
floreal[.]icu
gameupdate-endpoint[.]com
gameupdate-endpoint1[.]com
health-smooth-eu1[.]com
mayandmary[.]net
microservice-feeder1[.]com
ms-dns-resolver1[.]com
ms-onedrive-updater1[.]com
ms-onedrive-updater2[.]com
ms-team-connect[.]com
ms-team-connect1[.]com
ms-team-connect2[.]com
ms-team-connect3[.]com
ms-team-ping[.]com
ms-team-ping1[.]com
ms-team-ping10[.]com
ms-team-ping2[.]com
ms-team-ping3[.]com
ms-team-ping4[.]com
ms-team-ping5[.]com
ms-team-ping6[.]com
ms-team-ping7[.]com
ms-team-ping8[.]com
ms-team-ping9[.]com
my-team-space[.]com
my-team-space1[.]com
my-team-space2[.]com
my-team-space3[.]com
my-team-space4[.]com
national-competition-arise00[.]org
partners-invitation[.]media
partners-invitation[.]social
payments-adsense[.]com
phoenixnap-sourceforge1[.]com
shopliokre[.]com
syswolupdatesupp1[.]com
takedownabuse[.]com
takedownfl[.]com
takedownglobal[.]media
takedownsecurity[.]com
worldwidetakedown[.]report
wwtakedown[.]media
youtube-dmca[.]com
youtube-partners[.]com
IPs that are likely related to this campaign:
5.101.81[.]119
23.26.237[.]117
23.27.164[.]2
45.80.231[.]244
62.3.15[.]94
62.60.179[.]33
64.188.77[.]34
64.188.91[.]83
77.110.127[.]54
80.97.160[.]202
83.217.208[.]54
85.209.158[.]14
86.54.25[.]77
86.54.25[.]88
88.119.169[.]128
91.196.34[.]202
92.223.30[.]85
94.74.164[.]181
94.74.191[.]123
94.103.1[.]38
95.164.53[.]62
95.217.96[.]242
101.99.89[.]94
101.99.92[.]246
109.71.252[.]89
144.172.110[.]194
166.88.117[.]149
178.17.62[.]16
185.65.202[.]76
185.100.168[.]91
185.102.115[.]194
185.102.115[.]211
185.153.198[.]115
192.52.242[.]57
192.124.176[.]56
193.68.89[.]59
193.221.200[.]48
194.33.61[.]152
195.66.25[.]23
195.66.25[.]103
198.105.126[.]187
217.119.129[.]87
