Exploring the network infrastructure of the Notepad++ Compromise
On February 2, 2026, Notepad++ disclosed that part of its upgrade distribution channel was compromised by state-sponsored hackers. Rapid7 provided some additional insight about the infection tools that were deployed as part of the attack, including file and network indicators leveraged in the attack.
In our report, we’ll show you how to find:
- The likely origin IP of a Cobalt Strike beacon domain reported by Rapid7
- An additional IP address associated with the C2 domain
- A likely additional C2 domain
- An additional source IP address that may have been used as a malicious file host
Attack Summary
The attack appears to have happened at the server used by the hosting provider for Notepad++, which per Validin’s DNS history was either Hostinger directly or a shared hosting reseller that uses Hostinger. The threat actor used their access to provide malicious updates by selectively redirecting users to an attacker-controlled server.
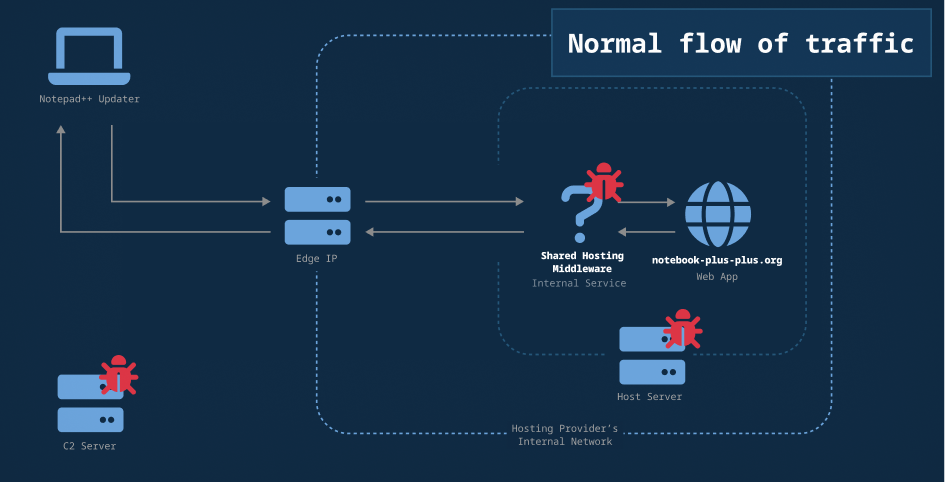
Figure 1. The flow of traffic when no redirect was injected
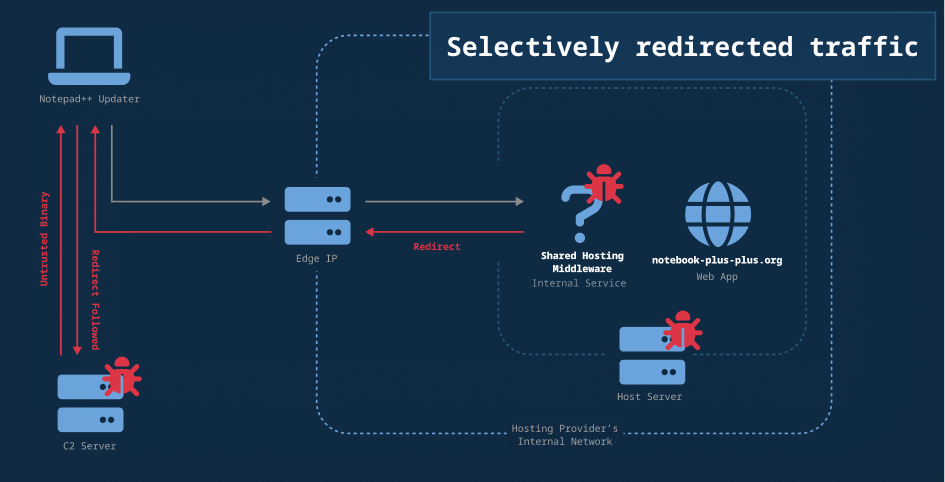
Figure 2. The flow of traffic when redirected via compromised internal services
A note from the hosting provider indicates that the Notepad++ account was the only account targeted despite the attackers potentially having access to many other accounts.
A timeline of the events as we understand them:
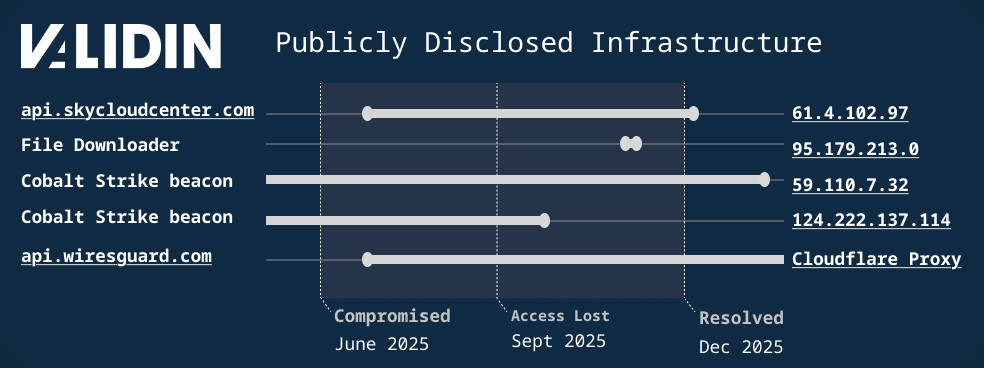
Figure 3. Timeline of publicly-disclosed infrastructure reconstructed with Validin data.
Per the update on the incident on the Notepad++ blog, the attackers maintained access to the shared server starting June 2025 and ending sometime between November 10, 2025 and December 2, 2025.
Network Indicators
The report from Rapid7 contains several public network indicators along with context around how they were used:
95.179.213[.]0- provided the first suspicious file downloaded in the infection chainapi[.]skycloudcenter[.]com- Command and Control (C2) provider (HTTPS, port 443)61.4.102[.]97- IP address forapi[.]skycloudcenter[.]comapi[.]wiresguard[.]com- domain used for Cobalt Strike beacon (HTTPS, port 443)59.110.7[.]32- IP hosting Cobalt Strike beacon (HTTP, port 8880)124.222.137[.]114- IP hosting Cobalt Strike beacon (HTTP, port 9999)
While we don’t have timestamps in the report, we can infer some details about behavior from the data in Validin’s DNS and host response history.
Initial Download IP
The IP 95.179.213[.]0 is in AS-CHOOPA (Vultr). The banners captured by Validin since June 1, 2025 indicate 3 distinct operational periods:
-
2025-08-19 to 2025-08-19
-
Port 443 uses a generic “CloudFlare Origin Certificate” and an empty response
-
Port 22 returns this SSH start line, indicating an Ubuntu install:
SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.11 -
2025-09-30 to 2025-09-30
-
Port 22 returns this SSH start line, indicating aDebian install:
SSH-2.0-OpenSSH_9.2p1 Debian-2+deb12u7 -
2025-10-14 through 2025-12-04
-
Port 80 returns “HTTP/1.1 200 OK” with the response body “Service is unavailable.” until 2025-10-19, followed by “HTTP/1.1 403 Forbidden” with a generic Apache error response body from 2025-10-21 until 2025-12-04
-
Port 22 returns this SSH start line, indicating an Ubuntu install:
SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.13
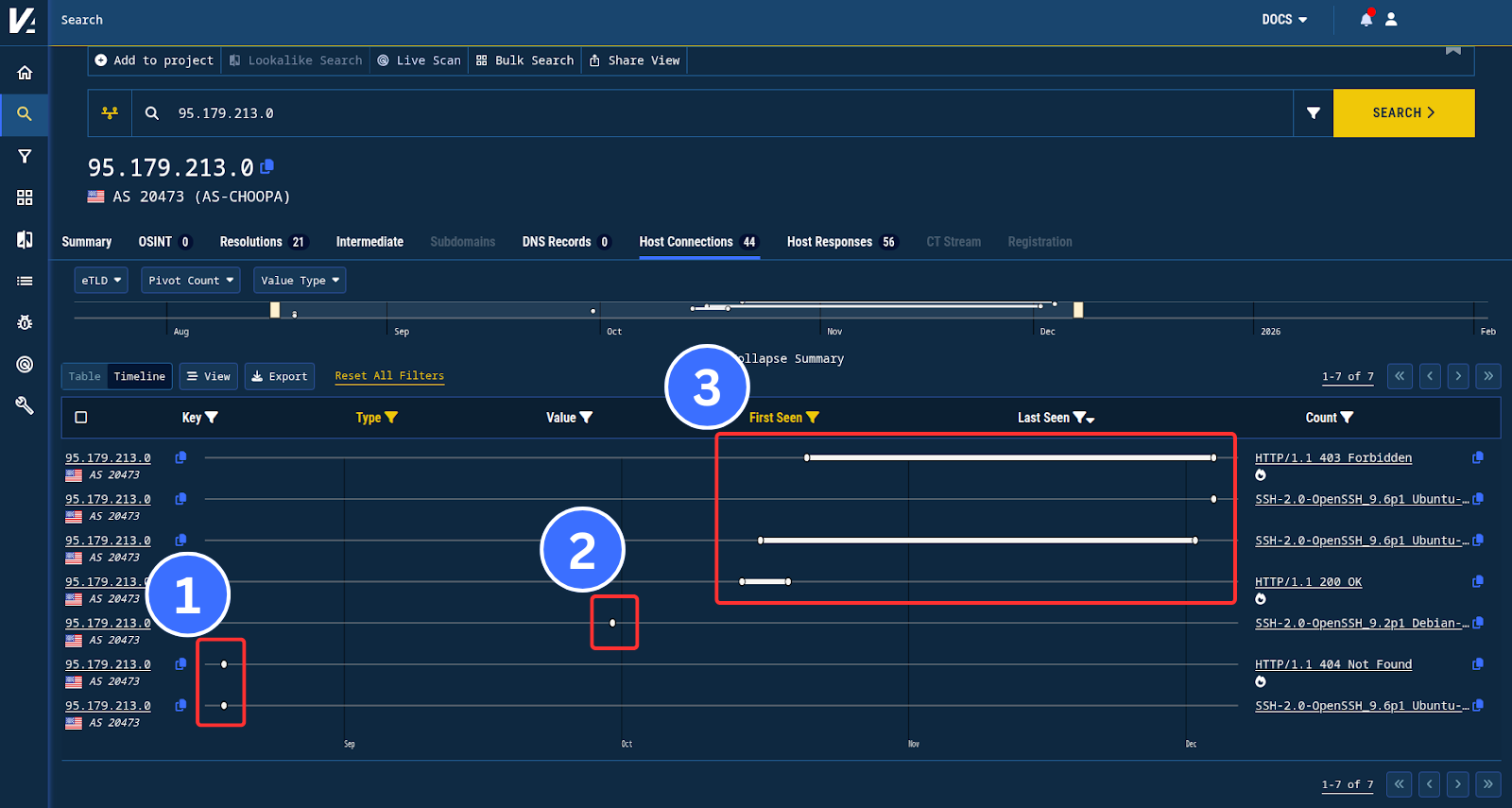
Figure 4. Three distinct activity periods observed on the initial download IP.
C2 Domain
The C2 domain api[.]skycloudcenter[.]com was active from August 31, 2025 until December 9, 2025 on two different IP addresses on AS 55720 (Gigabit Hosting):
61.4.102[.]97- in the Rapid7 report, active until 2025-12-03160.250.93[.]48- resolved for about 6 days until 2025-12-09
Since December 10, 2025, the C2 domain has only resolved to the bogon 127.0.0.1.
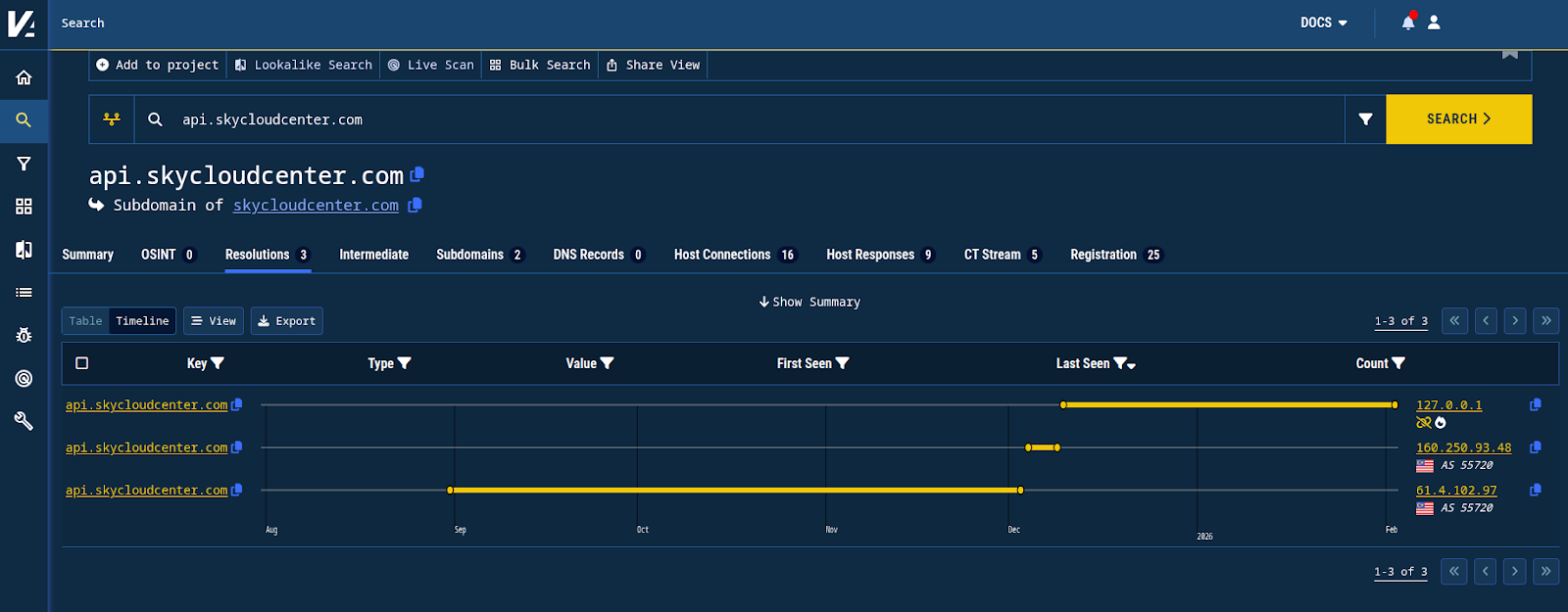
Figure 5. DNS history detail for the known C2 domain shows relatively brief use of another IP, followed by direction to a bogon IP range.
The parent domain was registered on August 25, 2025 on Namecheap and has not been configured with A records (IPv4 addresses) since the most recent registration (the domain has been registered before, most recently from 2021 until 2022).
CS Beacon Domain
The Cobalt Strike (CS) Beacon Domain, api[.]wiresguard[.]com, has been active since at least June 13, 2025 and has been hosted on Cloudflare the entire time.
Like the reported C2 domain, the parent domain was also registered on Namecheap, but 5 months earlier than the C2 domain on March 19, 2025.
Interestingly, since at least March 26, 2025, the IP address 103.159.133[.]178 has returned a self-signed certificate with the domain wiresguard[.]com in the Common Name field. During this time, just like api[.]wiresguard[.]com, the IP address returned a zero-byte “HTTP/1.1 404 Not Found” response on port 443, hinting that it might be the origin IP for api[.]wiresguard[.]com.
![Figure 6. One of these IPs is not like the others - 103.159.133[.]178, also on AS 55720 (Gigabit Hosting) like the reported Cobalt Strike beacon IPs. Figure 6. One of these IPs is not like the others - 103.159.133[.]178, also on AS 55720 (Gigabit Hosting) like the reported Cobalt Strike beacon IPs.](/images/npp_compromise/image8.png)
Figure 6. One of these IPs is not like the others - 103.159.133[.]178, also on AS 55720 (Gigabit Hosting) like the reported Cobalt Strike beacon IPs.
![Figure 7. The self-signed certificate on 103.159.133[.]178. Figure 7. The self-signed certificate on 103.159.133[.]178.](/images/npp_compromise/image9.png)
Figure 7. The self-signed certificate on 103.159.133[.]178.
CS Beacon IP
The IP address 59.110.7[.]32 was confirmed by Rapid7 to have been used as a Cobalt Strike beacon IP on port 8880. In Validin, we see that port 22 has been open and responding with the same OpenSSH start line since March 16, 2025. Validin shows that port 8880 was open until January 27, 2026. (Note: Validin added IPv4-wide port coverage for port 8880 in mid-January 2026.)
![Figure 8. Recent port banners showing the port 8880 stopped responding on 59.110.7[.]32 around January 27. Figure 8. Recent port banners showing the port 8880 stopped responding on 59.110.7[.]32 around January 27.](/images/npp_compromise/image10.png)
Figure 8. Recent port banners showing the port 8880 stopped responding on 59.110.7[.]32 around January 27.
DNS Pivots
The C2 domain api[.]skycloudcenter[.]com resolved to an additional IP not mentioned in the Rapid7 report for a few days in early December: 160.250.93[.]48. Pivoting on this IP address, we find an additional domain name started resolving to it shortly after that time window: api.cloudtrafficservice[.]com. This domain continues to resolve to 160.250.93[.]48 as of the time this blog post was written.
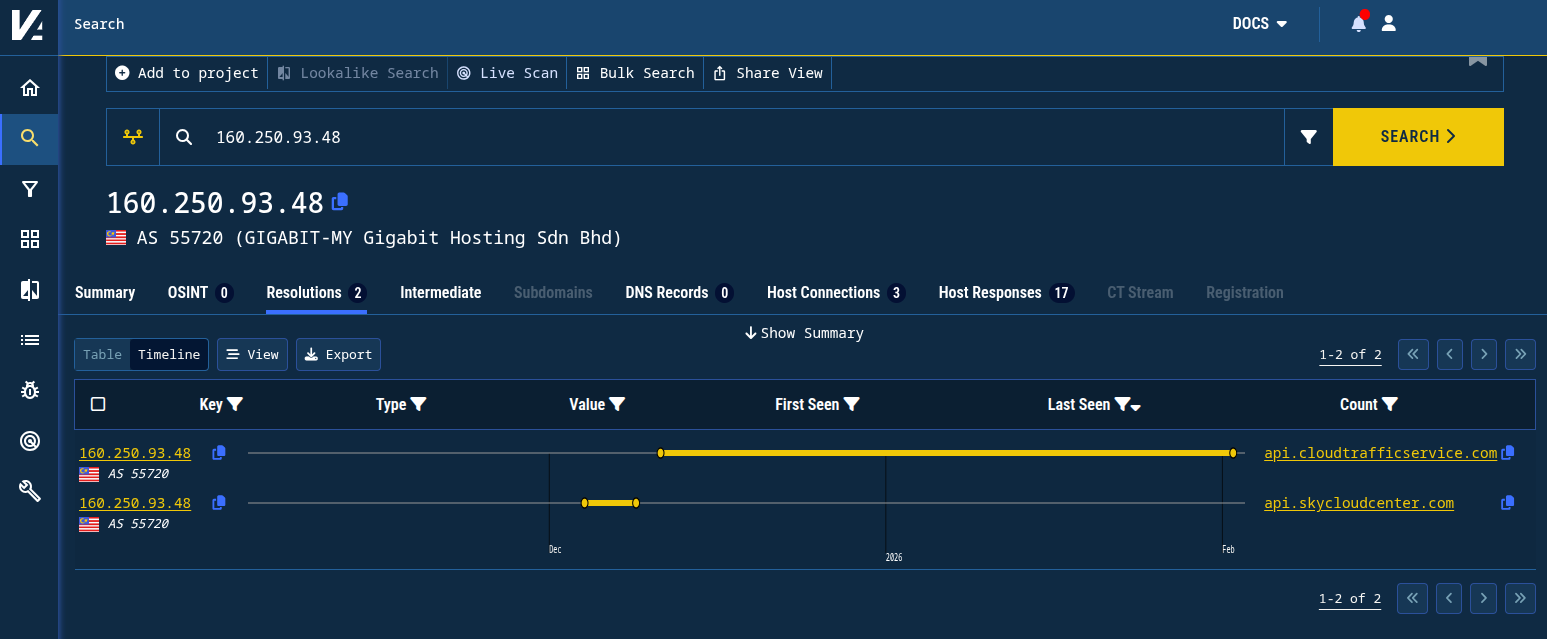
Figure 9. Pivoting on the IP address reveals a similarly-named domain name.
The domain name cloudtrafficservice[.]com was registered on December 3, 2025 on Namecheap, just like the C2 and CS beacon domains, and like skycloudcenter[.]com, does not directly resolve to an IP address.
We can also see that the registration details were updated on December 5, 2025, and that the name servers changed to dns1.registrar-servers[.]com and dns2.registrar-servers[.]com from ainsley[.]ns[.]cloudflare[.]com and neil[.]ns[.]cloudflare[.]com.
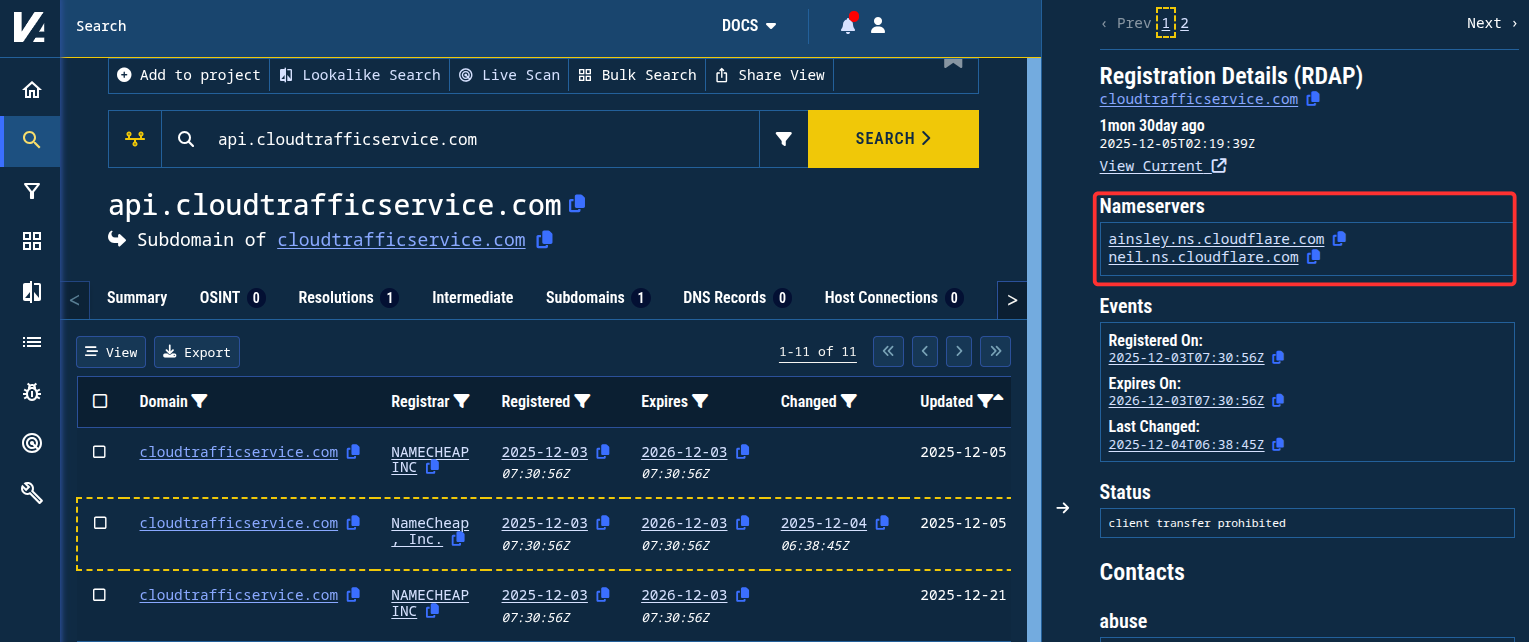
Figure 10. Registration details as they were captured shortly before the registration records were updated and the name servers modified.
Host Response Pivots
For a brief window, the initial download IP 95.179.213[.]0 responded with “HTTP/1.1 200 OK” and a 23 B response (“Service is unavailable.” / SHA1 23ce73454ebf289b2c25c3885887ac3d6055fa63). That exact response is relatively rare within Validin, but combined with the host header hash from the confirmed C2 (f400115bf3326edba086), we can build a query that reveals exactly one other IP address hosted on the same ASN, AS 20473 / AS-CHOOPA (Vultr): 45.32.144[.]255.
This new IP address, 45.32.144[.]255, was active in that configuration from September 28, 2025 until October 12, 2025, meaning its activity immediately preceded that of the known malicious IP address 95.179.213[.]0.
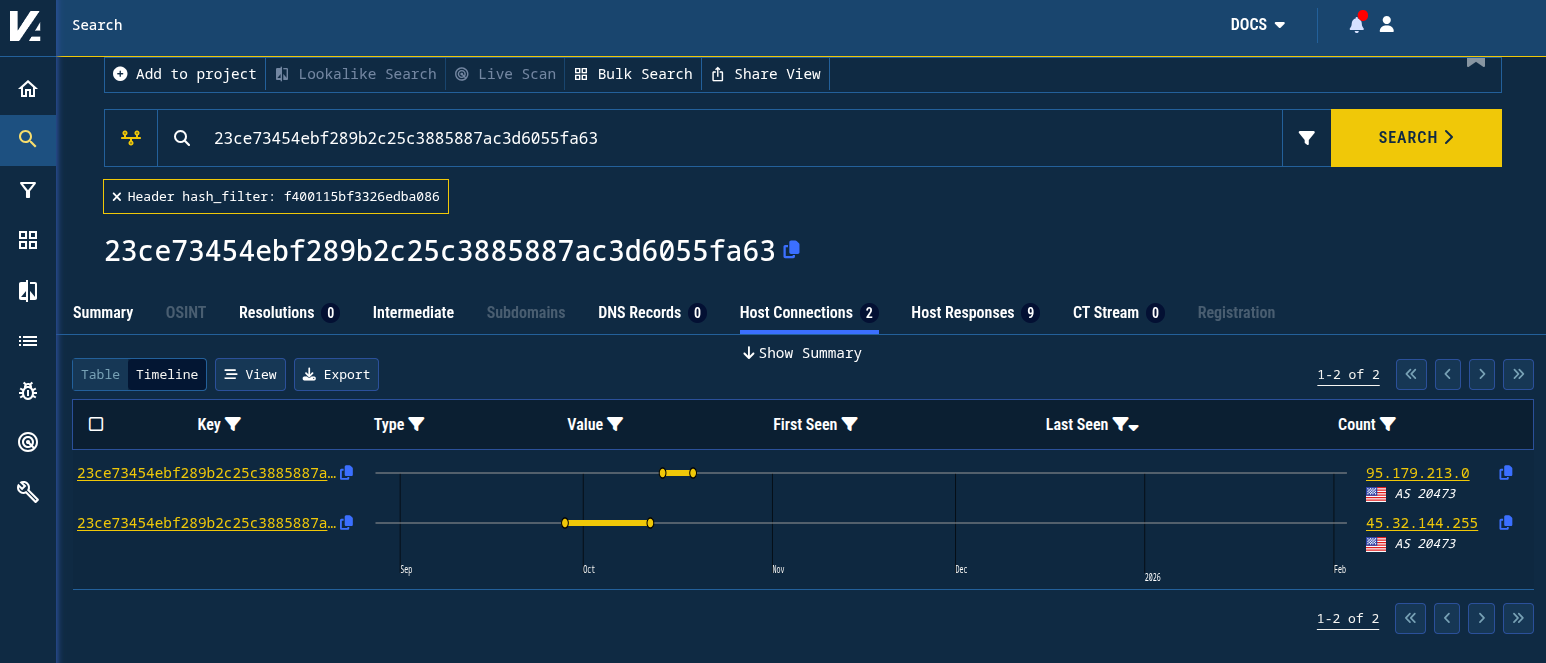
Figure 11. Finding another IP address behaving the exact same way as the confirmed malicious download IP address.
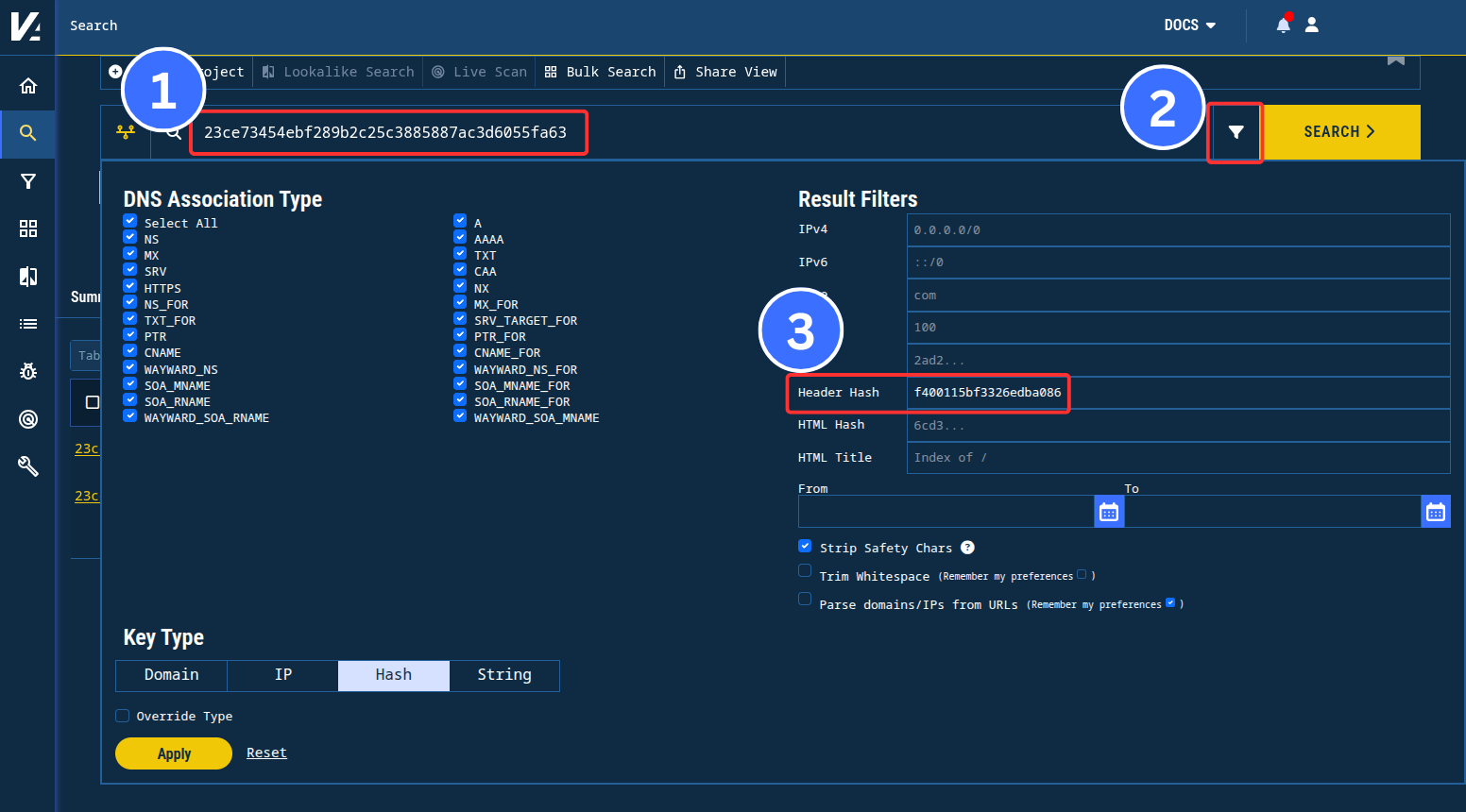
Figure 12. Community users can replicate these results in Validin by applying the header hash filter f400115bf3326edba086 with the primary search key 23ce73454ebf289b2c25c3885887ac3d6055fa63.
Conclusion
Through Validin’s persistent and rapid scanning, we were able to uncover several more indicators related to this incident. A potential C2 domain and IP discovered through a brief DNS history connection and an additional CS Beacon IP through our certificate data. Significantly, some of the infrastructure is still active as of writing this blog.
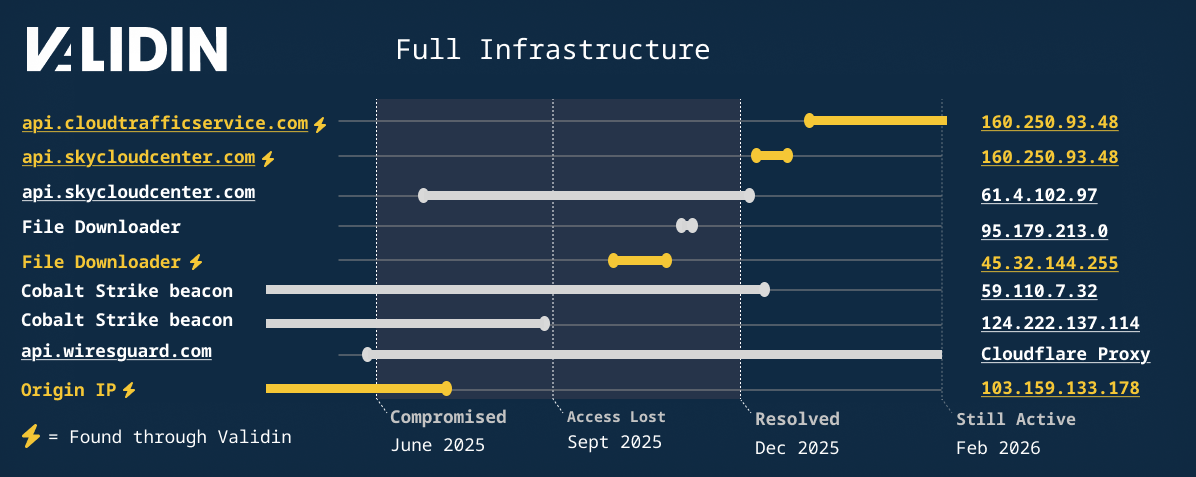
Figure 13. A reconstructed timeline showing additional indicators captured by Validin.
Indicators
45.32.144[.]255 - possible malicious download IP, active 2025-09-28 through 2025-10-12
160.250.93[.]48 - IP used by C2 domains api.skycloudcenter[.]com and api.cloudtrafficservice[.]com starting 2025-12-04
cloudtrafficservice[.]com
api[.]cloudtrafficservice[.]com - C2 domain active since 2025-12-03
103.159.133[.]178 - possible origin IP for Cobalt Strike beacon domain wiresguard[.]com
